28 min to read
Enterprise Istio: Advanced Service Mesh Architecture and Production Deployment Guide
Comprehensive guide to production-ready Istio deployments with advanced security, observability, and multi-cluster patterns
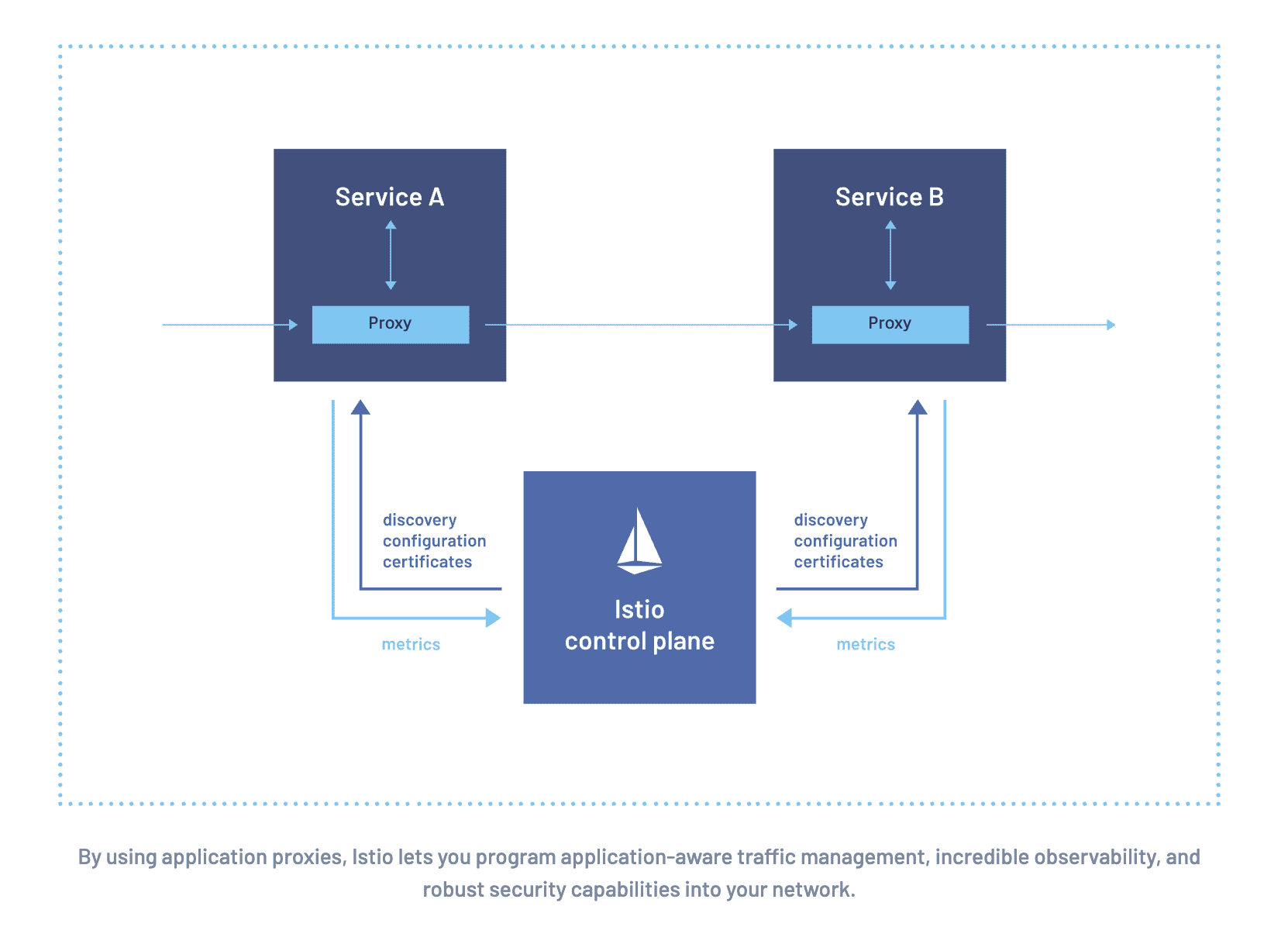
Executive Overview
Istio has evolved from a promising service mesh experiment into the de facto standard for enterprise microservices communication, powering production workloads that handle billions of requests daily across organizations like Google, Netflix, and major financial institutions.
