2 min to read
ArgoCD Ingress Error Resolution Guide (GKE)
Resolving 502 Server Error and LoadBalancer Health Check Failures in GKE ArgoCD Ingress Configuration
Overview
This article addresses the 502 Server Error and LoadBalancer Health Check failures that occur when configuring ArgoCD Ingress in GKE (Google Kubernetes Engine) environment.
Google Cloud Load Balancer distributes traffic through health checks of backend services, but when configuring ArgoCD Ingress, internal HTTP → HTTPS redirection can cause health check failures, preventing external access to the ArgoCD UI.
Troubleshooting Flow
Troubleshooting Steps:
- Analyze 502 errors in GKE LoadBalancer and ArgoCD Ingress configuration
- Verify redirection through internal curl testing (Temporary Redirect)
- Configure
--insecuresetting throughargocd-cmd-params-cmConfigMap - Verify health check recovery and ArgoCD UI exposure
ArgoCD Ingress Error (With GKE)
When checking the LoadBalancer’s backend service, Server Error occurs due to failed Health Checks in the regional network endpoint groups (equivalent to AWS Target Groups).
Error Verification
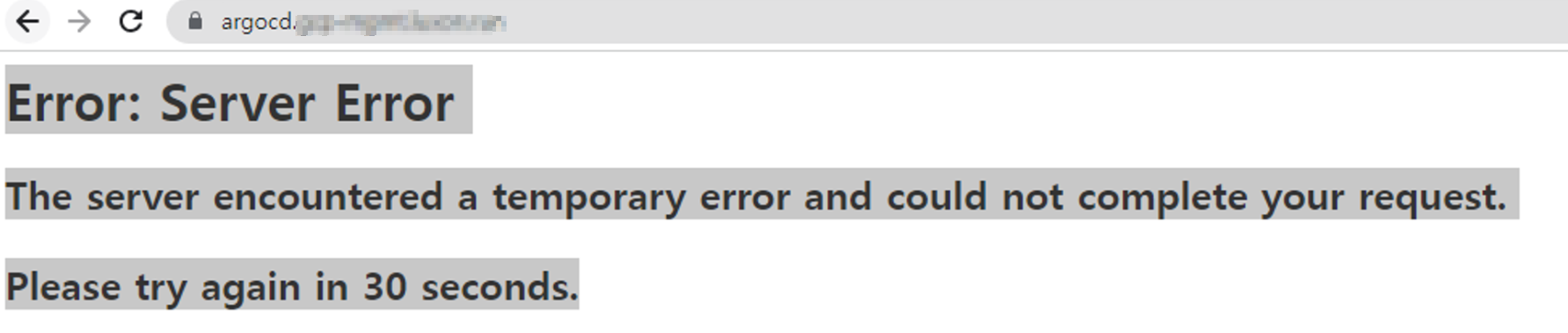
External Access Test:
$ curl https://argocd.somaz.link/healthz
Response:
Internal Testing
Kubernetes Internal curl Test:
kubectl run curl -it --rm --image curlimages/curl -- sh
curl 10.31.0.134:8080/healthz
# Temporary Redirect
Problem Resolution
According to the ArgoCD Ingress documentation, the API server must be run with TLS disabled to prevent internal redirection loops from HTTP to HTTPS.
ConfigMap Modification
argocd-cmd-params-cm ConfigMap Configuration:
apiVersion: v1
data:
redis.server: argocd-redis-ha-haproxy:6379
server.insecure: "true"
kind: ConfigMap
metadata:
labels:
app.kubernetes.io/name: argocd-cmd-params-cm
app.kubernetes.io/part-of: argocd
name: argocd-cmd-params-cm
namespace: argocd
Resolution Results
- Health Check functioning normally
- ArgoCD UI properly exposed
- External access enabled
Key Points
This section summarizes the main considerations and solutions for exposing ArgoCD through Ingress in GKE.
Main Points
💡 Key Points Summary
- Problem Cause
- ArgoCD has HTTPS redirection enabled by default
- GKE Ingress requires internal HTTP communication for Health Checks
- Solution
- Set
server.insecuretotruein ConfigMap (argocd-cmd-params-cm) - Restart or rollout argocd-server after configuration
- Set
Conclusion
When exposing ArgoCD through Ingress in GKE, the internal TLS redirection in ArgoCD can cause GCP LoadBalancer health checks to fail.
By setting server.insecure: "true" in ArgoCD, internal TLS can be disabled, allowing GCP LoadBalancer to pass health checks and properly serve the ArgoCD UI through the Ingress path.


Comments