14 min to read
Single Sign-On (SSO)
A comprehensive guide to SSO and authentication protocols
Overview
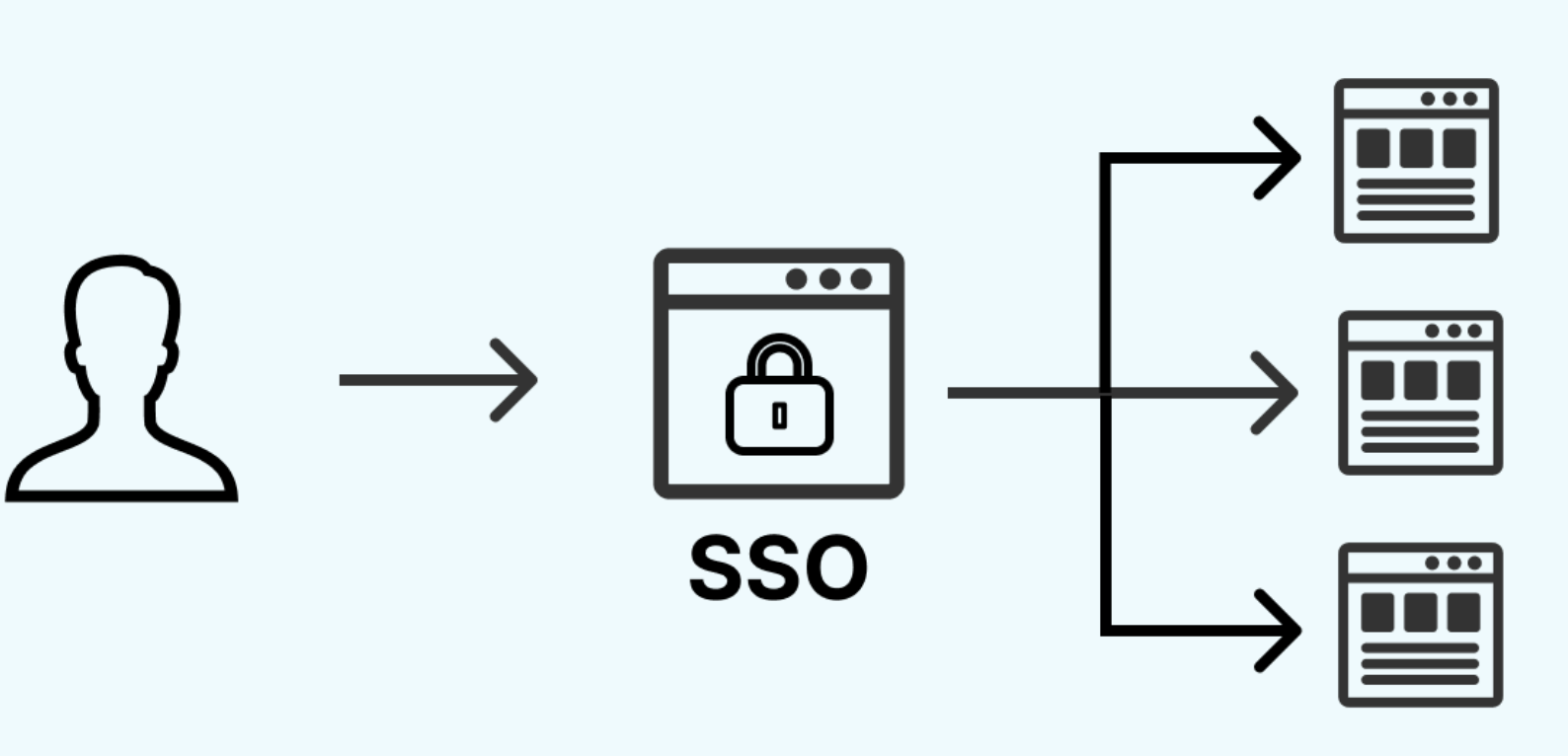
Single Sign-On (SSO) enables users to access multiple systems with a single authentication process.