As modern applications increasingly adopt microservices architectures with hundreds or thousands of services, the complexity of inter-service communication, security, and observability has grown exponentially.
Enterprise Istio deployments must address sophisticated requirements including zero-trust security, multi-cluster federation, advanced traffic management, comprehensive observability, and strict compliance frameworks.
This guide explores Istio from foundational concepts to enterprise-grade production patterns, covering advanced security implementations, intelligent traffic management, global mesh federation, and operational excellence practices.
Whether you're architecting greenfield microservices infrastructure, securing existing service-to-service communication, or preparing for multi-region service mesh deployments, this guide provides the depth and practical insights needed for Istio mastery in enterprise environments.
2017-2019] --> B[Production Adoption
2019-2021] B --> C[Enterprise Scale
2021-2023] C --> D[AI-Native Mesh
2023-Present] end subgraph "Foundation Capabilities" A --> A1[Basic Traffic Management] A --> A2[mTLS Security] A --> A3[Observability Stack] end subgraph "Production Features" B --> B1[Multi-Cluster Support] B --> B2[Advanced Security] B --> B3[Performance Optimization] B --> B4[Operational Tools] end subgraph "Enterprise Excellence" C --> C1[Zero-Trust Architecture] C --> C2[Global Mesh Federation] C --> C3[Policy as Code] C --> C4[Compliance Automation] end subgraph "Next-Generation Mesh" D --> D1[AI-Driven Traffic Management] D --> D2[Intelligent Security] D --> D3[Automated Optimization] D --> D4[Predictive Scaling] end style A fill:#ffebee,stroke:#d32f2f,stroke-width:2px style B fill:#e8f5e8,stroke:#388e3c,stroke-width:2px style C fill:#e3f2fd,stroke:#1976d2,stroke-width:2px style D fill:#f3e5f5,stroke:#7b1fa2,stroke-width:2px
Istio Evolution: From basic service mesh to comprehensive enterprise platform
Advanced Enterprise Architecture
Istio’s enterprise architecture enables sophisticated microservices communication patterns through a distributed control plane and intelligent data plane that scale to thousands of services across multiple clusters and regions.
Multi-Cluster Coordinator] GlobalCerts[Global Certificate Authority] PolicyEngine[Global Policy Engine] ConfigStore[Centralized Configuration Store] end subgraph "Regional Control Planes" Region1[US East Control Plane] Region2[EU Central Control Plane] Region3[APAC Control Plane] end subgraph "Data Plane - Production Cluster" EnvoyFleet[Envoy Proxy Fleet
10,000+ Sidecars] GatewayMesh[Gateway Mesh
Ingress/Egress] ServiceMesh[Service Mesh
East-West Traffic] end subgraph "Advanced Security Layer" ZeroTrust[Zero-Trust Enforcement] PolicyValidation[Policy Validation Engine] ThreatDetection[Real-time Threat Detection] ComplianceAudit[Compliance Auditing] end subgraph "Observability Platform" MetricsAggregation[Global Metrics Aggregation] DistributedTracing[Distributed Tracing Platform] LogAggregation[Centralized Log Analytics] ServiceTopology[Real-time Service Topology] end PrimaryIstiod --> Region1 PrimaryIstiod --> Region2 PrimaryIstiod --> Region3 Region1 --> EnvoyFleet Region2 --> EnvoyFleet Region3 --> EnvoyFleet EnvoyFleet --> GatewayMesh EnvoyFleet --> ServiceMesh PolicyEngine --> ZeroTrust PolicyEngine --> PolicyValidation EnvoyFleet --> MetricsAggregation EnvoyFleet --> DistributedTracing EnvoyFleet --> LogAggregation style PrimaryIstiod fill:#e3f2fd,stroke:#1976d2,stroke-width:3px style EnvoyFleet fill:#fff3e0,stroke:#f57c00,stroke-width:2px style ZeroTrust fill:#e8f5e8,stroke:#388e3c,stroke-width:2px style MetricsAggregation fill:#f3e5f5,stroke:#7b1fa2,stroke-width:2px
Enterprise Istio Architecture: Global control plane with distributed execution and advanced security
Advanced Control Plane Configuration
Production-Grade Istiod Deployment
Enterprise Istio requires sophisticated control plane configuration for high availability, scalability, and security.
