15 min to read
Deep Dive into OpenStack Barbican
Understanding OpenStack's Key Management Service
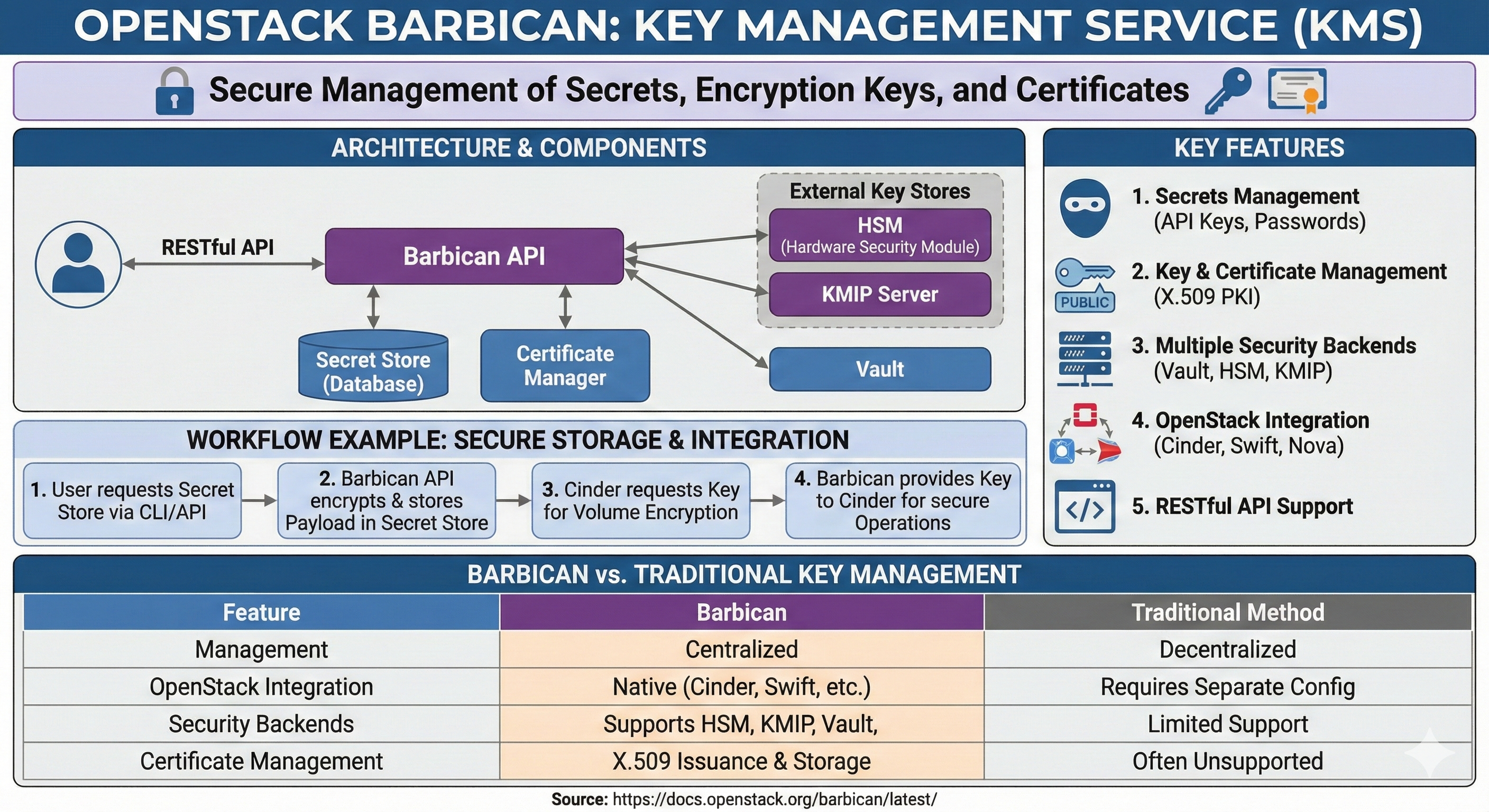
Understanding OpenStack Barbican
Barbican is OpenStack’s Key Management Service (KMS) that provides secure storage, provisioning, and management of secrets such as encryption keys, certificates, and passwords.
