25 min to read
Terraform Fundamentals: Complete Guide to Infrastructure as Code
Master Terraform installation, configuration files, and essential commands for cloud infrastructure automation
Overview
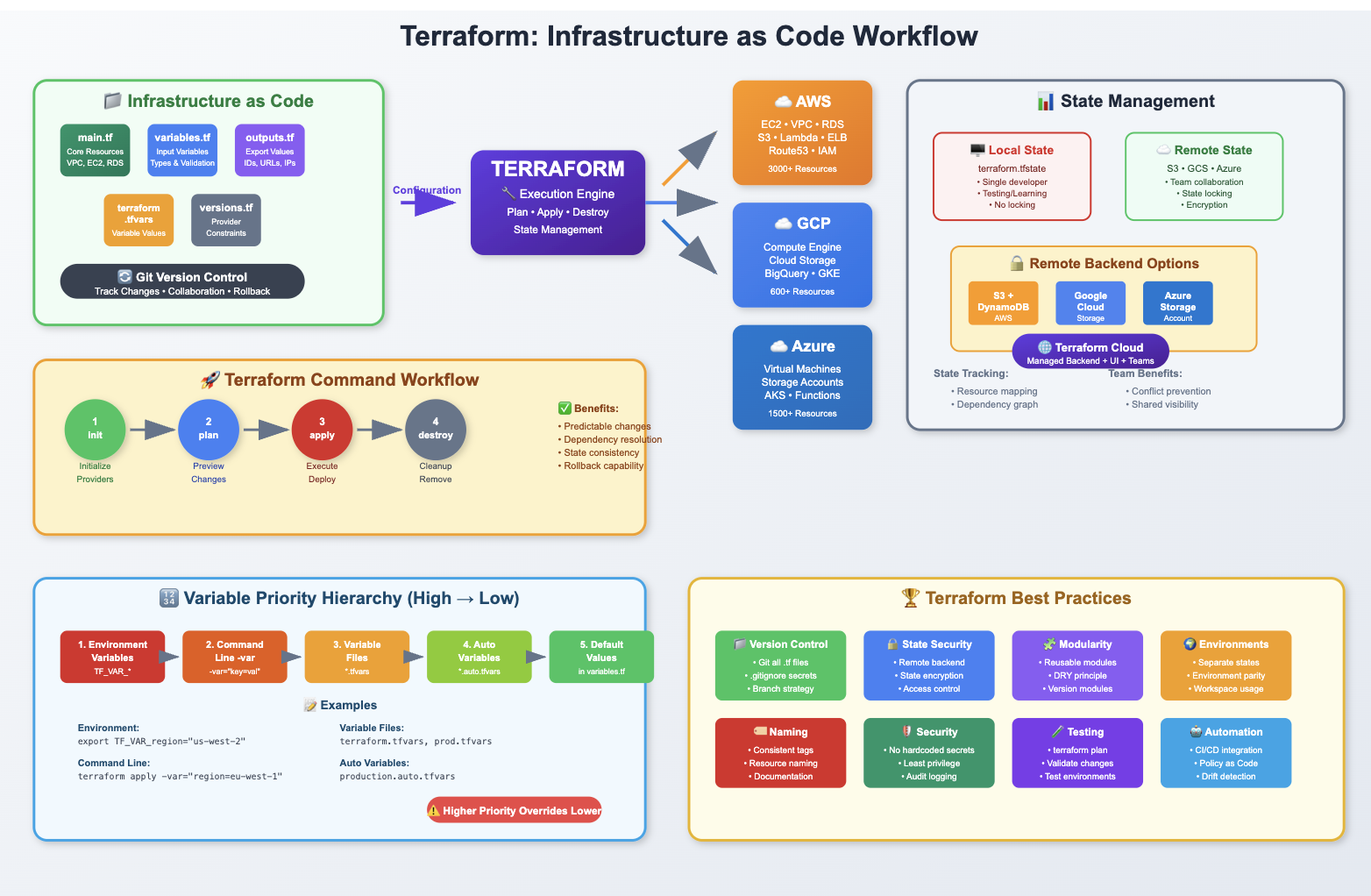
Terraform is HashiCorp’s open-source Infrastructure as Code (IaC) tool that enables you to define, provision, and manage cloud and on-premises infrastructure through declarative configuration files.
Using HCL (HashiCorp Configuration Language), Terraform allows you to describe your infrastructure’s desired state and automatically builds and manages it.