# High-availability Istiod configuration
apiVersion: install.istio.io/v1alpha1
kind: IstioOperator
metadata:
name: enterprise-control-plane
spec:
values:
pilot:
env:
EXTERNAL_ISTIOD: true
PILOT_ENABLE_WORKLOAD_ENTRY_AUTOREGISTRATION: true
PILOT_ENABLE_CROSS_CLUSTER_WORKLOAD_ENTRY: true
PILOT_TRACE_SAMPLING: 1.0
global:
meshID: enterprise-mesh-prod
network: network1
components:
pilot:
k8s:
replicaCount: 3 # HA deployment
resources:
requests:
cpu: 500m
memory: 2048Mi
limits:
cpu: 2000m
memory: 4096Mi
env:
- name: PILOT_ENABLE_WORKLOAD_ENTRY_AUTOREGISTRATION
value: "true"
- name: PILOT_ENABLE_CROSS_CLUSTER_WORKLOAD_ENTRY
value: "true"
hpaSpec:
minReplicas: 3
maxReplicas: 10
targetCPUUtilizationPercentage: 70
nodeSelector:
node-type: istio-control-plane
tolerations:
- key: "dedicated"
operator: "Equal"
value: "istio"
effect: "NoSchedule"
affinity:
podAntiAffinity:
requiredDuringSchedulingIgnoredDuringExecution:
- labelSelector:
matchLabels:
app: istiod
topologyKey: kubernetes.io/hostname
ingressGateways:
- name: istio-ingressgateway
enabled: true
k8s:
replicaCount: 3
resources:
requests:
cpu: 1000m
memory: 1024Mi
limits:
cpu: 4000m
memory: 2048Mi
service:
type: LoadBalancer
annotations:
service.beta.kubernetes.io/aws-load-balancer-type: "nlb"
service.beta.kubernetes.io/aws-load-balancer-backend-protocol: "tcp"
nodeSelector:
node-type: istio-gateway
tolerations:
- key: "dedicated"
operator: "Equal"
value: "istio"
effect: "NoSchedule"
Multi-Cluster Federation Setup
Enterprise deployments often require service mesh federation across multiple clusters and regions.
Step 1: Primary Cluster Setup
Step 2: Remote Cluster Setup
Step 3: Cross-Cluster Service Discovery
# Enable cross-cluster service discovery
apiVersion: networking.istio.io/v1alpha3
kind: ServiceEntry
metadata:
name: remote-cluster-services
namespace: istio-system
spec:
hosts:
- productcatalog.production.global
location: MESH_EXTERNAL
ports:
- number: 80
name: http
protocol: HTTP
resolution: DNS
addresses:
- 240.0.0.1 # Virtual IP for cross-cluster service
endpoints:
- address: productcatalog.production.svc.cluster.local
network: network1
ports:
http: 80
- address: productcatalog-remote.production.remote.local
network: network2
ports:
http: 80
---
# Cross-cluster endpoint configuration
apiVersion: networking.istio.io/v1alpha3
kind: WorkloadEntry
metadata:
name: productcatalog-remote
namespace: production
spec:
address: 10.10.1.100 # Remote cluster service IP
ports:
http: 80
labels:
app: productcatalog
version: v2
cluster: remote
network: network2
serviceAccount: productcatalog
Zero-Trust Security Architecture
Enterprise Istio deployments require comprehensive zero-trust security that operates at multiple layers, providing defense-in-depth for microservices communication.
Advanced Security Policies
Comprehensive mTLS Implementation
Production-grade mutual TLS configuration with certificate lifecycle management.