It serves as a central repository for sensitive data and enables secure integration with other OpenStack services.
What is Barbican?
The Key Management Service
Barbican serves as OpenStack’s security service, providing essential functionality:
- Secret Management: Secure storage of sensitive data including passwords, API keys, and binary data
- Key Management: Generation and lifecycle management of encryption keys with support for symmetric and asymmetric algorithms
- Certificate Management: PKI-based certificate handling with CA integration and automated renewal
- Service Integration: Seamless integration with other OpenStack services through standardized APIs
By providing centralized key management, Barbican enables secure data protection and compliance with security regulations in the cloud.
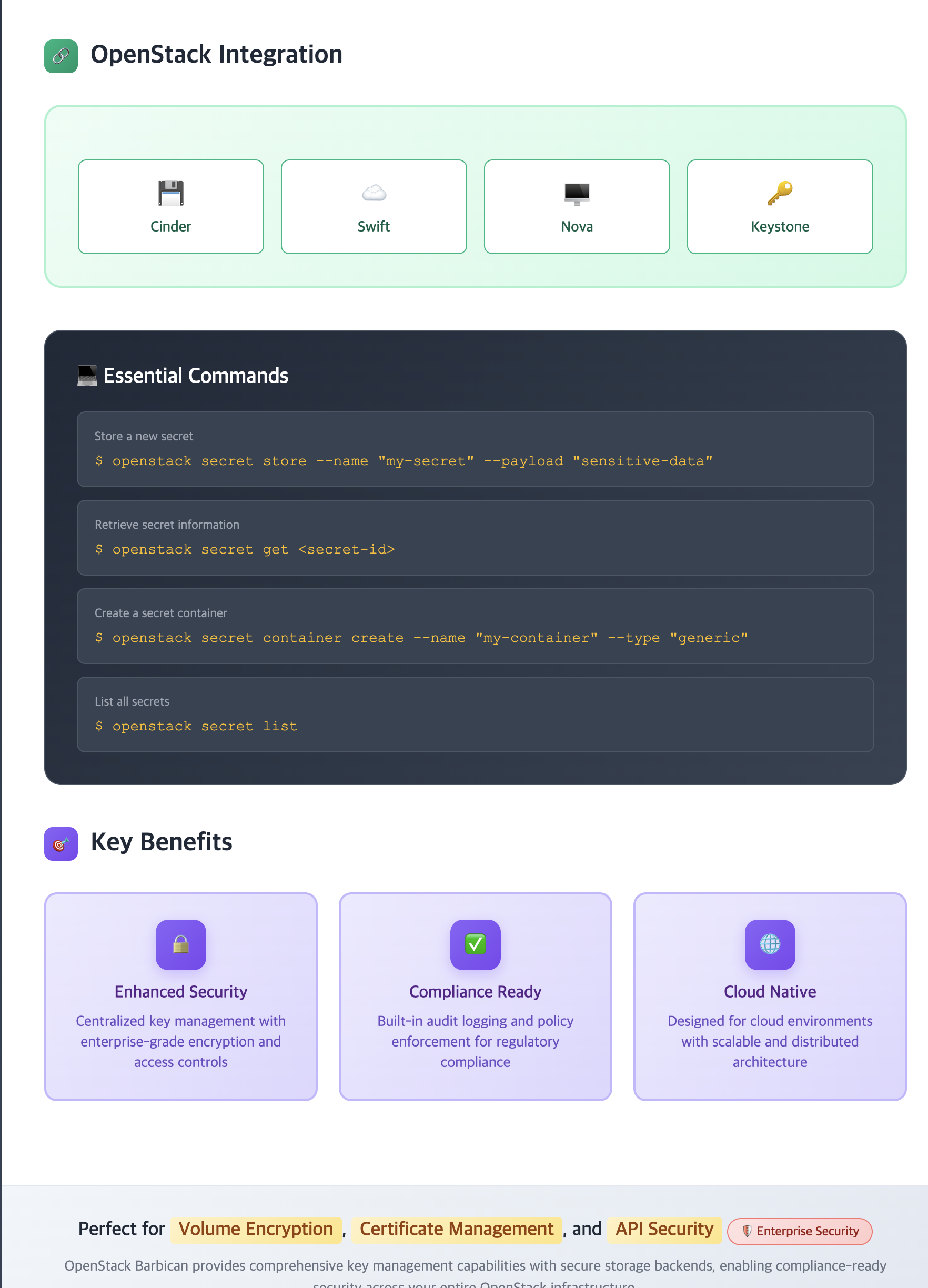
Why Use Barbican?