This comprehensive guide covers Terraform installation methods, core concepts, essential file structures, and fundamental commands necessary for effective infrastructure automation.
We’ll explore how Terraform supports multiple cloud providers including AWS, Azure, Google Cloud, and on-premises services, making it a versatile solution for hybrid and multi-cloud environments.
Terraform’s declarative approach simplifies infrastructure management by focusing on the desired end state rather than the procedural steps, enabling consistent, repeatable, and version-controlled infrastructure deployments.
What is Terraform?
Terraform is a cloud-agnostic infrastructure automation tool that uses HCL (HashiCorp Configuration Language) to define infrastructure resources as code. It enables teams to provision, modify, and destroy infrastructure consistently across different environments and cloud providers.
Core Philosophy:
- Declarative Configuration: Define what you want, not how to achieve it
- Immutable Infrastructure: Replace rather than modify existing resources
- Plan Before Apply: Preview changes before execution
- State Management: Track infrastructure state and dependencies
- Provider Ecosystem: Extensive support for cloud and on-premises services
Key Use Cases:
Multi-Cloud Infrastructure
- Consistent resource provisioning across AWS, GCP, Azure
- Hybrid cloud and on-premises integration
- Cross-provider networking and service integration
DevOps Automation
- CI/CD pipeline infrastructure provisioning
- Environment parity across dev, staging, production
- Infrastructure testing and validation
Enterprise Scale Management
- Large-scale resource orchestration
- Compliance and governance automation
- Cost optimization through resource lifecycle management
Terraform’s Key Features
1. Declarative Configuration
Define your infrastructure’s desired state in configuration files, and Terraform automatically determines the necessary actions to achieve that state.
# Example: Simple VPC declaration
resource "aws_vpc" "main" {
cidr_block = "10.0.0.0/16"
enable_dns_hostnames = true
enable_dns_support = true
tags = {
Name = "main-vpc"
Environment = "production"
}
}
2. Multi-Cloud Support
Use identical configuration syntax across different cloud providers, enabling consistent infrastructure patterns and easier migration strategies.
# AWS Provider
provider "aws" {
region = "us-west-2"
}
# Google Cloud Provider
provider "google" {
project = "my-project-id"
region = "us-central1"
}
# Azure Provider
provider "azurerm" {
features {}
}
3. Modularity and Reusability
Create reusable modules that encapsulate common infrastructure patterns, promoting consistency and reducing duplication across projects.
# Module usage example
module "vpc" {
source = "./modules/vpc"
vpc_name = "production-vpc"
cidr_block = "10.0.0.0/16"
environment = "production"
public_subnets = ["10.0.1.0/24", "10.0.2.0/24"]
private_subnets = ["10.0.10.0/24", "10.0.20.0/24"]
}
4. State Management and Planning
Terraform maintains a state file that tracks resource relationships and enables intelligent change planning and dependency resolution.
# State management commands
terraform state list # List tracked resources
terraform state show aws_instance.web # Show resource details
terraform state pull # Download remote state
terraform state push # Upload state to remote backend
5. Version Control and Collaboration
Infrastructure configurations integrate seamlessly with Git workflows, enabling code review, branching strategies, and collaborative development.
# Typical workflow
git clone https://github.com/company/terraform-infrastructure
cd terraform-infrastructure
terraform init
terraform plan
terraform apply
Installation Methods
Method 1: Official Package Repository (Recommended)
Method 2: Direct Binary Installation
# Download and install specific version
TERRAFORM_VERSION="1.14.0-alpha20250813"
wget https://releases.hashicorp.com/terraform/${TERRAFORM_VERSION}/terraform_${TERRAFORM_VERSION}_linux_amd64.zip
unzip terraform_${TERRAFORM_VERSION}_linux_amd64.zip
sudo mv terraform /usr/local/bin/
chmod +x /usr/local/bin/terraform
# Verify installation
terraform version
Method 3: Package Managers
# macOS with Homebrew
brew tap hashicorp/tap
brew install hashicorp/tap/terraform
# Windows with Chocolatey
choco install terraform
# Arch Linux
pacman -S terraform
Method 4: Docker Container
# Run Terraform in Docker
docker run --rm -it -v $(pwd):/workspace -w /workspace hashicorp/terraform:1.14.0-alpha20250813 version
# Create alias for convenience
alias terraform='docker run --rm -it -v $(pwd):/workspace -w /workspace hashicorp/terraform:1.14.0-alpha20250813'
Post-Installation Setup
# Enable autocompletion
terraform -install-autocomplete
# Verify installation and check version
terraform version
# Check available commands
terraform -help
Terraform File Structure and Organization
Project Directory Layout
# Recommended Terraform project structure
terraform-project/
├── main.tf # Primary resource definitions
├── variables.tf # Input variable declarations
├── outputs.tf # Output value definitions
├── versions.tf # Provider and Terraform version constraints
├── terraform.tfvars # Variable value assignments
├── terraform.tfvars.example # Example variable values
├── modules/ # Local modules directory
│ ├── vpc/
│ ├── compute/
│ └── database/
├── environments/ # Environment-specific configurations
│ ├── dev/
│ ├── staging/
│ └── production/
└── .terraform/ # Terraform working directory (auto-generated)
1. main.tf - Core Infrastructure Definition
The main.tf file contains your primary resource definitions and is the heart of your Terraform configuration.
