17 min to read
BGP (Border Gateway Protocol) Complete Guide - Internet's Core Routing Protocol
From AS concepts to advanced BGP operations, comprehensive understanding of internet routing infrastructure
Overview
Understanding BGP (Border Gateway Protocol) is fundamental for anyone working with internet routing and large-scale networks. BGP is the path vector-based routing protocol used to exchange and select routes between Autonomous Systems (AS) on the internet.
This article systematically explains core BGP concepts with practical examples, covering AS fundamentals, internal vs external routing protocols, BGP path attributes, and real-world implementation strategies for network engineers.
Key Concepts Covered
- AS (Autonomous System) fundamentals and concepts
- BGP protocol architecture and operation
- iBGP vs eBGP differences and use cases
- Path attributes and route selection algorithms
- BGP security and troubleshooting
- Multi-homing and enterprise deployment strategies
Autonomous System (AS) Fundamentals
Understanding the concept of Autonomous Systems is essential for comprehending BGP and internet routing architecture.
What is an Autonomous System?
An Autonomous System (AS) is a collection of routers under the control of a single network administrator, operating under a unified management policy, or configured with a single routing strategy. Each AS represents a distinct administrative domain within the internet.
AS numbers are globally unique identifiers assigned by Regional Internet Registries (RIRs) to organizations that manage their own routing policies.
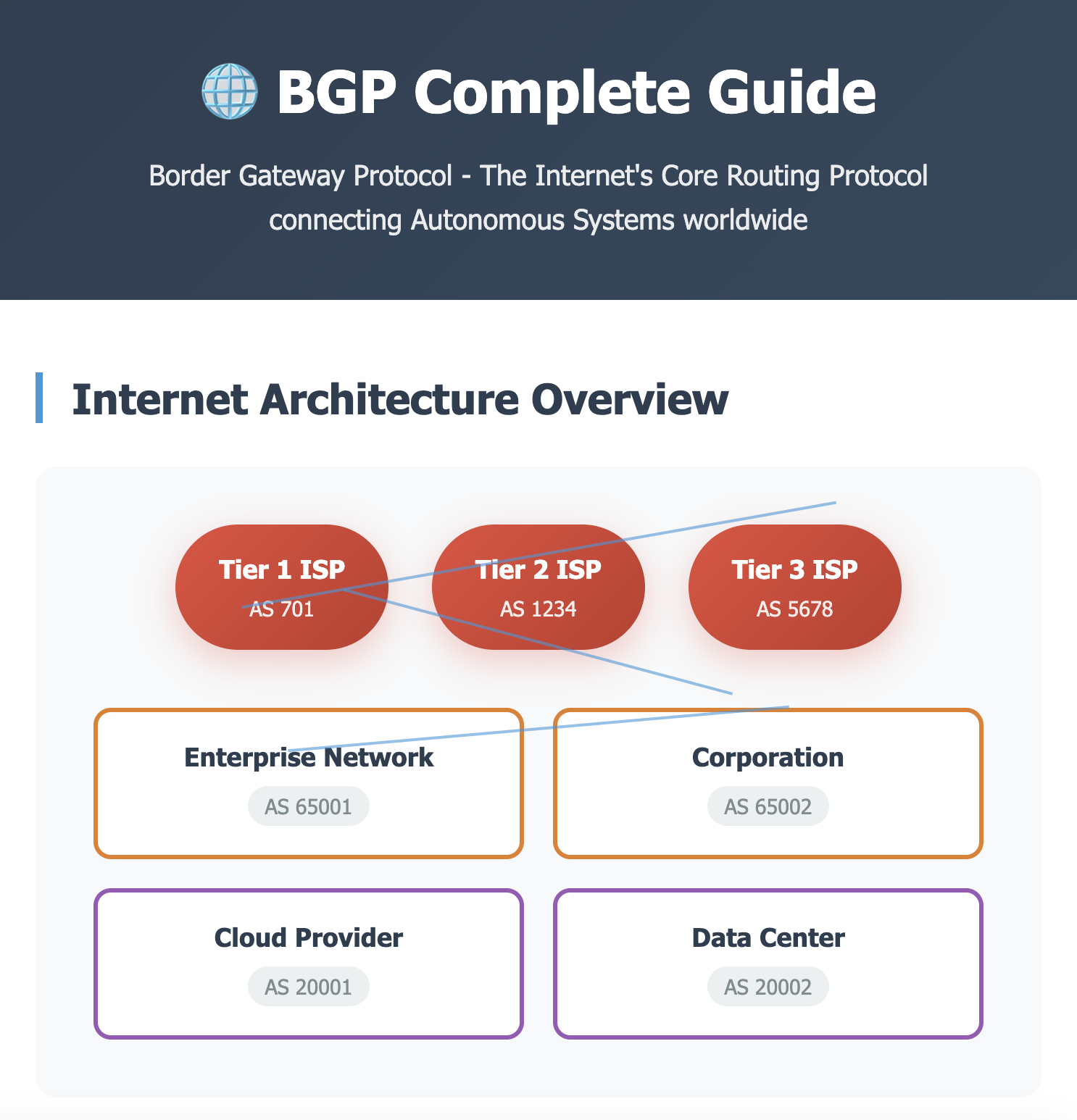
AS in Internet Architecture