In today’s interconnected digital environment, organizations typically manage multiple applications and services. Without SSO, users would need to remember and manage separate credentials for each system, leading to password fatigue and security vulnerabilities. SSO solves these challenges by providing a seamless authentication experience while improving security posture.
What is SSO?
Single Sign-On (SSO) is an authentication method that allows users to log in once and gain access to multiple applications and systems without being prompted to log in again for each application during the same session.
SSO is an authentication scheme that allows users to access multiple applications with one set of credentials. It:
- Improves user experience
- Reduces authentication complexity
- Enhances security
- Centralizes access management
- Identity Provider (IdP)The system that performs user authentication and provides identity information to service providers
- Service Provider (SP)Application or service that relies on the IdP for authentication
- Trust RelationshipThe established connection between IdP and SP, typically using certificates
- Directory ServiceStores user identities and attributes (e.g., Active Directory, LDAP)
- Authentication TokensSecurely carry identity information between systems
SSO vs. Federated Identity
While often used interchangeably, SSO and Federated Identity have distinct differences:
Single Sign-On (SSO):
- Provides access to multiple applications within the same organization
- Typically uses a single identity provider
- Focuses on authentication within organizational boundaries
Federated Identity:
- Extends authentication across different organizations
- Involves multiple identity providers
- Allows for cross-domain authentication
- Examples include using Google or Facebook to log into third-party websites
Key Benefits
SSO offers numerous advantages for both users and organizations:
1. Enhanced User Experience
- Single login for multiple services
- Reduced password management
- Faster access to applications
- Lower frustration and support requests
2. Improved Security
- Centralized authentication
- Stronger password policies
- Reduced phishing vulnerability
- Easier implementation of MFA
3. Efficient Resource Management
- Centralized user management
- Simplified administration
- Reduced help desk costs
- Streamlined onboarding/offboarding
Business Impact
Organizations implementing SSO typically experience:
- 20-50% reduction in password-related IT support tickets
- 30-60 minutes saved per user per month from avoiding password resets and multiple logins
- 15-30% decrease in unauthorized access incidents due to better credential management
- Faster adoption of new applications due to seamless access
- Improved compliance posture through centralized authentication policies
SSO Implementation Models
There are several approaches to implementing SSO, each with distinct characteristics and use cases.
Web-Based SSO
The most common form of SSO, designed for web applications:
Characteristics:
- Browser-centric implementation
- Uses HTTP redirects, cookies, and tokens
- Supported by most modern authentication protocols
- Works across domains with proper configuration
Implementation Flow:
- User attempts to access a web application (service provider)
- Application redirects to identity provider for authentication
- User authenticates with the identity provider
- Identity provider issues a token or assertion
- User is redirected back to the application with the token
- Application verifies the token and grants access
Enterprise SSO
Enterprise SSO
Designed for large organizations with complex networks and application ecosystems, often integrating with existing directory services.
Characteristics:
- Integrates with corporate directory services (Active Directory, LDAP)
- Supports both legacy and modern applications
- Often includes advanced access policies and governance
- May incorporate privileged access management
- Typically uses SAML or Kerberos
Common Solutions:
- Okta
- Microsoft Azure AD/Entra ID
- Ping Identity
- OneLogin
- ForgeRock
Kerberos-Based SSO
A traditional SSO method used in Windows environments:
Characteristics:
- Based on ticket-granting system
- Works primarily within a single domain
- Integrated with Active Directory
- Limited support for web applications
- Uses symmetric key cryptography
Components:
- Key Distribution Center (KDC)
- Ticket Granting Service (TGS)
- Authentication Service (AS)
- Service Principals
Authentication Protocols
Modern SSO implementations rely on standard protocols to ensure interoperability, security, and broad support across platforms.
OAuth 2.0 (Open Authorization)
OAuth 2.0 is an authorization framework that enables third-party applications to obtain limited access to a user’s account on a server.