# main.tf
terraform {
required_version = ">= 1.0"
required_providers {
aws = {
source = "hashicorp/aws"
version = "~> 5.0"
}
}
backend "s3" {
bucket = "my-terraform-state"
key = "infrastructure/terraform.tfstate"
region = "us-west-2"
}
}
provider "aws" {
region = var.aws_region
default_tags {
tags = {
Environment = var.environment
Project = var.project_name
ManagedBy = "terraform"
Owner = var.owner
}
}
}
# VPC Configuration
resource "aws_vpc" "main" {
cidr_block = var.vpc_cidr
enable_dns_hostnames = true
enable_dns_support = true
tags = {
Name = "${var.project_name}-vpc"
}
}
# Internet Gateway
resource "aws_internet_gateway" "main" {
vpc_id = aws_vpc.main.id
tags = {
Name = "${var.project_name}-igw"
}
}
# Public Subnets
resource "aws_subnet" "public" {
count = length(var.public_subnet_cidrs)
vpc_id = aws_vpc.main.id
cidr_block = var.public_subnet_cidrs[count.index]
availability_zone = data.aws_availability_zones.available.names[count.index]
map_public_ip_on_launch = true
tags = {
Name = "${var.project_name}-public-subnet-${count.index + 1}"
Type = "public"
}
}
# Data source for availability zones
data "aws_availability_zones" "available" {
state = "available"
}
2. variables.tf - Input Variable Declarations
Define all input variables with types, descriptions, and default values for better documentation and validation.
# variables.tf
variable "aws_region" {
type = string
description = "AWS region for infrastructure deployment"
default = "us-west-2"
validation {
condition = can(regex("^[a-z]{2}-[a-z]+-[0-9]$", var.aws_region))
error_message = "AWS region must be in format: us-west-2, eu-central-1, etc."
}
}
variable "environment" {
type = string
description = "Environment name (dev, staging, production)"
validation {
condition = contains(["dev", "staging", "production"], var.environment)
error_message = "Environment must be one of: dev, staging, production."
}
}
variable "project_name" {
type = string
description = "Name of the project for resource naming"
validation {
condition = can(regex("^[a-z][a-z0-9-]*[a-z0-9]$", var.project_name))
error_message = "Project name must start with a letter, contain only lowercase letters, numbers, and hyphens."
}
}
variable "vpc_cidr" {
type = string
description = "CIDR block for the VPC"
default = "10.0.0.0/16"
validation {
condition = can(cidrhost(var.vpc_cidr, 0))
error_message = "VPC CIDR must be a valid IPv4 CIDR block."
}
}
variable "public_subnet_cidrs" {
type = list(string)
description = "List of CIDR blocks for public subnets"
default = ["10.0.1.0/24", "10.0.2.0/24"]
validation {
condition = alltrue([
for cidr in var.public_subnet_cidrs : can(cidrhost(cidr, 0))
])
error_message = "All subnet CIDRs must be valid IPv4 CIDR blocks."
}
}
variable "instance_type" {
type = string
description = "EC2 instance type for web servers"
default = "t3.micro"
}
variable "owner" {
type = string
description = "Owner tag for resources"
}
variable "enable_monitoring" {
type = bool
description = "Enable detailed monitoring for EC2 instances"
default = false
}
variable "backup_retention_days" {
type = number
description = "Number of days to retain backups"
default = 7
validation {
condition = var.backup_retention_days >= 1 && var.backup_retention_days <= 365
error_message = "Backup retention days must be between 1 and 365."