AS 701] Tier2[Tier 2 ISP
AS 1234] Tier3[Tier 3 ISP
AS 5678] end subgraph "Enterprise Networks" Corp1[Corporation A
AS 10001] Corp2[Corporation B
AS 10002] Corp3[Corporation C
AS 10003] end subgraph "Data Centers" DC1[Cloud Provider
AS 20001] DC2[Hosting Company
AS 20002] end Tier1 --> Tier2 Tier2 --> Tier3 Tier3 --> Corp1 Tier3 --> Corp2 Tier3 --> Corp3 Tier2 --> DC1 Tier2 --> DC2 style Tier1 fill:#e3f2fd style Tier2 fill:#e8f5e8 style Tier3 fill:#fff3e0 style Corp1 fill:#fce4ec style DC1 fill:#f3e5f5
Interior vs Exterior Routing Protocols
| Protocol Type | Purpose and Scope | Common Examples |
|---|---|---|
| Interior Gateway Protocol (IGP) | Routing within a single AS |
|
| Exterior Gateway Protocol (EGP) | Routing between different ASes |
|
AS Boundary Router (ASBR) Role
ASBRs serve as gateways between Autonomous Systems, managing external routing information and policy enforcement:
# ASBR configuration example (Cisco IOS)
router bgp 65001
neighbor 192.168.1.1 remote-as 65002
neighbor 192.168.1.1 description "External AS 65002"
# Route redistribution from IGP to BGP
redistribute ospf 1 route-map OSPF_TO_BGP
# Route filtering and policy application
neighbor 192.168.1.1 route-map FILTER_IN in
neighbor 192.168.1.1 route-map FILTER_OUT out
ASBR Key Functions:
- Route Exchange: Advertise internal routes to external ASes
- Policy Enforcement: Apply routing policies and filters
- Security: Implement access controls and authentication
- Monitoring: Track external routing changes and performance
BGP Protocol Architecture
Understanding BGP’s fundamental architecture and operation is crucial for effective network design and troubleshooting.
