13 min to read
Mastering SSH Tunneling for Secure Remote Access
A comprehensive guide to SSH tunneling techniques and real-world applications
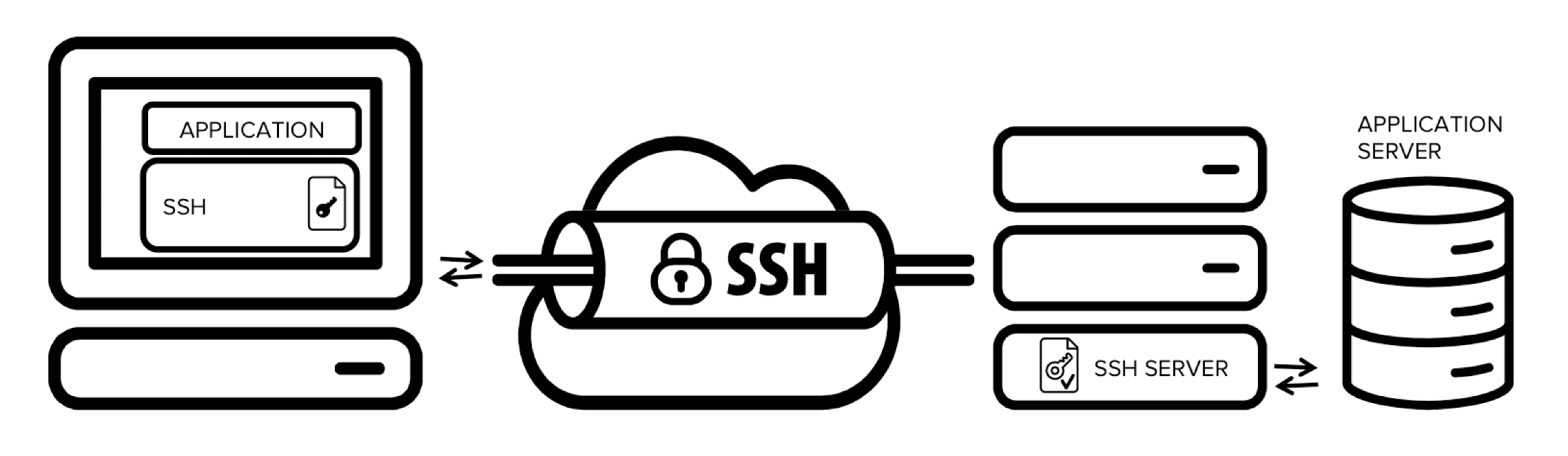
Understanding SSH Tunneling
SSH tunneling is a powerful technique that leverages secure SSH connections to encrypt network traffic between systems. It allows you to securely access services on remote servers, bypass network restrictions, and protect sensitive data in transit.
What is SSH Tunneling?
SSH Tunneling Basics
SSH tunneling (also called SSH port forwarding) creates an encrypted channel through an SSH connection to transfer data securely. This technique can:
- Provide secure access to services behind firewalls
- Encrypt traffic that would otherwise be transmitted in plaintext
- Allow access to internal network resources from external locations
- Bypass network restrictions in controlled environments
SSH tunneling is an essential skill for system administrators, developers, and security professionals.
Three Types of SSH Tunneling
| Tunneling Type | Purpose |
|---|---|
| Local Port Forwarding | Forward traffic from a port on your local machine to a port on a remote server |
| Remote Port Forwarding | Forward traffic from a port on the remote server to a port on your local machine |
| Dynamic Port Forwarding | Create a SOCKS proxy for routing various types of traffic through an SSH tunnel |
Diagram Description:
- SSH Tunneling branches into Local Port Forwarding (Local → Remote Service), Remote Port Forwarding (Remote → Local Service), and Dynamic Port Forwarding (SOCKS Proxy).
Local Port Forwarding
Local port forwarding is the most common type of SSH tunneling. It allows you to forward traffic from a port on your local machine to a port on a remote server, potentially reaching services that are not directly accessible.
Basic Syntax
ssh -L [local_port]:[destination_host]:[destination_port] [username]@[ssh_server]
Parameter Explanation:
local_port: The port on your local machine to listen ondestination_host: The server you want to reach (from the SSH server’s perspective)destination_port: The port on the destination host to connect tousername@ssh_server: SSH server that will relay the connection
Practical Example
# Access a remote web server through SSH tunnel
ssh -L 8080:localhost:80 user@example.com
Use Cases for Local Port Forwarding
| Scenario | Example Command |
|---|---|
| Accessing a database server | ssh -L 3306:database-server:3306 user@jump-server |
| Accessing internal web applications | ssh -L 8080:internal-app:8080 user@bastion-host |
| Securely browsing via a remote server | ssh -L 8080:www.example.com:80 user@ssh-server |
Remote Port Forwarding
Remote port forwarding is the reverse of local forwarding. It allows you to expose a local service to a remote server, making it accessible via a port on the remote machine. This is particularly useful for sharing local development environments or services behind NAT.
