5 min to read
Linux Kernel Parameters (sysctl) Guide
Understanding and Applying Linux Kernel Parameters in Practice
Understanding Linux Kernel Parameters
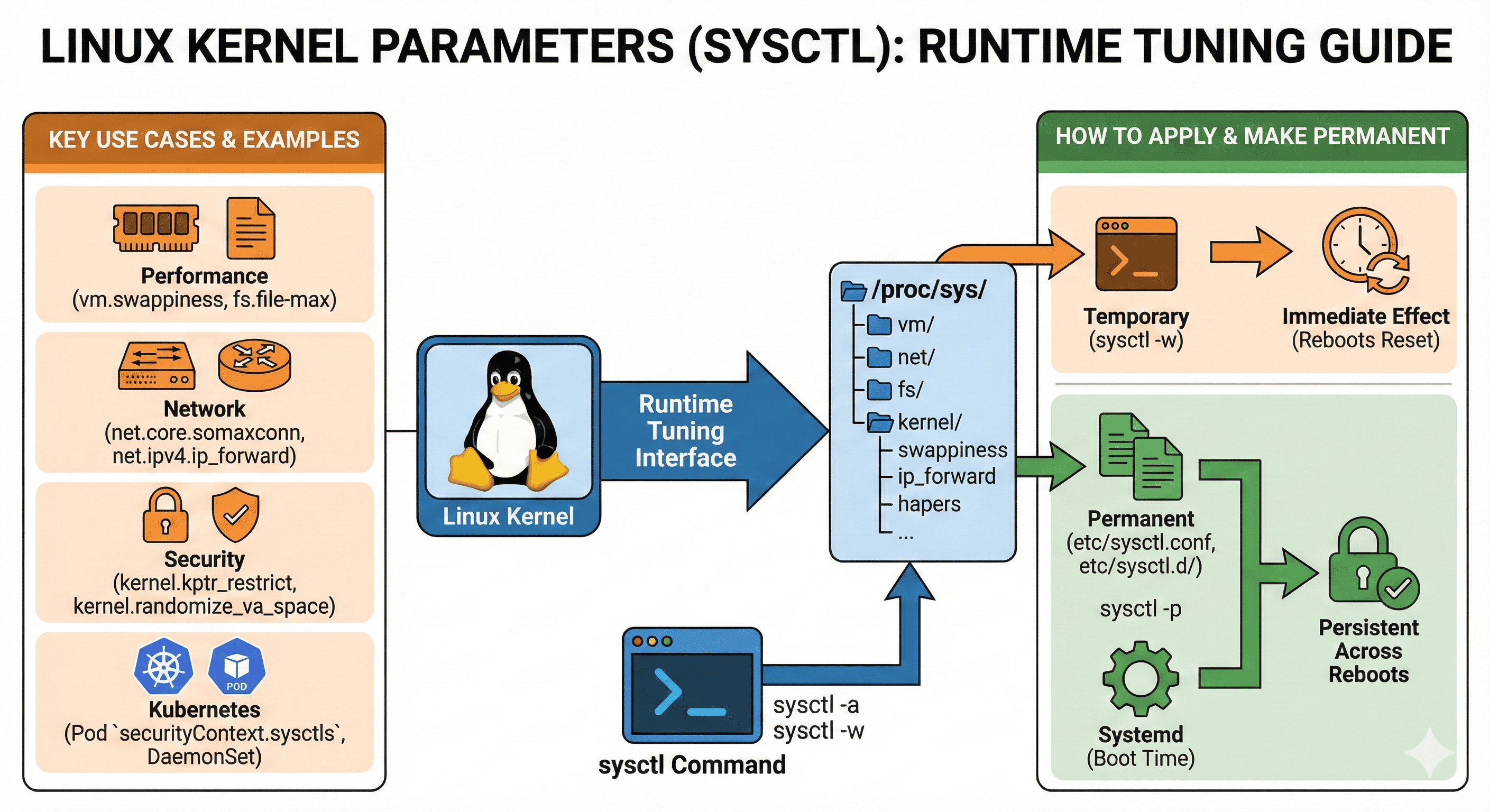
Linux kernel parameters (sysctl settings) are runtime configuration values that allow fine-tuning of the operating system’s behavior. These parameters are exposed through the virtual filesystem at /proc/sys and can be viewed or modified using the sysctl command.