BGP Protocol Characteristics
Session Establishment] Update[Update Message
Route Advertisement] Keepalive[Keepalive Message
Connection Maintenance] Notification[Notification Message
Error Handling] end subgraph "BGP Operation" PeerSetup[Peer Relationship Setup] RouteExchange[Route Information Exchange] PathSelection[Path Selection Algorithm] FIBUpdate[Forwarding Table Update] end Application --> TCP TCP --> IP IP --> DataLink Open --> PeerSetup Update --> RouteExchange Keepalive --> PeerSetup Notification --> PeerSetup RouteExchange --> PathSelection PathSelection --> FIBUpdate style Application fill:#e8f5e8 style TCP fill:#e3f2fd style Update fill:#fff8e1
BGP vs IGP Comparison
| Aspect | BGP (Border Gateway Protocol) | IGP (OSPF, EIGRP, etc.) |
|---|---|---|
| Scope | Inter-AS routing (between Autonomous Systems) | Intra-AS routing (within single Autonomous System) |
| Protocol Type | Path Vector Protocol | Link-State or Distance Vector |
| Route Selection | Policy-based with Path Attributes | Metric-based (cost, bandwidth, delay) |
| Convergence Speed | Slow (policy evaluation) | Fast (automatic metric calculation) |
| Scale | Internet-scale (millions of routes) | Network-scale (thousands of routes) |
BGP Message Types and Operation
BGP operates using four essential message types exchanged between peers:
# BGP message types and their purposes
# 1. OPEN Message - Session establishment
BGP OPEN Message:
Version: 4
My AS: 65001
Hold Time: 180
BGP Identifier: 192.168.1.1
Optional Parameters
# 2. UPDATE Message - Route advertisement
BGP UPDATE Message:
Withdrawn Routes: (empty)
Path Attributes: ORIGIN, AS_PATH, NEXT_HOP, LOCAL_PREF
NLRI: 10.0.0.0/8, 172.16.0.0/12
# 3. KEEPALIVE Message - Connection maintenance
BGP KEEPALIVE Message:
(Header only, no data)
# 4. NOTIFICATION Message - Error handling
BGP NOTIFICATION Message:
Error Code: 2 (OPEN Message Error)
Error Subcode: 1 (Unsupported Version)
Data: (error details)
BGP Session Establishment Flow:
- TCP Connection: Establish TCP connection on port 179
- OPEN Exchange: Send and receive OPEN messages
- Capability Negotiation: Agree on supported features
- Session Establishment: BGP session becomes established
- Route Exchange: Begin exchanging routing information
iBGP vs eBGP Implementation
Understanding the differences between internal and external BGP is crucial for proper network design.
iBGP (Internal BGP) Architecture
iBGP Speaker] Router2[Router 2
iBGP Speaker] Router3[Router 3
iBGP Speaker] Router4[Router 4
iBGP Speaker] subgraph "iBGP Full Mesh" Router1 -.-> Router2 Router1 -.-> Router3 Router1 -.-> Router4 Router2 -.-> Router3 Router2 -.-> Router4 Router3 -.-> Router4 end end subgraph "External Connections" AS65002[AS 65002
eBGP Peer] AS65003[AS 65003
eBGP Peer] end Router1 --> AS65002 Router2 --> AS65003 style Router1 fill:#e8f5e8 style Router2 fill:#e8f5e8 style Router3 fill:#e8f5e8 style Router4 fill:#e8f5e8 style AS65002 fill:#fff3e0 style AS65003 fill:#fff3e0
eBGP (External BGP) Architecture
eBGP Speaker] Router2[Router 2
eBGP Speaker] Router3[Router 3
iBGP Speaker] end subgraph "AS 65002" Router4[Router 4
eBGP Speaker] Router5[Router 5
iBGP Speaker] end subgraph "AS 65003" Router6[Router 6
eBGP Speaker] Router7[Router 7
iBGP Speaker] end Router1 <--> Router4 Router2 <--> Router6 Router1 -.-> Router2 Router1 -.-> Router3 Router2 -.-> Router3 Router4 -.-> Router5 Router6 -.-> Router7 style Router1 fill:#e8f5e8 style Router4 fill:#fff3e0 style Router6 fill:#fce4ec
iBGP vs eBGP Configuration Differences
# iBGP Configuration (same AS)
router bgp 65001
neighbor 192.168.1.2 remote-as 65001 # Same AS number
neighbor 192.168.1.2 update-source loopback0
neighbor 192.168.1.2 next-hop-self # Modify NEXT_HOP attribute
# eBGP Configuration (different AS)
router bgp 65001
neighbor 10.0.0.2 remote-as 65002 # Different AS number
neighbor 10.0.0.2 ebgp-multihop 2 # Allow non-direct connections
neighbor 10.0.0.2 send-community # Send community attributes
# Route redistribution between iBGP and eBGP
router bgp 65001
redistribute connected route-map CONNECTED_TO_BGP
redistribute ospf 1 route-map OSPF_TO_BGP
Key Differences:
- AS Number: iBGP uses same AS, eBGP uses different AS
- NEXT_HOP Handling: iBGP modifies NEXT_HOP, eBGP preserves it
- TTL Values: iBGP TTL=255, eBGP TTL=1 (configurable)
- Route Advertisement: iBGP doesn’t advertise routes learned from iBGP peers
BGP Path Attributes and Route Selection
Understanding BGP path attributes is essential for implementing routing policies and optimizing network performance.