Basic Syntax
ssh -R [remote_port]:[local_host]:[local_port] [username]@[ssh_server]
Parameter Explanation:
remote_port: The port on the remote SSH server to listen onlocal_host: The local machine or service to forward to (usually localhost)local_port: The port of your local serviceusername@ssh_server: SSH server that will relay the connection
Practical Example
# Share a local development web server with a remote server
ssh -R 9000:localhost:3000 user@example.com
Use Cases for Remote Port Forwarding
| Scenario | Example Command |
|---|---|
| Sharing local development server | ssh -R 8000:localhost:3000 user@public-server |
| Remote support access | ssh -R 2222:localhost:22 user@support-server |
| Exposing local API to remote services | ssh -R 5000:localhost:5000 user@integration-server |
Dynamic Port Forwarding
Dynamic port forwarding creates a SOCKS proxy that can route different types of traffic through an SSH tunnel. This is extremely useful for securely browsing the web or accessing multiple services through a single tunnel.
Basic Syntax
ssh -D [local_socks_port] [username]@[ssh_server]
Parameter Explanation:
local_socks_port: The port on your local machine for the SOCKS proxyusername@ssh_server: SSH server that will relay connections
Practical Example
# Create a SOCKS proxy on port 1080
ssh -D 1080 user@example.com
localhost:1080| B[SSH Client] B -->|Encrypted SSH| C[SSH Server] C --> D[Website 1] C --> E[Website 2] C --> F[Website 3] style A stroke:#333,stroke-width:1px,fill:#f5f5f5 style B stroke:#333,stroke-width:1px,fill:#a5d6a7 style C stroke:#333,stroke-width:1px,fill:#64b5f6 style D stroke:#333,stroke-width:1px,fill:#ffcc80 style E stroke:#333,stroke-width:1px,fill:#ffcc80 style F stroke:#333,stroke-width:1px,fill:#ffcc80
Use Cases for Dynamic Port Forwarding
- Secure browsing on public Wi-Fi
- Bypassing geo-restrictions
- Accessing multiple internal services
- Debugging network applications
Advanced Techniques for Production Environments
In production environments, you often need more robust SSH tunneling solutions that stay running, auto-reconnect, and persist across system reboots. Let’s explore some advanced techniques for real-world applications.
Setting Up Persistent Tunnels
Common SSH Tunnel Options:
-f: Run SSH in the background-N: Do not execute a remote command (tunnel only)-C: Compress data for better performance-q: Quiet mode-T: Disable pseudo-terminal allocation
Example: Redis Access via SSH Tunnel
Create a background tunnel to Redis, allowing connections from any IP to the local machine
ssh -fN -L 0.0.0.0:6395:redis-server.example.com:6379 user@jumphost
Security Warning:
Using 0.0.0.0 binds the port to all interfaces. For better security:
- Use
127.0.0.1to restrict to localhost - Implement firewall rules
- Use key-based authentication
- Consider jump hosts for sensitive environments
Creating Systemd Services for Persistent Tunnels
For production environments, it’s crucial to ensure that your SSH tunnels start automatically on system boot and restart if they fail. Using systemd services is an excellent way to achieve this.
Step 1: Create Tunnel Script
#!/bin/bash
# Redis tunnel script
/usr/bin/ssh -N -i /home/ec2-user/.ssh/id_rsa -L 0.0.0.0:6395:redis-endpoint.example.com:6379 ec2-user@10.33.1.252 &
# Add more tunnels as needed
/usr/bin/ssh -N -i /home/ec2-user/.ssh/id_rsa -L 0.0.0.0:3336:mysql-endpoint.example.com:3306 ec2-user@10.33.1.252 &
wait
Step 2: Create Systemd Service File
# /etc/systemd/system/ssh-tunnels.service
[Unit]
Description=SSH Tunnels for Database Access
After=network.target
[Service]
User=ec2-user
ExecStart=/usr/local/bin/ssh-tunnels.sh
Restart=always
RestartSec=5
[Install]
WantedBy=multi-user.target
Step 3: Enable and Start the Service
# Set executable permissions
sudo chmod +x /usr/local/bin/ssh-tunnels.sh
# Reload systemd configuration
sudo systemctl daemon-reload
# Enable and start the service
sudo systemctl enable ssh-tunnels.service
sudo systemctl start ssh-tunnels.service
# Check status
sudo systemctl status ssh-tunnels.service
Service Management Commands:
sudo systemctl start ssh-tunnels.service: Start the servicesudo systemctl stop ssh-tunnels.service: Stop the servicesudo systemctl restart ssh-tunnels.service: Restart the servicesudo systemctl status ssh-tunnels.service: Check statussudo journalctl -u ssh-tunnels.service: View logs
SSH Tunnel Security Best Practices
When implementing SSH tunneling in production environments, security should be a primary concern. The following best practices will help ensure your tunnels remain secure and reliable.
