12 min to read
TLS Handshake and Certificate Architecture - A Deep Dive into HTTPS Security
Understanding the cryptographic foundation of modern web security
Overview
Every time you see that green padlock icon in your browser, a sophisticated cryptographic dance has just occurred behind the scenes. This dance is called the TLS Handshake, and it’s the foundation of secure web communication.
In our interconnected world, billions of HTTPS connections are established daily, protecting everything from casual web browsing to critical financial transactions. Yet despite its ubiquity, the inner workings of TLS (Transport Layer Security) remain mysterious to many developers and system administrators.
This comprehensive guide answers fundamental questions about web security: How does TLS establish trust between strangers on the internet? What happens during those crucial milliseconds of connection establishment? How do digital certificates prove identity in a trustless network?
We’ll explore the intricate mechanics of TLS handshakes, dissect certificate structures, examine the global PKI infrastructure, and provide practical insights for implementing and troubleshooting TLS in production environments.
HTTPS and TLS: The Security Foundation
HTTPS is fundamentally HTTP wrapped in a TLS security layer. This simple concept revolutionized web security by providing three critical guarantees: encryption (confidentiality), authentication (identity verification), and integrity (tamper detection).
HTTP vs HTTPS: The fundamental difference in security postures
Without TLS, network communication resembles sending postcards through the mail system—anyone along the path can read, modify, or intercept your messages. TLS transforms this into a secure, tamper-evident envelope system where only the intended recipient can access the contents.
The TLS Handshake Protocol
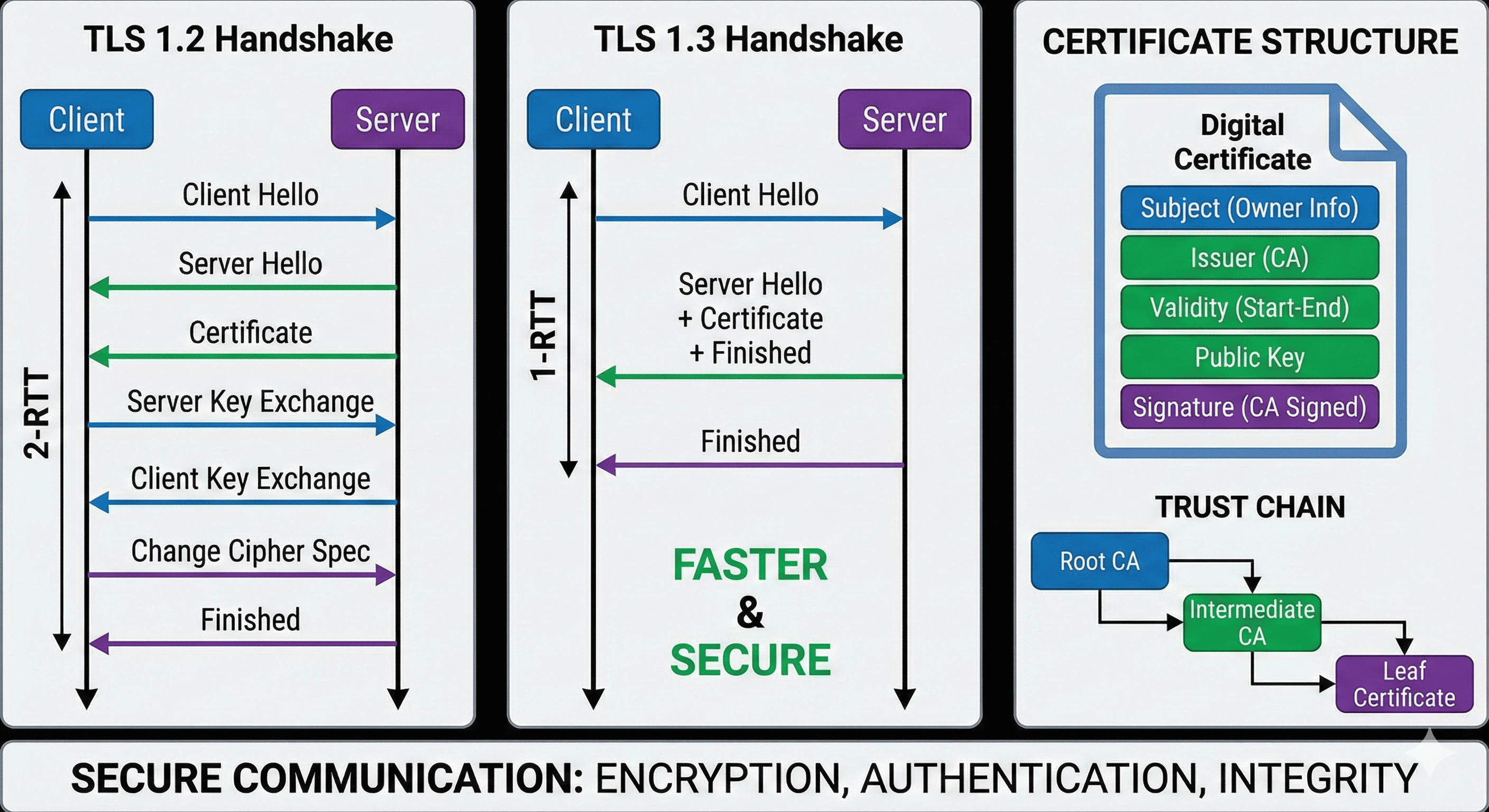
The TLS handshake is a carefully orchestrated negotiation process that establishes secure communication parameters between client and server. This process must be both secure and efficient, as it occurs before every HTTPS session.
TLS 1.2 Handshake Flow: A detailed view of the negotiation process
Handshake Phases Explained
Phase 1: Hello Exchange
The client announces its capabilities (supported TLS versions, cipher suites, compression methods) and provides a random number for entropy. The server responds with its selected configuration and its own random number.
Phase 2: Authentication