BGP Path Attributes Overview
| Attribute Type | Well-Known vs Optional | Description | Example Values |
|---|---|---|---|
| ORIGIN | Well-Known Mandatory | Route source indication | IGP (0), EGP (1), Incomplete (2) |
| AS_PATH | Well-Known Mandatory | List of ASes traversed | 65002 65003 65004 |
| NEXT_HOP | Well-Known Mandatory | Next hop IP address | 192.168.1.1 |
| LOCAL_PREF | Well-Known Discretionary | Local preference value | 100 (default), 200 (high priority) |
| MED | Optional Non-Transitive | Multi-Exit Discriminator | 0-4294967295 |
| COMMUNITY | Optional Transitive | Route grouping and policy | 65001:100, 65001:200 |
BGP Route Selection Algorithm
BGP uses a deterministic algorithm to select the best route when multiple paths exist:
# BGP Route Selection Process (Cisco IOS order)
# 1. Highest Weight (Cisco proprietary)
# 2. Highest LOCAL_PREF
# 3. Locally originated routes
# 4. Shortest AS_PATH
# 5. Lowest ORIGIN code (IGP < EGP < Incomplete)
# 6. Lowest MED
# 7. eBGP over iBGP
# 8. Lowest IGP metric to NEXT_HOP
# 9. Lowest Router ID
# 10. Lowest Neighbor IP address
# Example route selection
BGP table version is 15, local router ID is 192.168.1.1
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal
*> 10.0.0.0/8 192.168.1.2 0 0 65002 i
* 10.0.0.0/8 192.168.1.3 0 0 65003 65002 i
* 10.0.0.0/8 192.168.1.4 0 0 65004 65003 65002 i
Route Selection Example:
- Route 1: AS_PATH length 1, LOCAL_PREF 100
- Route 2: AS_PATH length 2, LOCAL_PREF 100
- Route 3: AS_PATH length 3, LOCAL_PREF 100
- Result: Route 1 selected (shortest AS_PATH)
Path Attribute Manipulation
# LOCAL_PREF manipulation for inbound traffic control
route-map SET_LOCAL_PREF permit 10
match ip address prefix-list PREFERRED_ROUTES
set local-preference 200
route-map SET_LOCAL_PREF permit 20
set local-preference 100
# AS_PATH prepending for outbound traffic control
route-map PREPEND_AS permit 10
set as-path prepend 65001 65001 65001
# MED manipulation for inbound traffic engineering
route-map SET_MED permit 10
match community 65001:100
set metric 100
route-map SET_MED permit 20
match community 65001:200
set metric 200
BGP Security and Best Practices
Implementing proper security measures is crucial for protecting BGP infrastructure from attacks and misconfigurations.