In modern cloud environments, security is paramount. Barbican addresses several critical challenges:
- Centralized Security: Eliminates scattered secret storage across services
- Compliance: Meets regulatory requirements like FIPS 140-2 and Common Criteria
- Scalability: Supports high-availability deployments with load balancing
- Audit Trail: Provides comprehensive logging for security audits
- Hardware Security: Integrates with HSMs for enhanced protection
Supported Secret Types
Barbican supports various types of secrets:
| Secret Type | Description | Use Cases |
|---|---|---|
| Symmetric Keys | AES encryption keys | Volume encryption, database encryption |
| Asymmetric Keys | RSA/ECC key pairs | SSL/TLS certificates, digital signatures |
| Passphrases | Text-based passwords | Database credentials, service passwords |
| Certificates | X.509 certificates | HTTPS endpoints, service authentication |
| Raw Binary | Arbitrary binary data | Custom encryption keys, tokens |
Barbican Architecture Overview (Diagram Description)
- Core Features: Secret Management, Key Management, Certificate Management
- Service Integration: Cinder, Swift, Nova
- Security: Encryption, Access Control, Audit Logging
- Storage: Secret Store, HSM, KMIP
Barbican Architecture and Components
Barbican’s architecture is designed to provide secure and flexible key management capabilities.
Each component plays a specific role in managing and protecting sensitive data.
Detailed Architecture
Barbican follows a modular architecture with clear separation of concerns:
Core Components
| Component | Role | Description |
|---|---|---|
| Barbican API | API Service |
|
| Barbican Worker | Processing Service |
|
| Secret Store | Storage Service |
|
| Certificate Manager | Certificate Service |
|
Storage Backend Options
Barbican supports multiple storage backends for different security requirements:
| Backend Type | Description | Use Cases |
|---|---|---|
| Simple Crypto | Default software-based encryption | Development, testing, basic production |
| HSM (PKCS#11) | Hardware Security Module integration | High-security environments, compliance |
| KMIP | Key Management Interoperability Protocol | Enterprise key management systems |
| HashiCorp Vault | External vault service integration | Multi-cloud, existing Vault deployments |
| Dogtag | Red Hat Certificate System | PKI-focused environments |
Service Integration
Barbican integrates seamlessly with several OpenStack services to provide comprehensive security:
| Service | Integration Type | Security Benefits |
|---|---|---|
| Cinder | Volume encryption key management |
|
| Swift | Object storage encryption |
|
| Nova | Instance and image encryption |
|
| Neutron | VPN and networking security |
|
| Octavia | Load balancer certificates |
|
This integration enables comprehensive security across the OpenStack ecosystem with centralized key management.
Key Features and Capabilities
Barbican provides comprehensive key management capabilities that enable secure data protection and compliance.
These features make it a powerful tool for security management in OpenStack environments.
Core Features
| Feature | Description | Benefits |
|---|---|---|
| Secret Management | Secure storage of sensitive data |
|
| Certificate Management | PKI-based certificate handling |
|
| Security Backends | Multiple storage options |
|
Best Practices
Key considerations for Barbican deployment and operation:
| Category | Best Practice | Implementation |
|---|---|---|
| Backend Selection | Choose appropriate storage backend |
|
| Access Control | Implement proper access policies |
|
| Key Rotation | Establish key rotation procedures |
|
| Audit Logging | Enable comprehensive logging |
|
| Backup Strategy | Implement secure backup procedures |
|
Security Considerations
Critical security aspects to consider:
- Encryption in Transit: All API communications use HTTPS/TLS
- Encryption at Rest: Secrets encrypted before storage
- Access Patterns: Monitor unusual access patterns
- Key Escrow: Implement proper key escrow procedures
- Compliance: Meet regulatory requirements (FIPS, Common Criteria)
These practices ensure secure and maintainable key management.