}
}
variable "additional_tags" {
type = map(string)
description = "Additional tags to apply to resources"
default = {}
}
3. terraform.tfvars - Variable Value Assignments
Store actual values for your variables. This file should be customized per environment and may contain sensitive data.
# terraform.tfvars
aws_region = "us-west-2"
environment = "production"
project_name = "web-application"
owner = "devops-team"
vpc_cidr = "10.0.0.0/16"
public_subnet_cidrs = [
"10.0.1.0/24",
"10.0.2.0/24",
"10.0.3.0/24"
]
instance_type = "t3.small"
enable_monitoring = true
backup_retention_days = 30
additional_tags = {
CostCenter = "engineering"
Compliance = "required"
Backup = "daily"
}
4. outputs.tf - Output Value Definitions
Define outputs to expose important resource attributes that other configurations or external systems might need.
# outputs.tf
output "vpc_id" {
description = "ID of the created VPC"
value = aws_vpc.main.id
}
output "vpc_cidr_block" {
description = "CIDR block of the VPC"
value = aws_vpc.main.cidr_block
}
output "public_subnet_ids" {
description = "List of public subnet IDs"
value = aws_subnet.public[*].id
}
output "internet_gateway_id" {
description = "ID of the Internet Gateway"
value = aws_internet_gateway.main.id
}
output "availability_zones" {
description = "List of availability zones used"
value = data.aws_availability_zones.available.names
}
# Sensitive output example
output "database_password" {
description = "Database administrator password"
value = random_password.db_password.result
sensitive = true
}
# Complex output with multiple attributes
output "vpc_info" {
description = "Complete VPC information"
value = {
id = aws_vpc.main.id
cidr_block = aws_vpc.main.cidr_block
default_route_table_id = aws_vpc.main.default_route_table_id
default_security_group_id = aws_vpc.main.default_security_group_id
dns_hostnames_enabled = aws_vpc.main.enable_dns_hostnames
dns_support_enabled = aws_vpc.main.enable_dns_support
}
}
5. versions.tf - Version Constraints
Specify Terraform and provider version requirements to ensure consistent behavior across different environments.
# versions.tf
terraform {
required_version = ">= 1.0"
required_providers {
aws = {
source = "hashicorp/aws"
version = "~> 5.0"
}
random = {
source = "hashicorp/random"
version = "~> 3.1"
}
local = {
source = "hashicorp/local"
version = "~> 2.1"
}
tls = {
source = "hashicorp/tls"
version = "~> 4.0"
}
}
# Remote state backend configuration
backend "s3" {
# Configuration can be provided via backend config file
# or specified during terraform init
}
}
Essential Terraform Commands
Core Workflow Commands
# 1. Initialize working directory
terraform init
# - Downloads provider plugins
# - Initializes backend (if configured)
# - Creates .terraform directory
# 2. Validate configuration syntax
terraform validate
# - Checks for syntax errors
# - Validates configuration structure
# - Returns success/failure status
# 3. Format configuration files
terraform fmt
# - Formats .tf files to canonical style
# - Use -recursive for subdirectories
# - Use -diff to show formatting changes
# 4. Plan infrastructure changes
terraform plan
# - Shows what changes will be made
# - Performs refresh of current state
# - No actual changes are made
# 5. Apply planned changes
terraform apply
# - Executes the planned changes
# - Prompts for confirmation (unless -auto-approve)
# - Updates state file
# 6. Destroy infrastructure
terraform destroy
# - Plans destruction of all resources
# - Prompts for confirmation
# - Removes resources in dependency order
Advanced Command Options
# Planning with specific targets
terraform plan -target=aws_instance.web
terraform plan -target=module.database
# Apply with variable overrides
terraform apply -var="environment=staging" -var="instance_count=3"
terraform apply -var-file="staging.tfvars"
# Destroy specific resources
terraform destroy -target=aws_instance.test
# Import existing infrastructure
terraform import aws_instance.example i-1234567890abcdef0
# State management commands
terraform state list # List all resources
terraform state show aws_instance.web # Show resource details
terraform state rm aws_instance.old # Remove from state
terraform state mv aws_instance.old aws_instance.new # Rename resource
# Workspace management
terraform workspace list # List workspaces
terraform workspace new production # Create new workspace
terraform workspace select production # Switch workspace
terraform workspace delete old-workspace # Delete workspace
