4 min to read
Deep Dive into Zero Trust Security Model
Understanding the Never Trust, Always Verify Approach
Understanding Zero Trust Security Model
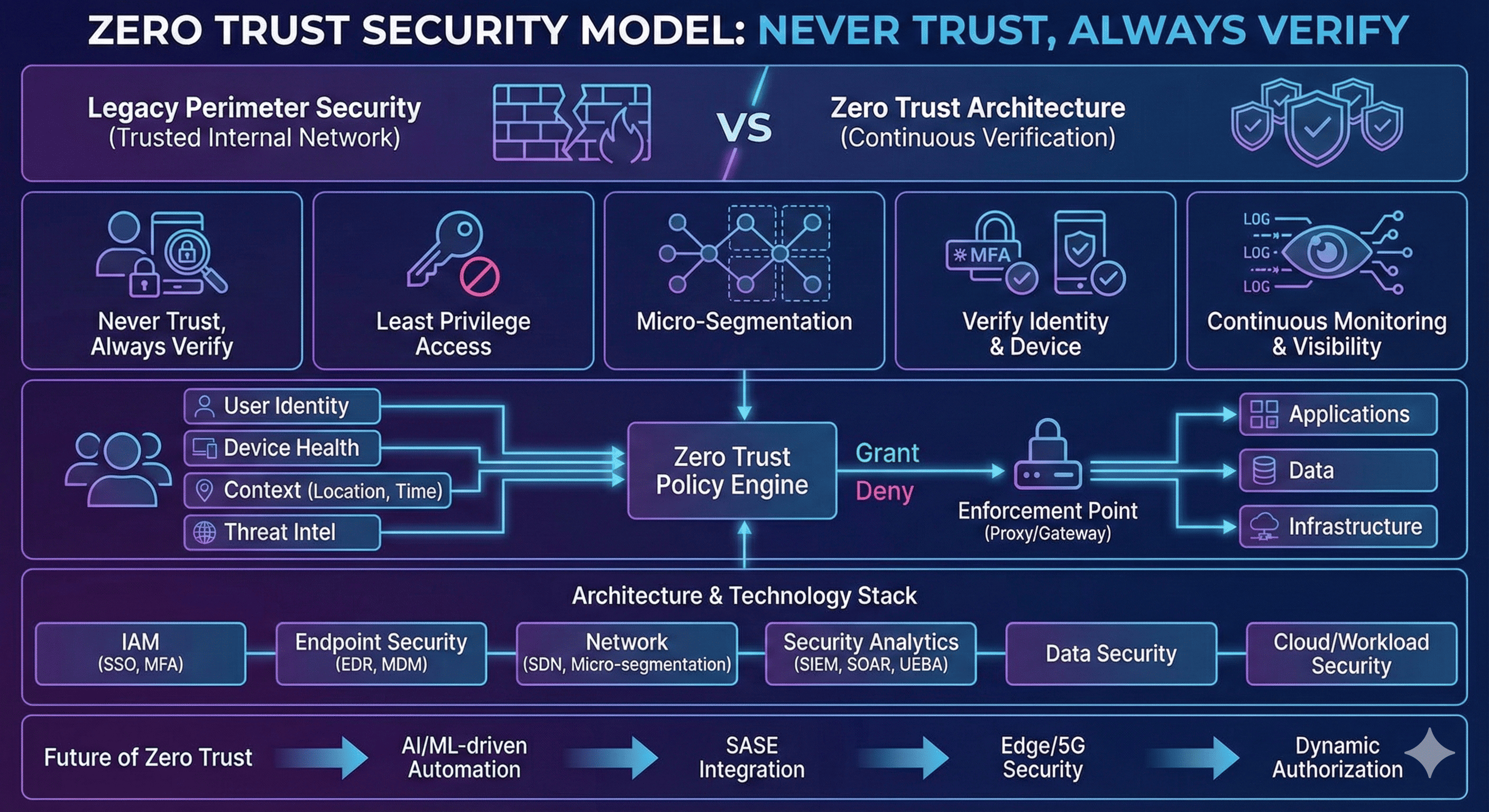
Zero Trust is a modern security model based on the principle of “never trust, always verify.” It challenges the traditional perimeter-based security approach by assuming that no user, device, or network should be inherently trusted, regardless of their location or previous authentication.
What is Zero Trust?
The Security Paradigm Shift
Zero Trust represents a fundamental shift in security philosophy:
- No Implicit Trust: Every access request is verified, regardless of source
- Continuous Validation: Trust is never granted permanently
- Least Privilege: Access is granted on a need-to-know basis
- Micro-segmentation: Network is divided into smaller, isolated segments
This approach addresses modern security challenges posed by cloud computing, remote work, and sophisticated cyber threats.
Zero Trust Model Overview (Diagram Description)
- Zero Trust Model
- Core Principles: Never Trust, Always Verify, Least Privilege
- Components: Identity, Device, Network
- Implementation: Assessment, Planning, Deployment
- Benefits: Enhanced Security, Better Control, Improved Visibility
Core Principles and Components
Zero Trust architecture is built on several key principles and components that work together to create a comprehensive security framework. Understanding these elements is crucial for effective implementation.
Core Principles
| Principle | Description | Implementation |
|---|---|---|
| Never Trust | No implicit trust granted |
|
| Least Privilege | Minimum access required |
|
| Micro-segmentation | Network isolation |
|
Key Components
Essential Components
Zero Trust implementation requires several key components:
- Identity and Access Management (IAM): SSO, MFA, RBAC
- Device Security: Endpoint protection, MDM, device health checks
- Network Security: Micro-segmentation, SDN, VPN alternatives
- Data Protection: Encryption, DLP, data classification
- Visibility and Analytics: SIEM, UEBA, security analytics
These components work together to create a comprehensive security framework.
Implementation Strategy
Implementing Zero Trust requires a strategic approach that considers organizational needs, existing infrastructure, and security requirements. A phased implementation helps ensure successful adoption.
Implementation Phases
| Phase | Description | Key Activities |
|---|---|---|
| Assessment | Evaluate current state |
|
| Planning | Develop implementation strategy |
|
| Deployment | Implement solutions |
|
Best Practices
Implementation Best Practices
- Start Small: Begin with critical assets and expand gradually
- User Experience: Balance security with usability
- Continuous Monitoring: Implement comprehensive logging and analysis
- Regular Reviews: Assess and update security policies
- Training: Educate users and administrators
These practices help ensure successful Zero Trust implementation.
Use Cases and Examples
Zero Trust can be applied across various environments and scenarios. Here are some common use cases and implementation examples.
Common Use Cases
| Environment | Implementation | Benefits |
|---|---|---|
| Cloud |
|
|
| Kubernetes |
|
|
| Enterprise |
|
|
Implementation Considerations
Key Considerations
- Legacy Systems: Compatibility with existing infrastructure
- User Experience: Impact on productivity and usability
- Cost: Investment in new technologies and training
- Compliance: Meeting regulatory requirements
- Integration: Working with existing security tools
These considerations help ensure successful implementation.
Key Points
-
Core Principles
- Never trust, always verify
- Least privilege access
- Micro-segmentation
- Continuous monitoring -
Key Components
- Identity management
- Device security
- Network protection
- Data security -
Implementation
- Phased approach
- User experience
- Continuous improvement
- Regular assessment

Comments