The server presents its certificate chain to prove its identity. This chain must trace back to a trusted Certificate Authority (CA) that the client recognizes.
Phase 3: Key Exchange
Both parties collaborate to generate a shared secret (Master Secret) without transmitting it directly. This uses asymmetric cryptography to securely establish symmetric keys.
Phase 4: Activation
Both sides confirm they’re ready to begin encrypted communication and verify that the handshake completed successfully.
TLS Evolution: 1.2 vs 1.3 Comparison
TLS 1.3, standardized in 2018, represents a significant leap forward in both security and performance. Understanding these differences is crucial for modern system design.
| Aspect | TLS 1.2 | TLS 1.3 | Impact |
|---|---|---|---|
| Handshake Rounds | 2-3 RTT | 1 RTT (0-RTT with resumption) | 50%+ latency reduction |
| Cipher Suites | 300+ combinations | 5 secure combinations | Eliminates weak crypto |
| Perfect Forward Secrecy | Optional | Mandatory | Enhanced privacy protection |
| Handshake Encryption | Partial | Nearly complete | Metadata protection |
| Vulnerabilities | CRIME, BEAST, POODLE | Resistant to known attacks | Improved security posture |
TLS 1.3 (green) vs TLS 1.2 (orange): Simplified handshake reduces latency
Digital Certificate Architecture
Digital certificates are the linchpin of TLS security, providing cryptographic proof of identity in an environment where participants have never met. Understanding certificate structure is essential for troubleshooting and security analysis.
Certificate Anatomy
| Field | Purpose | Example |
|---|---|---|
| Version | X.509 certificate version | v3 (most common) |
| Serial Number | Unique identifier within CA | 0x1a2b3c4d5e6f |
| Signature Algorithm | Cryptographic algorithm used | SHA256withRSA |
| Issuer | Certificate Authority information | CN=Let's Encrypt Authority X3 |
| Validity Period | Certificate lifespan | Not Before: 2026-01-01 Not After: 2026-04-01 |
| Subject | Certificate owner identity | CN=api.example.com |
| Public Key | Cryptographic public key | 2048-bit RSA or 256-bit ECDSA |
| Extensions | Additional constraints/features | SAN, Key Usage, OCSP URLs |
| Signature | CA's cryptographic signature | Base64-encoded signature blob |
Subject Alternative Names (SAN)
Modern certificates extensively use SAN extensions to cover multiple domains and subdomains within a single certificate. This approach improves both cost efficiency and management complexity.