# Enterprise mTLS configuration with custom CA
apiVersion: security.istio.io/v1beta1
kind: PeerAuthentication
metadata:
name: enterprise-mtls-strict
namespace: istio-system
spec:
mtls:
mode: STRICT
---
# Workload-specific mTLS policy
apiVersion: security.istio.io/v1beta1
kind: PeerAuthentication
metadata:
name: payment-service-mtls
namespace: payment
spec:
selector:
matchLabels:
app: payment-service
mtls:
mode: STRICT
portLevelMtls:
8080:
mode: STRICT
9090: # Health check port
mode: DISABLE
---
# Advanced authorization policies
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: payment-service-authz
namespace: payment
spec:
selector:
matchLabels:
app: payment-service
rules:
# Allow only authenticated services
- from:
- source:
principals: ["cluster.local/ns/order/sa/order-service"]
to:
- operation:
methods: ["POST"]
paths: ["/api/v1/payments"]
when:
- key: request.headers[x-user-id]
values: ["*"]
- key: request.headers[authorization]
values: ["Bearer *"]
# Allow health checks
- from:
- source:
principals: ["cluster.local/ns/istio-system/sa/istio-proxy"]
to:
- operation:
methods: ["GET"]
paths: ["/health", "/ready"]
# Deny all other traffic
- {} # Default deny
---
# JWT validation policy
apiVersion: security.istio.io/v1beta1
kind: RequestAuthentication
metadata:
name: jwt-validation
namespace: api-gateway
spec:
selector:
matchLabels:
app: api-gateway
jwtRules:
- issuer: "https://auth.enterprise.com"
jwksUri: "https://auth.enterprise.com/.well-known/jwks.json"
audiences:
- "api.enterprise.com"
forwardOriginalToken: true
fromHeaders:
- name: Authorization
prefix: "Bearer "
fromParams:
- "access_token"
Advanced Threat Detection and Response
Intelligent security monitoring and automated threat response capabilities.
Security Monitoring with Falco Integration
# Falco rules for Istio security monitoring
apiVersion: v1
kind: ConfigMap
metadata:
name: istio-security-rules
namespace: istio-system
data:
istio_rules.yaml: |
- rule: Istio Unauthorized Access Attempt
desc: Detect unauthorized access attempts in Istio mesh
condition: >
k8s_audit and
ka.verb in (create, update, patch) and
ka.target.resource in (authorizationpolicies, peerauthentications) and
not ka.user.name in (system:serviceaccount:istio-system:istiod)
output: >
Unauthorized Istio security policy modification
(user=%ka.user.name verb=%ka.verb resource=%ka.target.resource
object=%ka.target.name)
priority: WARNING
- rule: Istio mTLS Disabled
desc: Detect when mTLS is disabled
condition: >
k8s_audit and
ka.verb in (create, update, patch) and
ka.target.resource=peerauthentications and
ka.request_object contains "mode: DISABLE"
output: >
mTLS disabled in Istio mesh
(user=%ka.user.name namespace=%ka.target.namespace
policy=%ka.target.name)
priority: ERROR
---
# Security monitoring deployment
apiVersion: apps/v1
kind: DaemonSet
metadata:
name: istio-security-monitor
namespace: istio-system
spec:
selector:
matchLabels:
app: istio-security-monitor
template:
metadata:
labels:
app: istio-security-monitor
spec:
containers:
- name: falco
image: falcosecurity/falco:latest
args:
- /usr/bin/falco
- --cri
- /host/run/containerd/containerd.sock
- --k8s-api
- --k8s-api-cert=/var/run/secrets/kubernetes.io/serviceaccount/ca.crt
- --k8s-api-token=/var/run/secrets/kubernetes.io/serviceaccount/token
volumeMounts:
- name: istio-rules
mountPath: /etc/falco/rules.d
- name: containerd-socket
mountPath: /host/run/containerd/containerd.sock
- name: proc
mountPath: /host/proc
readOnly: true
- name: boot
mountPath: /host/boot
readOnly: true
- name: modules
mountPath: /host/lib/modules
readOnly: true
- name: usr
mountPath: /host/usr