# Output management
terraform output # Show all outputs
terraform output vpc_id # Show specific output
terraform output -json # JSON format output
Environment-Specific Commands
# Development environment
terraform plan -var-file="environments/dev.tfvars"
terraform apply -var-file="environments/dev.tfvars"
# Production environment with approval
terraform plan -var-file="environments/prod.tfvars" -out=prod.tfplan
terraform apply prod.tfplan
# Staging with specific backend config
terraform init -backend-config="environments/staging-backend.hcl"
terraform apply -var-file="environments/staging.tfvars"
Variable Priority and Management
Variable Value Precedence (Highest to Lowest)
Terraform evaluates variables in a specific order, with later sources overriding earlier ones:
# 1. Environment variables (highest priority)
export TF_VAR_instance_type="t3.large"
export TF_VAR_environment="production"
# 2. Command-line flags
terraform apply -var="instance_type=t3.medium" -var="environment=staging"
# 3. Variable files specified on command line
terraform apply -var-file="custom.tfvars" -var-file="override.tfvars"
# 4. terraform.tfvars file (if present)
# 5. terraform.tfvars.json file (if present)
# 6. *.auto.tfvars files (alphabetical order)
# 7. *.auto.tfvars.json files (alphabetical order)
# 8. Default values in variable declarations (lowest priority)
Variable File Examples
# environments/dev.tfvars
environment = "development"
instance_type = "t3.micro"
enable_monitoring = false
backup_retention_days = 3
# environments/staging.tfvars
environment = "staging"
instance_type = "t3.small"
enable_monitoring = true
backup_retention_days = 7
# environments/prod.tfvars
environment = "production"
instance_type = "t3.medium"
enable_monitoring = true
backup_retention_days = 30
Environment Variable Usage
# Setting Terraform variables via environment
export TF_VAR_aws_region="eu-west-1"
export TF_VAR_project_name="my-application"
export TF_VAR_owner="platform-team"
# AWS credentials (not Terraform variables)
export AWS_ACCESS_KEY_ID="your-access-key"
export AWS_SECRET_ACCESS_KEY="your-secret-key"
export AWS_DEFAULT_REGION="us-west-2"
# Terraform behavior configuration
export TF_LOG="DEBUG" # Enable debug logging
export TF_LOG_PATH="./terraform.log" # Log to file
export TF_DATA_DIR="./.terraform-custom" # Custom data directory
Sensitive Variable Handling
# variables.tf - Mark sensitive variables
variable "database_password" {
type = string
description = "Database administrator password"
sensitive = true
}
variable "api_key" {
type = string
description = "Third-party API key"
sensitive = true
}
# Using sensitive variables in resources
resource "aws_db_instance" "main" {
identifier = "main-database"
username = "admin"
password = var.database_password # Will be masked in logs
# Other configuration...
}
State Management and Backends
Local State (Default)
# Local state is stored in terraform.tfstate
# Suitable for individual development and learning
# Not recommended for team environments
# State file location
ls -la terraform.tfstate*
Remote State Configuration
# S3 Backend (recommended for AWS)
terraform {
backend "s3" {
bucket = "my-terraform-state-bucket"
key = "infrastructure/terraform.tfstate"
region = "us-west-2"
encrypt = true
dynamodb_table = "terraform-state-lock"
}
}
# Azure Backend
terraform {
backend "azurerm" {
resource_group_name = "terraform-state-rg"
storage_account_name = "terraformstatesa"
container_name = "tfstate"
key = "infrastructure.terraform.tfstate"
}
}
# Google Cloud Storage Backend
terraform {
backend "gcs" {
bucket = "my-terraform-state-bucket"
prefix = "infrastructure"
}
}
State Locking and Team Collaboration
# Initialize with backend configuration
terraform init -backend-config="bucket=my-unique-bucket"
# State locking prevents concurrent modifications
# DynamoDB table for S3 backend locking
resource "aws_dynamodb_table" "terraform_locks" {
name = "terraform-state-lock"
billing_mode = "PAY_PER_REQUEST"
hash_key = "LockID"
attribute {
name = "LockID"
type = "S"
}
tags = {
Name = "Terraform State Lock Table"
}
}
Best Practices and Recommendations
1. Project Organization
# Multi-environment structure
terraform-infrastructure/
├── modules/ # Reusable modules
│ ├── vpc/
│ ├── ec2/
│ └── rds/
├── environments/ # Environment-specific configs
│ ├── dev/
│ │ ├── main.tf
│ │ ├── variables.tf
│ │ └── terraform.tfvars
│ ├── staging/
│ └── prod/
├── global/ # Shared resources
│ ├── iam/
│ └── route53/
└── scripts/ # Helper scripts