Authentication and Access Control
| Best Practice | Implementation |
|---|---|
| Use SSH Keys | Always prefer SSH key authentication over passwords. Disable password authentication when possible. |
| Restrict SSH Users | Create dedicated users for tunneling with restricted shell access (/bin/false or /usr/sbin/nologin). |
| Implement Jump Hosts | Use dedicated jump servers as intermediaries between untrusted and trusted networks. |
| Limit SSH Access | Configure firewall rules to restrict SSH access to specific IP addresses or networks. |
Monitoring and Maintenance
- Log Review: Regularly check SSH logs
- Connection Auditing: Monitor active tunnels
- Key Rotation: Periodically rotate SSH keys
- Patching: Keep SSH software updated
- Alternative Paths: Have backup connection methods
Real-World Application Examples
Let’s examine some practical, real-world applications of SSH tunneling that demonstrate its versatility and utility in different scenarios.
Example 1: Secure Access to AWS ElastiCache
You need to access an AWS ElastiCache Redis instance only accessible from within a VPC.
# Create the tunnel
ssh -fN -L 6379:my-redis-cluster.abc123.amazonaws.com:6379 ec2-user@bastion-host.example.com
# Access Redis locally
redis-cli -h localhost -p 6379
Example 2: Secure Database Administration
# Create tunnel to MySQL database
ssh -L 3306:prod-db.internal:3306 user@jump-server.example.com
# Connect using local client
mysql -h 127.0.0.1 -u admin -p
Example 3: Accessing Internal Web Applications
You need to access internal monitoring dashboards or admin interfaces that are not exposed to the internet.
Solution: Set up local port forwarding to access the internal applications through a secure tunnel.
# Create tunnels for multiple internal services
ssh -L 8080:monitoring.internal:80 -L 8081:admin.internal:8080 user@jump-server.example.com
# Access in browser
# http://localhost:8080 (monitoring)
# http://localhost:8081 (admin interface)
Troubleshooting SSH Tunnels
When working with SSH tunnels, you may encounter various issues. Here are some common problems and their solutions to help you diagnose and fix tunneling problems.
Common Issues and Solutions
| Problem | Solution |
|---|---|
| Connection refused |
|
| Tunnel closes unexpectedly |
|
| Slow performance |
|
| Permission denied |
|
Debugging SSH Tunnels
- Verbose Mode: Add
-v,-vv, or-vvv - netstat/ss: Check listening ports (
netstat -tulnorss -tuln) - lsof: See which process is using a port (
lsof -i :port_number) - tcpdump: Capture network traffic
- telnet/nc: Test port reachability (
telnet host portornc -zv host port)
SSH Tunnel Alternatives
While SSH tunneling is versatile and widely available, there are other technologies that can accomplish similar goals, each with its own advantages and disadvantages.
| Alternative | Description | Best For |
|---|---|---|
| VPN | Creates an encrypted network connection, routing all or selected traffic through it. | Full network integration, multiple users, persistent connections |
| Reverse Proxies | Servers that sit between clients and backend services, forwarding requests and responses. | Web applications, load balancing, TLS termination |
| Wireguard | Modern, fast VPN with simple setup and strong encryption. | Persistent connections, mobile devices, simpler than OpenVPN |
| Cloudflare Tunnel | Service that creates a secure tunnel between your service and Cloudflare's edge network. | Public-facing web services without opening firewall ports |
When to Use Alternatives:
- Multiple users need access
- Want to route all traffic, not just specific ports
- Need centralized management or scaling
- Require higher throughput or lower latency
- Have compliance requirements SSH can’t satisfy
Key Points and Best Practices
-
Tunnel Types
- Local forwarding: Access remote services locally (-L)
- Remote forwarding: Expose local services remotely (-R)
- Dynamic forwarding: Create a SOCKS proxy for flexible routing (-D) -
Security Considerations
- Always use SSH key authentication, not passwords
- Restrict listening interfaces when possible (127.0.0.1 vs 0.0.0.0)
- Implement proper firewalls and access controls
- Regularly audit and rotate SSH keys -
Production Deployment
- Use systemd services for persistence and automatic restarts
- Consider tools like autossh for better reliability
- Implement monitoring to detect tunnel failures
- Document tunnel configurations and purposes -
Performance Tuning
- Enable compression for better performance over slow links
- Consider multiplexing multiple services over a single SSH connection
- Set appropriate timeouts and keepalives
- Monitor bandwidth and latency


Comments