BGP Security Threats and Countermeasures
Unauthorized route advertisement] Leaking[Route Leaking
Accidental route propagation] Spoofing[IP Spoofing
Fake BGP packets] DDoS[DDoS Attacks
BGP session flooding] end subgraph "Security Countermeasures" Filtering[Prefix Filtering
Route validation] Authentication[MD5 Authentication
BGP session security] TTL[TTL Security
Hop count validation] RPKI[RPKI Validation
Route origin verification] end Hijacking --> Filtering Leaking --> Filtering Spoofing --> Authentication DDoS --> TTL Hijacking --> RPKI style Hijacking fill:#ffebee style Filtering fill:#e8f5e8 style RPKI fill:#fff8e1
Prefix Filtering Implementation
# Prefix filtering configuration examples
# 1. Inbound prefix filtering
ip prefix-list ALLOW_INBOUND permit 10.0.0.0/8 le 24
ip prefix-list ALLOW_INBOUND permit 172.16.0.0/12 le 24
ip prefix-list ALLOW_INBOUND permit 192.168.0.0/16 le 24
route-map FILTER_INBOUND permit 10
match ip address prefix-list ALLOW_INBOUND
route-map FILTER_INBOUND deny 20
# 2. Outbound prefix filtering
ip prefix-list ALLOW_OUTBOUND permit 203.0.113.0/24
ip prefix-list ALLOW_OUTBOUND permit 198.51.100.0/24
route-map FILTER_OUTBOUND permit 10
match ip address prefix-list ALLOW_OUTBOUND
route-map FILTER_OUTBOUND deny 20
# 3. Apply filters to BGP neighbors
router bgp 65001
neighbor 192.168.1.2 route-map FILTER_INBOUND in
neighbor 192.168.1.2 route-map FILTER_OUTBOUND out
Filtering Best Practices:
- Prefix Validation: Only accept routes for allocated address space
- AS_PATH Filtering: Reject routes with invalid AS_PATH
- Community Filtering: Use communities for policy enforcement
- Rate Limiting: Implement BGP update rate limiting
BGP Authentication and TTL Security
# MD5 authentication for BGP sessions
router bgp 65001
neighbor 192.168.1.2 password BGP_SECRET_123
neighbor 192.168.1.2 ttl-security hops 1
# TTL security configuration
router bgp 65001
neighbor 10.0.0.2 ebgp-multihop 2
neighbor 10.0.0.2 ttl-security hops 2
# BGP session monitoring
router bgp 65001
neighbor 192.168.1.2 timers 30 90
neighbor 192.168.1.2 keepalive-interval 30
neighbor 192.168.1.2 hold-time 90
Security Configuration Guidelines:
- Strong Passwords: Use complex, unique passwords for each peer
- TTL Validation: Implement TTL security for eBGP sessions
- Session Monitoring: Configure appropriate keepalive and hold timers
- Logging: Enable BGP logging for security monitoring
BGP Multi-homing and Load Balancing
Implementing multi-homing strategies is essential for network reliability and performance optimization.
Multi-homing Architecture
Primary BGP Speaker] Router2[Router 2
Secondary BGP Speaker] Core[Core Network] end subgraph "ISP Connections" ISP1[ISP A
AS 65002] ISP2[ISP B
AS 65003] end subgraph "Traffic Flow" Inbound[Inbound Traffic] Outbound[Outbound Traffic] LoadBalancing[Load Balancing] end Router1 --> ISP1 Router2 --> ISP2 Core --> Router1 Core --> Router2 ISP1 --> Inbound ISP2 --> Inbound Outbound --> LoadBalancing LoadBalancing --> Router1 LoadBalancing --> Router2 style Router1 fill:#e8f5e8 style Router2 fill:#e8f5e8 style ISP1 fill:#fff3e0 style ISP2 fill:#fce4ec
Multi-homing Configuration Strategies
# Primary/Backup configuration
router bgp 65001
neighbor 192.168.1.1 remote-as 65002
neighbor 192.168.1.1 description "Primary ISP"
neighbor 192.168.1.1 route-map SET_PREFERENCE_PRIMARY out
neighbor 192.168.2.1 remote-as 65003
neighbor 192.168.2.1 description "Backup ISP"
neighbor 192.168.2.1 route-map SET_PREFERENCE_BACKUP out
# Route maps for traffic control
route-map SET_PREFERENCE_PRIMARY permit 10
set local-preference 200
set community 65001:100
route-map SET_PREFERENCE_BACKUP permit 10
set local-preference 100
set community 65001:200
# Load balancing with equal-cost paths
router bgp 65001
maximum-paths 2
maximum-paths ibgp 2
Multi-homing Benefits:
- Redundancy: Multiple ISP connections for failover
- Load Distribution: Traffic spread across multiple paths
- Performance: Optimized routing based on ISP performance
- Cost Optimization: Balance traffic based on pricing
Traffic Engineering with BGP
# Community-based traffic engineering
ip community-list 100 permit 65001:100
ip community-list 200 permit 65001:200
route-map TRAFFIC_ENGINEERING permit 10
match community 100
set local-preference 200
set as-path prepend 65001
route-map TRAFFIC_ENGINEERING permit 20
match community 200
set local-preference 100
set as-path prepend 65001 65001
# Apply to BGP neighbors
router bgp 65001
neighbor 192.168.1.1 route-map TRAFFIC_ENGINEERING in
neighbor 192.168.2.1 route-map TRAFFIC_ENGINEERING in
BGP Troubleshooting and Monitoring
Effective troubleshooting requires systematic approaches and proper monitoring tools.