Subject Alternative Name:
DNS:example.com
DNS:www.example.com
DNS:api.example.com
DNS:*.staging.example.com
DNS:admin.example.com
Public Key Infrastructure (PKI) and Trust Models
PKI provides the framework for establishing trust in a distributed environment. The hierarchical trust model used by web browsers relies on a carefully maintained ecosystem of Certificate Authorities.
Self-Signed
Stored in Browser/OS] --> INT1[Intermediate CA 1
Signed by Root] ROOT --> INT2[Intermediate CA 2
Signed by Root] INT1 --> LEAF1[Server Certificate
api.example.com] INT1 --> LEAF2[Server Certificate
app.company.com] INT2 --> LEAF3[Server Certificate
secure.bank.com] INT2 --> LEAF4[Server Certificate
shop.retailer.com] style ROOT fill:#ff6b9d,stroke:#333,stroke-width:3px style INT1 fill:#4ecdc4,stroke:#333,stroke-width:2px style INT2 fill:#4ecdc4,stroke:#333,stroke-width:2px style LEAF1 fill:#95e1d3,stroke:#333,stroke-width:1px style LEAF2 fill:#95e1d3,stroke:#333,stroke-width:1px style LEAF3 fill:#95e1d3,stroke:#333,stroke-width:1px style LEAF4 fill:#95e1d3,stroke:#333,stroke-width:1px
PKI Hierarchy: Chain of trust from root CA to end-entity certificates
Certificate Chain Validation Process
When a client receives a server certificate, it performs a rigorous validation process:
- Chain Construction: Build the complete certificate chain from server certificate to trusted root
- Signature Verification: Verify each certificate’s signature using the issuer’s public key
- Validity Checking: Ensure all certificates are within their validity periods
- Revocation Status: Check if any certificate has been revoked (via CRL or OCSP)
- Policy Constraints: Verify certificate usage constraints and extensions
- Hostname Verification: Confirm the certificate matches the requested hostname
Certificate Lifecycle Management
Modern web applications require sophisticated certificate management to maintain security and availability. Understanding the certificate lifecycle is crucial for operational excellence.
Automated Certificate Management
The rise of Let’s Encrypt and ACME protocol has revolutionized certificate management, enabling automated issuance and renewal.
Automated Certificate Lifecycle: ACME protocol enables hands-off management
Critical Considerations for Production
Certificate Monitoring: Implement automated monitoring for certificate expiration, chain validity, and revocation status.
Graceful Renewal: Plan renewal windows well before expiration (typically 30 days) to account for potential failures.
Multiple Validation Methods: Support both HTTP-01 and DNS-01 ACME challenges for maximum flexibility.
Backup Strategies: Maintain backup certificates and alternative CAs to prevent service interruption.
Security Practices: Protect private keys with HSMs or secure key management systems for high-value applications.
Common TLS Implementation Challenges
Real-world TLS deployment involves numerous pitfalls that can compromise security or availability. Understanding these challenges helps prevent costly mistakes.
Certificate Validation Errors
| Error Type | Browser Message | Root Cause | Resolution |
|---|---|---|---|
| Expired Certificate | NET::ERR_CERT_DATE_INVALID | Certificate past validity period | Renew certificate immediately |
| Untrusted CA | NET::ERR_CERT_AUTHORITY_INVALID | CA not in browser trust store | Use publicly trusted CA |
| Hostname Mismatch | NET::ERR_CERT_COMMON_NAME_INVALID | Certificate doesn't match domain | Add domain to SAN or get new cert |
| Incomplete Chain | NET::ERR_CERT_UNABLE_TO_CHECK_REVOCATION | Missing intermediate certificates | Install complete certificate chain |
| Revoked Certificate | NET::ERR_CERT_REVOKED | Certificate revoked by CA | Obtain new certificate |
Performance Optimization Strategies
TLS Session Resumption: Implement session tickets or session IDs to avoid full handshakes for returning clients.