readOnly: true
- name: etc
mountPath: /host/etc
readOnly: true
volumes:
- name: istio-rules
configMap:
name: istio-security-rules
- name: containerd-socket
hostPath:
path: /run/containerd/containerd.sock
- name: proc
hostPath:
path: /proc
- name: boot
hostPath:
path: /boot
- name: modules
hostPath:
path: /lib/modules
- name: usr
hostPath:
path: /usr
- name: etc
hostPath:
path: /etc
hostNetwork: true
hostPID: true
privileged: true
Real-time Threat Response with OPA Gatekeeper
# OPA Gatekeeper policy for Istio security
apiVersion: templates.gatekeeper.sh/v1beta1
kind: ConstraintTemplate
metadata:
name: istiosecuritypolicy
spec:
crd:
spec:
names:
kind: IstioSecurityPolicy
validation:
openAPIV3Schema:
type: object
properties:
allowedModes:
type: array
items:
type: string
requiredLabels:
type: array
items:
type: string
targets:
- target: admission.k8s.gatekeeper.sh
rego: |
package istiosecuritypolicy
violation[{"msg": msg}] {
input.review.kind.kind == "PeerAuthentication"
input.review.object.spec.mtls.mode != "STRICT"
msg := "PeerAuthentication must use STRICT mTLS mode"
}
violation[{"msg": msg}] {
input.review.kind.kind == "AuthorizationPolicy"
count(input.review.object.spec.rules) == 0
msg := "AuthorizationPolicy must have at least one rule"
}
---
# Apply security constraints
apiVersion: config.gatekeeper.sh/v1alpha1
kind: IstioSecurityPolicy
metadata:
name: enforce-strict-mtls
spec:
match:
- apiGroups: ["security.istio.io"]
kinds: ["PeerAuthentication"]
namespaces: ["production", "staging"]
parameters:
allowedModes: ["STRICT"]
requiredLabels: ["security-level"]
Automated Security Response System
Advanced Traffic Management
Enterprise traffic management requires sophisticated patterns for canary deployments, A/B testing, chaos engineering, and intelligent load balancing across global infrastructure.
Intelligent Traffic Routing
Advanced Canary Deployment Strategies
Production-grade canary deployments with automated rollback and intelligent traffic shifting.
# Advanced canary deployment with automated analysis
apiVersion: networking.istio.io/v1beta1
kind: VirtualService
metadata:
name: user-service-canary
namespace: production
spec:
hosts:
- user-service
http:
- match:
- headers:
canary-user:
exact: "true"
route:
- destination:
host: user-service
subset: v2
weight: 100
fault:
delay:
percentage:
value: 0.1
fixedDelay: 100ms # Chaos engineering
- match:
- uri:
prefix: "/api/v1/users"
route:
- destination:
host: user-service
subset: v1
weight: 90 # Stable version
- destination:
host: user-service
subset: v2
weight: 10 # Canary version
timeout: 30s
retries:
attempts: 3
perTryTimeout: 10s
retryOn: 5xx,reset,connect-failure,refused-stream
---
# Destination rule with advanced load balancing
apiVersion: networking.istio.io/v1beta1
kind: DestinationRule
metadata:
name: user-service-destination
namespace: production
spec:
host: user-service
trafficPolicy:
loadBalancer:
simple: LEAST_CONN
connectionPool:
tcp:
maxConnections: 100
connectTimeout: 30s
tcpKeepalive:
time: 7200s
interval: 75s
http:
http1MaxPendingRequests: 50
http2MaxRequests: 100
maxRequestsPerConnection: 10
maxRetries: 3
idleTimeout: 90s
h2UpgradePolicy: UPGRADE
outlierDetection:
consecutive5xxErrors: 5
interval: 30s
baseEjectionTime: 30s
maxEjectionPercent: 50
minHealthPercent: 30
subsets:
- name: v1
labels:
version: v1
trafficPolicy:
loadBalancer:
simple: ROUND_ROBIN
- name: v2
labels:
version: v2
trafficPolicy:
loadBalancer:
simple: LEAST_CONN
connectionPool:
tcp:
maxConnections: 50 # More conservative for canary
Global Traffic Management
Sophisticated multi-region traffic routing with latency optimization and failover.