Implementation and Usage
Effective implementation of Barbican requires proper configuration and integration with other OpenStack services.
Here are key considerations and best practices for utilizing Barbican effectively.
Configuration and Setup
Basic Configuration
Key configuration files and settings:
# /etc/barbican/barbican.conf
[DEFAULT]
# API Configuration
bind_host = 0.0.0.0
bind_port = 9311
host_href = https://barbican.example.com:9311
# Database Configuration
sql_connection = mysql+pymysql://barbican:password@localhost/barbican
# Keystone Authentication
auth_strategy = keystone
[keystone_authtoken]
auth_url = https://keystone.example.com:5000/v3
auth_type = password
project_domain_name = default
user_domain_name = default
project_name = service
username = barbican
password = barbican_password
# Secret Store Configuration
[secretstore]
namespace = barbican.secretstore.plugins
enabled_secretstore_plugins = store_crypto
[crypto]
namespace = barbican.crypto.plugins
enabled_crypto_plugins = simple_crypto
HSM Integration Example
For high-security environments using Hardware Security Modules:
[secretstore]
enabled_secretstore_plugins = store_crypto
[crypto]
enabled_crypto_plugins = p11_crypto
[p11_crypto_plugin]
# Path to PKCS#11 library
library_path = /usr/lib/libpkcs11.so
# HSM login credentials
login = myuser
slot_id = 1
# Algorithm settings
encryption_algorithm = AES
encryption_mode = CBC
Common Operations
| Operation | Description | Command |
|---|---|---|
| Store Secret | Store a new secret with metadata | openstack secret store --name "db-password" --payload "supersecret123" --algorithm "aes" --bit-length 256 |
| Generate Key | Generate encryption key | openstack secret order create --name "volume-key" --algorithm "aes" --bit-length 256 |
| Get Secret | Retrieve secret payload | openstack secret get --payload <secret-id> |
| List Secrets | List all accessible secrets | openstack secret list --limit 10 |
| Update Secret | Update secret metadata | openstack secret update <secret-id> --name "new-name" |
| Delete Secret | Delete secret permanently | openstack secret delete <secret-id> |
| Create Container | Group related secrets | openstack secret container create --name "ssl-certs" --type "certificate" --secret "certificate=<cert-id>" --secret "private_key=<key-id>" |
Advanced Usage Examples
Certificate Management
Generate and manage SSL certificates:
Volume Encryption Integration
Use Barbican with Cinder for encrypted volumes:
API Usage Examples
Using REST API
Direct API calls for automation:
Python Client Usage
Programmatic access using Python:
from barbicanclient import client
from keystoneauth1.identity import v3
from keystoneauth1 import session
# Authentication
auth = v3.Password(
auth_url='https://keystone.example.com:5000/v3',
username='admin',
password='password',
project_name='admin',
user_domain_name='default',
project_domain_name='default'
)
sess = session.Session(auth=auth)
barbican = client.Client(session=sess)
# Store secret
secret = barbican.secrets.create(
name='database-password',
payload='supersecret123',
algorithm='aes',
bit_length=256
)
secret_ref = secret.store()
# Retrieve secret
stored_secret = barbican.secrets.get(secret_ref)
payload = stored_secret.payload
Use Cases
Barbican is particularly useful for:
| Use Case | Description | Benefits |
|---|---|---|
| Volume Encryption | Managing Cinder volume encryption keys |
|
| Object Storage | Securing Swift object storage |
|
| Load Balancer SSL | Managing SSL certificates for Octavia |
|
| Application Secrets | Storing application credentials |
|
| Compliance | Meeting regulatory requirements |
|
These use cases demonstrate Barbican’s flexibility and security capabilities across various scenarios.