OCSP Stapling: Cache OCSP responses at the server to reduce client-side validation latency.
Certificate Compression: Use certificate compression in TLS 1.3 to reduce handshake overhead.
Cipher Suite Optimization: Prefer ECDSA certificates and modern cipher suites for better performance.
Practical TLS Troubleshooting
Effective TLS troubleshooting requires understanding both the protocol mechanics and the tools available for diagnosis.
Essential Diagnostic Commands
# Test TLS connection and view certificate details
openssl s_client -connect example.com:443 -servername example.com
# Analyze certificate file
openssl x509 -in certificate.pem -text -noout
# Check certificate chain
openssl s_client -connect example.com:443 -showcerts
# Test specific TLS version
openssl s_client -connect example.com:443 -tls1_3
# Check certificate expiration
openssl x509 -in certificate.pem -noout -dates
# Verify certificate against private key
openssl x509 -in certificate.pem -noout -modulus | openssl md5
openssl rsa -in private.key -noout -modulus | openssl md5
Advanced Debugging Techniques
Packet Capture Analysis: Use Wireshark to analyze TLS handshake packets and identify protocol-level issues.
SSL Labs Testing: Leverage the SSL Server Test to identify configuration weaknesses and compatibility issues.
Certificate Transparency Monitoring: Monitor CT logs to detect unauthorized certificate issuance for your domains.
HSTS and Security Headers: Implement proper security headers to prevent downgrade attacks and improve security posture.
Security Best Practices
Modern TLS deployment requires attention to numerous security considerations beyond basic certificate installation.
Configuration Hardening
# Example Nginx TLS configuration
ssl_protocols TLSv1.2 TLSv1.3;
ssl_ciphers ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384;
ssl_prefer_server_ciphers off;
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 10m;
ssl_stapling on;
ssl_stapling_verify on;
# Security headers
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains" always;
add_header X-Frame-Options DENY always;
add_header X-Content-Type-Options nosniff always;
Monitoring and Alerting
Implement comprehensive monitoring for certificate health:
- Certificate expiration alerts (30, 14, 7, and 1 day warnings)
- Certificate chain validation monitoring
- TLS protocol version usage analytics
- Cipher suite adoption tracking
- Certificate transparency log monitoring
The Future of TLS
TLS continues to evolve in response to emerging threats and technological advances. Understanding future directions helps inform long-term security strategies.
Post-Quantum Cryptography
The advent of quantum computing poses a significant threat to current cryptographic systems. NIST has standardized post-quantum algorithms that will eventually replace current public key systems:
- CRYSTALS-Kyber: Key encapsulation mechanism
- CRYSTALS-Dilithium: Digital signature algorithm
- FALCON: Alternative signature algorithm for constrained environments
TLS 1.4 and Beyond
Future TLS versions will likely focus on:
- Enhanced post-quantum readiness
- Improved privacy protection
- Reduced latency for mobile networks
- Better support for IoT and edge computing
Conclusion
TLS and the PKI ecosystem represent one of the most successful large-scale cryptographic deployments in history. From humble beginnings as SSL for securing credit card transactions, TLS has evolved into the foundation of internet security.
Understanding TLS handshakes and certificate management is no longer optional knowledge for software engineers and system administrators. These protocols underpin critical business operations, and their proper implementation directly impacts user trust, regulatory compliance, and business continuity.
The complexity of modern TLS deployment—from automated certificate management to performance optimization—requires a deep understanding of both cryptographic principles and operational practices. As threats evolve and new technologies emerge, this knowledge becomes even more valuable.
By mastering these concepts, you’re not just implementing security features; you’re participating in the global infrastructure that makes secure digital communication possible for billions of people worldwide.


Comments