Global Load Balancing Strategy
Cross-Region Failover Configuration
# Service entry for cross-region services
apiVersion: networking.istio.io/v1alpha3
kind: ServiceEntry
metadata:
name: user-service-global
namespace: production
spec:
hosts:
- user-service.global
location: MESH_EXTERNAL
ports:
- number: 80
name: http
protocol: HTTP
- number: 443
name: https
protocol: HTTPS
resolution: DNS
addresses:
- 240.0.0.10 # Global virtual IP
endpoints:
# US West primary
- address: user-service.us-west.example.com
ports:
http: 80
https: 443
locality: us-west/zone1
priority: 0
weight: 100
# US East backup
- address: user-service.us-east.example.com
ports:
http: 80
https: 443
locality: us-east/zone1
priority: 1
weight: 100
# EU primary for EU traffic
- address: user-service.eu-central.example.com
ports:
http: 80
https: 443
locality: eu-central/zone1
priority: 0
weight: 100
---
# Health check configuration for global services
apiVersion: networking.istio.io/v1alpha3
kind: DestinationRule
metadata:
name: user-service-global-health
namespace: production
spec:
host: user-service.global
trafficPolicy:
connectionPool:
tcp:
maxConnections: 100
connectTimeout: 10s
tcpKeepalive:
time: 7200s
interval: 75s
http:
http1MaxPendingRequests: 50
http2MaxRequests: 100
maxRequestsPerConnection: 5
maxRetries: 3
idleTimeout: 60s
outlierDetection:
consecutiveGatewayErrors: 3
consecutive5xxErrors: 3
interval: 10s
baseEjectionTime: 30s
maxEjectionPercent: 50
minHealthPercent: 50
# Health check configuration
healthCheck:
interval: 5s
timeout: 3s
unhealthyThreshold: 3
healthyThreshold: 2
path: /health
httpHeaders:
- name: x-health-check
value: istio
Traffic Shifting Automation Script
Production Observability and Analytics
Enterprise Istio deployments require comprehensive observability that spans metrics, traces, logs, and topology visualization with advanced analytics and machine learning insights.
Advanced Monitoring Stack
Comprehensive Metrics and Alerting
Production-grade monitoring with custom SLI/SLO definitions and intelligent alerting.
Distributed Tracing with Intelligence
Advanced tracing with dependency analysis and performance insights.
Jaeger Configuration for Enterprise Scale
# Production Jaeger deployment with advanced configuration
apiVersion: jaegertracing.io/v1
kind: Jaeger
metadata:
name: jaeger-production
namespace: istio-system
spec:
strategy: production
storage:
type: elasticsearch
elasticsearch:
nodeCount: 3
redundancyPolicy: SingleRedundancy
storage:
storageClassName: fast-ssd
size: 100Gi
resources:
requests:
cpu: 1000m
memory: 2Gi
limits:
cpu: 2000m
memory: 4Gi
collector:
replicas: 3
resources:
requests:
cpu: 500m
memory: 1Gi
limits:
cpu: 1000m
memory: 2Gi
config: |
receivers:
otlp:
protocols:
grpc:
endpoint: 0.0.0.0:14250
http:
endpoint: 0.0.0.0:14268
jaeger:
protocols:
grpc:
endpoint: 0.0.0.0:14250
thrift_http:
endpoint: 0.0.0.0:14268
thrift_compact:
endpoint: 0.0.0.0:14267
thrift_binary:
endpoint: 0.0.0.0:14267
processors:
batch:
timeout: 1s
send_batch_size: 1024
memory_limiter:
limit_mib: 512
exporters:
elasticsearch:
endpoints: ["http://elasticsearch.istio-system:9200"]
index: jaeger-span-%{+yyyy.MM.dd}
service:
pipelines:
traces:
receivers: [otlp, jaeger]
processors: [memory_limiter, batch]
exporters: [elasticsearch]
query:
replicas: 2
resources:
requests:
cpu: 500m
memory: 1Gi
limits:
cpu: 1000m
memory: 2Gi
---
# Istio telemetry configuration for tracing
apiVersion: telemetry.istio.io/v1alpha1
kind: Telemetry
metadata:
name: default
namespace: istio-system
spec:
tracing:
- providers:
- name: jaeger
- customTags:
user_id:
header:
name: x-user-id
request_id:
header:
name: x-request-id
business_unit:
environment:
name: BUSINESS_UNIT
defaultValue: "unknown"
version:
environment:
name: APP_VERSION
defaultValue: "unknown"
- sampling: 1.0 # 100% sampling for production analysis
Service Dependency Analysis Scripts
Advanced Trace Analytics with Custom Queries
Performance Optimization and Scaling
Enterprise Istio deployments require sophisticated performance optimization and intelligent scaling to handle massive traffic loads while maintaining optimal resource utilization.