Monitoring and Troubleshooting
Effective monitoring and troubleshooting are essential for maintaining a secure and reliable Barbican deployment.
Monitoring and Logging
Key Metrics to Monitor
| Metric Category | Key Metrics | Monitoring Tools |
|---|---|---|
| API Performance |
|
Prometheus, Grafana, OpenStack Telemetry |
| Security Events |
|
ELK Stack, Splunk, SIEM systems |
| System Health |
|
Nagios, Zabbix, OpenStack Health Monitor |
Log Analysis
Key log files and what to monitor:
# Barbican API logs
tail -f /var/log/barbican/barbican-api.log
# Barbican Worker logs
tail -f /var/log/barbican/barbican-worker.log
# Key log patterns to watch for:
# - Authentication failures
# - Secret access requests
# - Backend communication errors
# - Certificate expiration warnings
Common Issues and Solutions
Troubleshooting Guide
| Issue | Symptoms | Solution |
|---|---|---|
| Authentication Failures |
|
|
| Backend Connection Issues |
|
|
| Performance Issues |
|
|
Performance Tuning
Optimization strategies for production deployments:
- API Workers: Scale horizontally based on load
- Database Optimization: Tune MySQL/PostgreSQL settings
- Caching: Implement Redis for token caching
- Load Balancing: Use HAProxy for API load distribution
- Backend Optimization: Optimize HSM/KMIP connections
Security Best Practices
Comprehensive security guidelines for Barbican deployments in production environments.
Access Control and RBAC
Role-Based Access Control
Configure proper RBAC policies:
# policy.json example
{
"admin": "role:admin",
"creator": "role:creator",
"observer": "role:observer",
"secret:decrypt": "rule:admin or rule:creator",
"secret:get": "rule:admin or rule:creator or rule:observer",
"secret:put": "rule:admin or rule:creator",
"secret:delete": "rule:admin",
"container:get": "rule:admin or rule:creator or rule:observer",
"container:post": "rule:admin or rule:creator",
"container:delete": "rule:admin"
}
Project Isolation
Ensure proper project-based isolation:
- Secrets are project-scoped by default
- Cross-project access requires explicit permissions
- Service accounts should have minimal required permissions
- Regular access reviews and cleanup
Encryption Standards
Supported Algorithms
| Algorithm Type | Supported Algorithms | Key Sizes |
|---|---|---|
| Symmetric | AES, 3DES | 128, 192, 256 bits |
| Asymmetric | RSA, ECC | 1024, 2048, 4096 bits (RSA) P-256, P-384, P-521 (ECC) |
| Hashing | SHA-1, SHA-256, SHA-512 | 160, 256, 512 bits |
Compliance and Auditing
Key compliance considerations:
- FIPS 140-2: Use certified HSMs for compliance
- Common Criteria: Implement evaluation assurance levels
- SOX/PCI DSS: Meet regulatory requirements
- Audit Trails: Comprehensive logging and monitoring
- Data Residency: Control where secrets are stored
Key Points
-
Core Functionality
- Centralized key management service
- Multi-backend secret storage
- X.509 certificate lifecycle management
- Seamless OpenStack service integration -
Advanced Features
- HSM and KMIP backend support
- PKI operations and CA integration
- Role-based access control
- Comprehensive audit logging
- API and CLI management interfaces -
Security Benefits
- Hardware-backed key storage
- Encryption in transit and at rest
- Compliance with security standards
- Automated key rotation
- Cross-service secret sharing -
Operational Excellence
- High availability deployment options
- Performance monitoring and alerting
- Backup and disaster recovery
- Integration with existing security tools
- Scalable architecture design
References
- OpenStack Barbican Documentation
- Red Hat OpenStack Platform Documentation
- OpenStack Wiki - Barbican
- Barbican API Reference
- OASIS Key Management Interoperability Protocol (KMIP)
- NIST FIPS 140-2 Security Requirements
- OpenStack Security Guide - Key Management
- Barbican Configuration Reference
- OpenStack Barbican Client Documentation
- Hardware Security Module (HSM) Integration Guide

Comments