Common BGP Issues and Solutions
| Issue Category | Symptoms and Indicators | Diagnostic Steps and Solutions |
|---|---|---|
| Session Establishment |
|
|
| Route Advertisement |
|
|
| Path Selection |
|
|
Essential BGP Troubleshooting Commands
# BGP neighbor status verification
show ip bgp summary
show ip bgp neighbors
show ip bgp neighbors 192.168.1.1
# BGP routing table examination
show ip bgp
show ip bgp 10.0.0.0/8
show ip bgp regexp "65002"
# Path attribute analysis
show ip bgp 10.0.0.0/8 longer-prefixes
show ip bgp paths
show ip bgp community
# Real-time debugging
debug ip bgp updates
debug ip bgp keepalives
debug ip bgp events
# Route filtering verification
show ip prefix-list
show route-map
show ip bgp filter-list
Troubleshooting Methodology:
- Verify Physical Connectivity: Check interface status and cabling
- Check BGP Configuration: Verify AS numbers, passwords, and policies
- Analyze Route Exchange: Monitor BGP updates and path attributes
- Validate Policy Implementation: Check route maps and filters
- Monitor Performance: Track convergence time and stability
BGP Monitoring and Alerting
# BGP monitoring script example
#!/bin/bash
# Check BGP session status
bgp_status=$(show ip bgp summary | grep -E "^(Neighbor|Total)" | tail -1)
if [[ $bgp_status == *"Idle"* ]] || [[ $bgp_status == *"Active"* ]]; then
echo "ALERT: BGP session issues detected at $(date)" >> bgp_alerts.log
echo "$bgp_status" >> bgp_alerts.log
# Send notification
echo "BGP Alert: $bgp_status" | mail -s "BGP Session Alert" admin@company.com
fi
# Monitor route count changes
current_routes=$(show ip bgp | grep -c "^*>")
if [ -f route_count.txt ]; then
previous_routes=$(cat route_count.txt)
if [ $current_routes -ne $previous_routes ]; then
echo "Route count changed: $previous_routes -> $current_routes" >> bgp_changes.log
fi
fi
echo $current_routes > route_count.txt
Key Points
- Autonomous System Design: Proper AS design and numbering is fundamental for scalable BGP implementation and internet connectivity
- Protocol Architecture: Understanding BGP's path vector nature and TCP-based operation is crucial for troubleshooting and optimization
- Path Attribute Management: Mastering BGP path attributes enables sophisticated routing policies and traffic engineering
- Security Implementation: Prefix filtering, authentication, and TTL security are essential for protecting BGP infrastructure
- Multi-homing Strategies: Proper multi-homing design provides redundancy, load balancing, and cost optimization
- Monitoring and Troubleshooting: Systematic troubleshooting approaches and comprehensive monitoring ensure BGP network health
- Policy Implementation: Route maps, prefix lists, and community attributes enable granular traffic control
- Performance Optimization: Understanding route selection algorithms and attribute manipulation maximizes network efficiency
Learning Path Recommendation
| Learning Stage | Recommended Focus Areas |
|---|---|
| Foundation |
|
| Intermediate |
|
| Advanced |
|
| Expert |
|
References
- RFC 4271 - A Border Gateway Protocol 4 (BGP-4)
- RFC 8200 - Internet Protocol, Version 6 (IPv6) Specification
- Cisco BGP Configuration Guide
- Juniper BGP Documentation
- BGP Route Server Project
- RIPE NCC BGP Tools
- BGP Looking Glass
- BGP Security Best Practices
- RPKI (Resource Public Key Infrastructure)
- BGP Flow Specification
- BGP Add-Path
- BGP Monitoring Protocol (BMP)
- BGP-LS (Link State)
- BGP EVPN
- BGP for IPv6
- BGP Communities
- BGP Route Refresh
- BGP Route Damping
- BGP Confederation
- BGP Route Reflection
- BGP Graceful Restart

Comments