Advanced Performance Tuning
Envoy Proxy Optimization
Production-grade Envoy configuration for maximum performance and reliability.
# Advanced Envoy proxy configuration
apiVersion: v1
kind: ConfigMap
metadata:
name: istio-proxy-config
namespace: istio-system
data:
mesh: |
defaultConfig:
proxyStatsMatcher:
inclusionRegexps:
- ".*circuit_breakers.*"
- ".*upstream_rq_retry.*"
- ".*upstream_cx_.*"
- ".*_cx_.*"
concurrency: 4 # Match CPU cores
# Performance optimizations
envoyAccessLogService:
address: jaeger-collector.istio-system:14250
# Resource limits
proxyMemoryLimit: "1Gi"
proxyCPULimit: "2000m"
# Advanced configuration
holdApplicationUntilProxyStarts: true
statusPort: 15020
# Custom bootstrap configuration
envoyMetricsService:
address: prometheus-collector.istio-system:9090
defaultProviders:
metrics:
- prometheus
tracing:
- jaeger
accessLogging:
- envoy
# Global mesh configuration
trustDomain: cluster.local
defaultServiceExportTo:
- "."
defaultVirtualServiceExportTo:
- "."
defaultDestinationRuleExportTo:
- "."
---
# High-performance Envoy deployment
apiVersion: apps/v1
kind: DaemonSet
metadata:
name: istio-proxy-performance
namespace: istio-system
spec:
selector:
matchLabels:
app: istio-proxy
template:
metadata:
labels:
app: istio-proxy
spec:
containers:
- name: istio-proxy
image: istio/proxyv2:1.19.0
resources:
requests:
cpu: 500m
memory: 512Mi
limits:
cpu: 2000m
memory: 1Gi
env:
- name: PILOT_ENABLE_WORKLOAD_ENTRY_AUTOREGISTRATION
value: "true"
- name: BOOTSTRAP_XDS_AGENT
value: "true"
securityContext:
runAsUser: 1337
runAsGroup: 1337
volumeMounts:
- name: workload-socket
mountPath: /var/run/secrets/workload-spiffe-uds
- name: credential-socket
mountPath: /var/run/secrets/credential-uds
- name: workload-certs
mountPath: /var/run/secrets/workload-spiffe-credentials
volumes:
- name: workload-socket
emptyDir: {}
- name: credential-socket
emptyDir: {}
- name: workload-certs
emptyDir: {}
nodeSelector:
kubernetes.io/arch: amd64
tolerations:
- effect: NoSchedule
operator: Exists
Multi-Cluster and Federation
Enterprise Istio deployments often span multiple clusters and regions, requiring sophisticated federation and cross-cluster communication patterns.
Advanced Multi-Cluster Patterns
Cross-Cluster Service Discovery
Intelligent service discovery and traffic routing across federated clusters.
# Multi-cluster service exposure
apiVersion: networking.istio.io/v1alpha3
kind: ServiceEntry
metadata:
name: cross-cluster-payment-service
namespace: production
spec:
hosts:
- payment-service.global
location: MESH_EXTERNAL
ports:
- number: 80
name: http
protocol: HTTP
- number: 443
name: https
protocol: HTTPS
resolution: DNS
addresses:
- 10.240.0.1 # Cross-cluster service IP
endpoints:
- address: payment-service.us-west.cluster.local
network: us-west-network
priority: 0
weight: 100
- address: payment-service.eu-central.cluster.local
network: eu-central-network
priority: 1
weight: 100
---
# Global destination rule for cross-cluster traffic
apiVersion: networking.istio.io/v1alpha3
kind: DestinationRule
metadata:
name: payment-service-global
namespace: production
spec:
host: payment-service.global
trafficPolicy:
loadBalancer:
localityLbSetting:
enabled: true
distribute:
- from: "region/us-west/*"
to:
"region/us-west/*": 80
"region/us-east/*": 20
- from: "region/eu-central/*"
to:
"region/eu-central/*": 100
failover:
- from: us-west
to: us-east
- from: eu-central
to: us-east
outlierDetection:
consecutive5xxErrors: 3
interval: 30s
baseEjectionTime: 30s
Conclusion
Istio has matured into the definitive enterprise service mesh platform, providing sophisticated capabilities for modern microservices architectures that demand security, observability, and intelligent traffic management at scale.