Purpose:
- Delegation of access rights
- Third-party application authentication
- API authorization
- Resource sharing without exposing credentials
Operation:
- Token-based authentication
- Resource owner authorization
- Defined access scopes
- Supports different grant types
Key Concepts:
- Resource Owner: The user who owns the protected resources
- Client: The application requesting access to resources
- Authorization Server: Issues access tokens after authenticating the resource owner
- Resource Server: Hosts the protected resources
- Access Token: Credentials used to access protected resources
- Refresh Token: Credentials used to obtain new access tokens
OAuth 2.0 Grant Types:
- Authorization Code: Used by web applications with server-side component
- Implicit: Simplified flow for browser-based applications (deprecated in OAuth 2.1)
- Resource Owner Password Credentials: Direct username/password authentication
- Client Credentials: Used for machine-to-machine communication
- Device Code: For devices with limited input capabilities
- Refresh Token: For obtaining new access tokens
SAML 2.0 (Security Assertion Markup Language)
SAML is an XML-based open standard for exchanging authentication and authorization data between an identity provider and a service provider.
Purpose:
- Enterprise SSO
- XML-based framework
- Identity provider communication
- Cross-domain authentication
- Attributes and entitlements sharing
Operation:
- IdP authentication
- SAML assertions (authentication, attribute, and authorization)
- Service provider validation
- XML Signatures and encryption
Key Components:
- Assertions: XML documents containing authentication statements, attribute statements, and authorization statements
- Protocols: Rules for requesting and exchanging assertions
- Bindings: Details on how SAML messages are transported (HTTP Redirect, HTTP POST, etc.)
- Profiles: Guidelines for using assertions, protocols, and bindings to support specific use cases
SAML Flows:
- IdP-Initiated Flow: Authentication process starts at the identity provider
- SP-Initiated Flow: Authentication process starts at the service provider (more common)
OIDC (OpenID Connect)
OpenID Connect is an identity layer on top of the OAuth 2.0 protocol that allows clients to verify the identity of end-users and obtain basic profile information.
Purpose:
- Identity layer over OAuth 2.0
- User authentication
- Profile information access
- Standardized identity verification
Operation:
- JWT-based ID tokens
- OAuth 2.0 extension
- RESTful implementation
- Standard claims about users
Key Components:
- ID Token: JWT containing claims about the authentication
- UserInfo Endpoint: RESTful endpoint to retrieve additional user claims
- Standard Claims: Pre-defined attributes like name, email, picture, etc.
- Discovery: JSON document describing the OpenID provider configuration
- Dynamic Registration: Allowing clients to register dynamically
OIDC Flows:
- Authorization Code Flow: Most secure, supports refresh tokens
- Implicit Flow: Simplified flow for browser-based apps (less secure)
- Hybrid Flow: Combines aspects of both Authorization Code and Implicit flows
JWT (JSON Web Tokens)
While not a standalone authentication protocol, JWTs are a critical component in modern authentication systems:
Characteristics:
- Compact, self-contained tokens for information transmission
- Digitally signed to ensure integrity
- Can be encrypted to ensure confidentiality
- Used in OAuth 2.0 and OIDC implementations
Structure:
- Header: Token type and signing algorithm
- Payload: Claims about the user and authentication
- Signature: Ensures the token hasn’t been altered
Example JWT:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.
eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.
SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c
Protocol Comparison
OAuth vs SAML vs OIDC Comparison
| Feature | OAuth 2.0 | SAML 2.0 | OIDC |
|---|---|---|---|
| Primary Use | Authorization | Enterprise SSO | Authentication |
| Format | JSON/JWT | XML | JSON/JWT |
| Complexity | Medium | High | Low |
| Modern Apps | Yes | Limited | Yes |
| Mobile Support | Good | Limited | Excellent |
| User Data | No (auth only) | Limited | Yes (ID token) |
| Enterprise Adoption | Medium | High | Growing |
| Implementation Complexity | Medium | High | Low |
Choosing the Right Protocol
Choose OAuth 2.0 when:
- You need to authorize third-party applications to access resources
- You're building an API that requires secure access
- You need fine-grained access control (scopes)
- User authentication is not the primary concern
Choose SAML 2.0 when:
- You need enterprise-grade SSO for web applications
- You're integrating with legacy systems
- You require complex attribute statements and entitlements
- You're working in a highly regulated industry with specific compliance requirements
Choose OpenID Connect when:
- You need both authentication and authorization
- You're building modern web or mobile applications
- You want standardized user profile information
- You need simpler implementation than SAML
- You want to leverage existing OAuth 2.0 infrastructure
Security Considerations
While SSO improves overall security posture, it also presents unique challenges and risks that must be addressed.
SSO Security Risks
Single Point of Failure:
- Compromise of the identity provider affects all connected applications
- Dependency on IdP availability
- Need for robust IdP security controls
Session Management:
- Long-lived sessions increase risk if compromised
- Need for appropriate timeout policies
- Secure token storage and transmission
Implementation Vulnerabilities:
- Improper validation of tokens/assertions
- Weak encryption or signature verification
- Missing or inadequate certificate validation
- Insecure communication channels
Security Best Practices
Protect the Identity Provider:
- Implement multi-factor authentication
- Regularly rotate signing keys and certificates
- Employ robust monitoring and alerting
- Use hardware security modules (HSMs) for key storage
Secure Token Handling:
- Validate all tokens and assertions
- Verify signatures and trust relationships
- Check expiration times and audience restrictions
- Implement proper token storage techniques
Session Management:
- Implement appropriate session timeouts
- Provide secure session termination (logout)
- Consider step-up authentication for sensitive operations
- Monitor for suspicious authentication patterns
Implementing SSO in Practice
Successfully implementing SSO requires careful planning, design, and execution.
Implementation Steps
- Assessment and Planning:
- Identify applications requiring SSO
- Select appropriate protocol(s)
- Define user directory strategy
- Establish security requirements
- Identity Provider Selection:
- Choose between cloud-based or on-premises solution
- Evaluate vendor offerings
- Consider scalability, features, and support
- Technical Implementation:
- Configure identity provider
- Establish trust relationships
- Integrate applications
- Configure authentication policies
- Testing and Validation:
- Verify authentication flows
- Test edge cases
- Conduct security assessment
- Perform load testing
- Deployment and Training:
- Plan phased rollout
- Prepare user communication
- Provide training and documentation
- Establish support procedures
- Legacy Application IntegrationApplications without native SSO support
- Mobile Application SupportAdapting web-centric protocols for mobile use
- Multi-Directory EnvironmentsMerging identities from multiple sources
- User ExperienceBalancing security with convenience
- Session SynchronizationManaging sessions across multiple applications
- Cross-Domain CookiesBrowser restrictions on third-party cookies
Real-World Implementation Examples
Example 1: Corporate SSO with SAML
<!-- Sample SAML Response -->
<samlp:Response ID="_8e8dc5f69a98cc4c1ff3427e5ce34606fd672f91e6" Version="2.0" IssueInstant="2023-01-10T21:33:37Z" Destination="https://sp.example.com/SAML2/SSO/POST" Consent="urn:oasis:names:tc:SAML:2.0:consent:unspecified" InResponseTo="_bec424fa5103428909a30ff1e31168327f79474984">