├── deploy.sh
└── validate.sh
2. Naming Conventions
# Resource naming convention
resource "aws_instance" "web" {
# Use descriptive names
tags = {
Name = "${var.project_name}-${var.environment}-web-${count.index + 1}"
}
}
# Variable naming
variable "vpc_cidr_block" { # Clear and descriptive
# Not: variable "cidr" or variable "c"
}
# Output naming
output "vpc_id" { # Match resource attribute
output "database_endpoint" { # Clear purpose
}
3. Security Best Practices
# Use data sources for sensitive information
data "aws_secretsmanager_secret_version" "db_password" {
secret_id = "prod/database/password"
}
# Avoid hardcoded secrets
resource "aws_db_instance" "main" {
password = data.aws_secretsmanager_secret_version.db_password.secret_string
# NOT: password = "hardcoded-password"
}
# Tag all resources for governance
resource "aws_instance" "web" {
tags = merge(var.common_tags, {
Name = "web-server"
Environment = var.environment
Backup = "required"
})
}
4. Module Design Principles
# modules/vpc/main.tf - Well-designed module
variable "vpc_name" {
type = string
description = "Name of the VPC"
}
variable "cidr_block" {
type = string
description = "CIDR block for the VPC"
}
variable "enable_nat_gateway" {
type = bool
description = "Enable NAT Gateway for private subnets"
default = true
}
# Clear outputs
output "vpc_id" {
description = "ID of the VPC"
value = aws_vpc.main.id
}
output "public_subnet_ids" {
description = "List of public subnet IDs"
value = aws_subnet.public[*].id
}
Troubleshooting Common Issues
1. Provider Configuration Issues
# Error: Provider configuration not found
# Solution: Ensure provider is declared
terraform {
required_providers {
aws = {
source = "hashicorp/aws"
version = "~> 5.0"
}
}
}
provider "aws" {
region = var.aws_region
}
2. State File Conflicts
# Error: Error acquiring the state lock
# Solution: Release lock or wait for completion
terraform force-unlock LOCK_ID
# Check current state
terraform state list
# Backup state before major changes
cp terraform.tfstate terraform.tfstate.backup
3. Resource Dependencies
# Error: Resource depends on resource that cannot be determined
# Solution: Use explicit depends_on
resource "aws_instance" "web" {
# ...
depends_on = [aws_internet_gateway.main]
}
4. Variable Validation Errors
# Error: Invalid value for variable
# Solution: Check variable constraints
variable "environment" {
validation {
condition = contains(["dev", "staging", "prod"], var.environment)
error_message = "Environment must be dev, staging, or prod."
}
}
Conclusion
Terraform fundamentally transforms infrastructure management by bringing software development practices to infrastructure provisioning. The ability to define, version, and automate infrastructure through declarative configuration files provides unprecedented consistency, reliability, and scalability for modern cloud operations.
Key Achievements:
- Infrastructure as Code: Complete infrastructure definitions in version-controlled files
- Multi-Cloud Portability: Consistent patterns across AWS, GCP, Azure, and hybrid environments
- Automated Lifecycle Management: Planned changes with dependency resolution and rollback capabilities
- Team Collaboration: Git-based workflows with state management and conflict resolution
Operational Benefits:
- Consistency: Identical infrastructure across environments eliminates configuration drift
- Scalability: Module-based architecture supports enterprise-scale deployments
- Reliability: Plan-before-apply workflow prevents unexpected changes
- Governance: Built-in validation, tagging, and compliance enforcement
- Cost Control: Resource lifecycle management and optimization opportunities
Next Steps:
- Explore advanced Terraform features like dynamic blocks and for_each expressions
- Implement comprehensive module libraries for common infrastructure patterns
- Integrate Terraform with CI/CD pipelines for automated infrastructure deployment
- Establish governance frameworks with policy-as-code using Sentinel or OPA
Mastering these Terraform fundamentals provides the foundation for scalable, maintainable, and reliable infrastructure automation. The combination of declarative configuration, state management, and extensive provider ecosystem makes Terraform an essential tool for modern DevOps and cloud engineering teams.
“Terraform transforms infrastructure from manual, error-prone processes into reliable, automated, and version-controlled systems that scale with your organization.”

Comments