This exploration demonstrates that mastering enterprise Istio requires deep understanding of distributed systems, advanced security frameworks, and sophisticated operational practices.
Key Success Factors for Production Istio:
Architectural Excellence: Understanding Istio’s distributed control plane, advanced Envoy proxy configurations, and multi-cluster federation patterns enables deployment of resilient, scalable service mesh infrastructure supporting thousands of services across global infrastructure.
Zero-Trust Security Mastery: Implementing comprehensive mTLS, advanced authorization policies, and intelligent threat detection provides defense-in-depth security that meets enterprise compliance requirements while maintaining operational efficiency.
Intelligent Traffic Management: Leveraging advanced routing algorithms, automated canary deployments, and global traffic optimization ensures optimal user experience and system reliability across diverse deployment scenarios.
Production Observability: Comprehensive monitoring, distributed tracing, and ML-driven analytics provide deep insights into service behavior, enabling proactive optimization and rapid issue resolution.
Operational Excellence: Advanced performance tuning, intelligent scaling, and automated policy management ensure reliable operations at enterprise scale while maintaining cost efficiency and security compliance.
Final Recommendations
Based on industry best practices and real-world enterprise deployments:
- Begin with a single cluster pilot deployment in staging environment
- Implement comprehensive observability stack from day one
- Establish clear security policies before production deployment
- Train operations teams on Istio troubleshooting and maintenance
- Plan for gradual service onboarding rather than "big bang" migration
- Implement high-availability control plane with proper resource allocation
- Use canary deployments for all service updates
- Establish automated security policy enforcement
- Deploy comprehensive monitoring and alerting
- Create disaster recovery procedures and test them regularly
- Design for network segmentation and security boundaries
- Implement intelligent traffic routing and failover mechanisms
- Use GitOps for configuration management across clusters
- Establish global observability with centralized analytics
- Plan for compliance and audit requirements from the start
- Automate certificate lifecycle management
- Implement capacity planning based on mesh metrics
- Use chaos engineering to validate resilience
- Establish clear runbooks for common operational scenarios
- Continuously optimize performance based on real traffic patterns
Production Deployment Checklist
- Kubernetes cluster meets minimum requirements (1.24+)
- Dedicated nodes for Istio control plane (if required)
- Network policies configured for cluster security
- Load balancers configured for ingress traffic
- Storage classes available for persistent volumes
- Custom root CA configured and secured
- mTLS policies defined for all services
- Authorization policies implemented
- Network policies complement Istio security
- Secret management system integrated
- Prometheus configured with sufficient retention
- Grafana dashboards customized for your services
- Jaeger deployed with persistent storage
- Log aggregation system configured
- Alerting rules defined and tested
- Gateway configurations tested
- Virtual services defined for all applications
- Destination rules configured with proper policies
- Circuit breakers and retry policies set
- Canary deployment strategy defined
- Backup and restore procedures documented
- Upgrade procedures tested in staging
- Runbooks created for common issues
- Team trained on Istio operations
- Emergency response procedures defined
Remember: Successful enterprise Istio deployment requires careful planning, comprehensive testing, and gradual rollout.
Focus on establishing solid foundations in security, observability, and operational practices before scaling to full production workloads.
References and Advanced Resources
- Istio Official Documentation
- Istio Architecture Deep Dive
- Multi-Cluster Installation
- Istio Security Best Practices
- Traffic Management Guide
- Observability Configuration
- Performance and Scalability
- Istio Operations Guide
- Envoy Proxy Documentation
- Istio Community
- Service Mesh Comparison
- Istio Ecosystem

Comments