<Issuer>https://idp.example.org/SAML2</Issuer>
<samlp:Status>
<samlp:StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:Success"/>
</samlp:Status>
<Assertion ID="_a75adf55-01d7-40cc-929f-dbd8372ebdfc" IssueInstant="2023-01-10T21:33:37Z" Version="2.0">
<Issuer>https://idp.example.org/SAML2</Issuer>
<Subject>
<NameID Format="urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress">j.doe@example.org</NameID>
<SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer">
<SubjectConfirmationData InResponseTo="_bec424fa5103428909a30ff1e31168327f79474984" NotOnOrAfter="2023-01-10T21:38:37Z" Recipient="https://sp.example.com/SAML2/SSO/POST"/>
</SubjectConfirmation>
</Subject>
<Conditions NotBefore="2023-01-10T21:33:37Z" NotOnOrAfter="2023-01-10T21:38:37Z">
<AudienceRestriction>
<Audience>https://sp.example.com/SAML2</Audience>
</AudienceRestriction>
</Conditions>
<AuthnStatement AuthnInstant="2023-01-10T21:33:37Z" SessionIndex="_be9967abd904ddcae3c0eb4189adbe3f71e327cf93">
<AuthnContext>
<AuthnContextClassRef>urn:oasis:names:tc:SAML:2.0:ac:classes:Password</AuthnContextClassRef>
</AuthnContext>
</AuthnStatement>
</Assertion>
</samlp:Response>
Example 2: OIDC Implementation
// OpenID Connect Authorization Request
const authorizationRequest = {
client_id: 'CLIENT_ID',
response_type: 'code',
scope: 'openid profile email',
redirect_uri: 'https://client.example.org/callback',
state: 'af0ifjsldkj',
nonce: 'n-0S6_WzA2Mj'
};
// URL with query parameters
const authUrl = 'https://auth.example.com/authorize?' +
new URLSearchParams(authorizationRequest).toString();
// After authorization, exchange code for tokens
async function exchangeCodeForTokens(authorizationCode) {
const tokenRequest = {
grant_type: 'authorization_code',
code: authorizationCode,
redirect_uri: 'https://client.example.org/callback',
client_id: 'CLIENT_ID',
client_secret: 'CLIENT_SECRET'
};
const response = await fetch('https://auth.example.com/token', {
method: 'POST',
headers: { 'Content-Type': 'application/x-www-form-urlencoded' },
body: new URLSearchParams(tokenRequest).toString()
});
return response.json();
// Returns { access_token, id_token, token_type, expires_in }
}
Advanced SSO Concepts
Multi-Factor Authentication (MFA) with SSO
Combining MFA with SSO enhances security while maintaining usability:
Integration Approaches:
- MFA during initial SSO authentication
- Risk-based MFA (adaptive authentication)
- Step-up authentication for sensitive applications
- Per-service MFA requirements
Common MFA Methods:
- Time-based one-time passwords (TOTP)
- Push notifications to mobile devices
- Biometric authentication
- Hardware security keys (FIDO2/WebAuthn)
Single Sign-Out and Session Management
Properly managing the end of user sessions is critical:
Single Logout Challenges:
- Terminating sessions across multiple applications
- Different session mechanisms per application
- Frontend vs. backend session termination
- Handling offline applications
Implementation Strategies:
- Front-channel logout (redirects)
- Back-channel logout (server-to-server)
- Logout tokens (OIDC)
- Session tracking and forced expiration
Access Governance and Compliance
SSO centralization creates opportunities for improved governance:
Capabilities:
- Centralized access reviews
- Detailed authentication logs
- Compliance reporting
- Access certification
- Just-in-time access provisioning
Future of SSO
Authentication technology continues to evolve to meet changing security requirements and user experience demands.
Emerging Trends
Passwordless Authentication:
- Biometric authentication
- Device-based authentication
- FIDO2 and WebAuthn standards
- One-time links and magic links
Zero Trust Architecture:
- Continuous authentication
- Context-aware access policies
- Device trust evaluation
- Micro-segmentation
Decentralized Identity:
- Self-sovereign identity (SSI)
- Blockchain-based authentication
- Verifiable credentials
- Portable identity across organizations
- PastProprietary solutions, Kerberos, early SAML
- PresentOAuth 2.0, OIDC, SAML 2.0, MFA integration
- Near FuturePasswordless, continuous authentication, enhanced biometrics
- Long-term FutureDecentralized identity, self-sovereign identity, AI-driven authentication

Comments