What are Kernel Parameters?
System Configuration Control
Kernel parameters enable:
- Performance Tuning: Optimize system resource utilization<
- Security Hardening: Configure system security features
- Network Optimization: Adjust network stack behavior
- Memory Management: Control memory allocation and swapping
Checking and Modifying Kernel Parameters
Kernel parameters can be checked and modified using either the sysctl command or by directly accessing the /proc/sys filesystem. Understanding both methods is essential for effective system administration.
Viewing Parameters
| Method | Description |
|---|---|
| sysctl -a | Display all available kernel parameters and their current values |
| sysctl parameter | View a specific parameter's value |
| cat /proc/sys/path | Read parameter value directly from filesystem |
Temporary Changes
Runtime Modifications
To make temporary changes that persist until reboot:
sysctl -w: Change parameter value using sysctl commandecho value > /proc/sys/path: Direct filesystem modification
Example: Adjusting swappiness
sysctl -w vm.swappiness=10
echo 10 > /proc/sys/vm/swappiness
Permanent Changes
Persistent Configuration
To make changes persist across reboots:
- /etc/sysctl.conf: Global configuration file
- /etc/sysctl.d/*.conf: Directory for modular configuration
Example configuration:
# /etc/sysctl.d/99-custom.conf
vm.swappiness = 10
fs.file-max = 100000
net.core.somaxconn = 1024
Common Kernel Parameters
Understanding commonly used kernel parameters is essential for system optimization and security. Here are some of the most frequently adjusted parameters grouped by their purpose.
Performance Parameters
| Parameter | Description | Usage |
|---|---|---|
| vm.swappiness | Controls tendency to swap memory pages | Lower values (10-20) for database servers |
| fs.file-max | Maximum number of file handles | Increase for high-concurrency servers |
| vm.overcommit_memory | Memory allocation policy | Set to 1 for container environments |
Network Parameters
| Parameter | Description | Usage |
|---|---|---|
| net.core.somaxconn | Maximum TCP connection queue | Increase for high-traffic web servers |
| net.ipv4.tcp_tw_reuse | Reuse TIME_WAIT sockets | Enable for high-connection servers |
| net.ipv4.ip_forward | Enable IP forwarding | Required for routers and containers |
Security Parameters
| Parameter | Description | Usage |
|---|---|---|
| kernel.kptr_restrict | Kernel pointer exposure control | Set to 1 for enhanced security |
| kernel.randomize_va_space | ASLR configuration | Set to 2 for maximum protection |
| net.ipv4.conf.all.accept_redirects | ICMP redirect acceptance | Set to 0 for security hardening |
Kubernetes and Container Environments
In containerized environments, kernel parameter management requires special consideration due to the shared kernel architecture and security implications.
Container Considerations
Container Security
Important considerations for containers:
- Most parameters affect the entire host
- Limited parameter modification from containers
- Security implications of parameter changes
Kubernetes Implementation
Kubernetes Configuration
Methods for managing parameters in Kubernetes:
- Node-level Configuration: Using
sysctl.conforsysctl.d - DaemonSet Approach: Using privileged containers
- Pod-level Settings: Using securityContext for safe sysctls
Example Kubernetes Configuration
apiVersion: v1
kind: Pod
metadata:
name: sysctl-example
spec:
securityContext:
sysctls:
- name: net.core.somaxconn
value: "1024"
- name: kernel.msgmax
value: "65536"
Best Practices
Following best practices when working with kernel parameters is crucial for system stability and security.
Implementation Guidelines
- Documentation: Keep detailed records of changes
- Testing: Test changes in non-production first
- Monitoring: Monitor system behavior after changes
- Backup: Maintain backup of original settings
Common Pitfalls
- Making changes without understanding impact
- Applying changes without testing
- Ignoring system-specific requirements
- Overlooking security implications
Key Points
-
Core Concepts
- Runtime system configuration
- Performance optimization
- Security hardening
- Network tuning -
Management
- Temporary vs permanent changes
- Configuration files
- Container considerations
- Security implications -
Best Practices
- Careful testing
- Documentation
- Monitoring
- Security awareness

Comments