14 min to read
Network Address Translation (NAT)
A comprehensive guide to NAT, SNAT, and DNAT
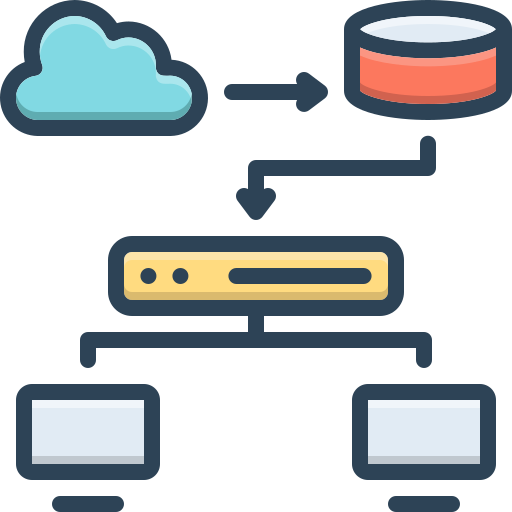
Overview
Network Address Translation (NAT) is a crucial networking technology that enables address translation between private and public networks.
NAT was developed as a solution to the IPv4 address exhaustion problem, allowing multiple devices on a local network to share a single public IP address. Beyond addressing IP shortages, NAT has evolved to become an essential component in network security and topology designs.
What is NAT?
Network Address Translation (NAT) is a method of remapping one IP address space into another by modifying network address information in the IP header of packets while they are in transit across a traffic routing device.
NAT converts network addresses from one type to another, primarily used to:
- Solve IP address shortage
- Protect internal networks
- Enable multiple devices to share one public IP
- Hide internal network structure
NAT typically works with the following private IP address ranges defined in RFC 1918:
- Class A: 10.0.0.0 to 10.255.255.255 (10.0.0.0/8)
- Class B: 172.16.0.0 to 172.31.255.255 (172.16.0.0/12)
- Class C: 192.168.0.0 to 192.168.255.255 (192.168.0.0/16)
These private addresses are not routable on the public internet and must be translated to public IP addresses for internet communication.
How NAT Works
NAT operates by maintaining a translation table that maps private IP addresses and ports to one or more public IP addresses and ports. When a device from the private network sends a packet to an external destination:
- The NAT device receives the packet
- It replaces the private source IP address with its public IP address
- It creates an entry in its translation table to track the connection
- It forwards the modified packet to the destination
When a response comes back:
- The NAT device receives the packet addressed to its public IP
- It looks up the destination port in its translation table
- It determines which internal device the packet should go to
- It replaces the destination IP with the internal device’s private IP
- It forwards the modified packet to the internal device
NAT Types
NAT implementations vary based on requirements, network design, and the level of control needed. Each type has specific use cases and advantages.
Static NAT
Static NAT establishes a one-to-one mapping between a private IP address and a public IP address. This mapping remains constant and is typically configured manually.
Characteristics:
- One-to-one mapping between private and public IP addresses
- Permanent, fixed relationship
- Each internal host requires a dedicated public IP address
- Useful when internal devices need consistent public addressing
Use Cases:
- Hosting internal servers that need to be accessible from the internet (web servers, mail servers)
- VoIP services that require consistent end-to-end addressing
- FTP servers and other services that open multiple connections
Example Configuration (Cisco IOS):
Router(config)# ip nat inside source static 192.168.1.10 203.0.113.5
Router(config)# interface GigabitEthernet0/0
Router(config-if)# ip nat inside
Router(config)# interface GigabitEthernet0/1
Router(config-if)# ip nat outside
Dynamic NAT
Dynamic NAT automatically maps private IP addresses to a pool of public IP addresses. Unlike static NAT, the mappings are not permanent and are created as needed.
Characteristics:
- Maps private IP addresses to a pool of public IP addresses
- No guaranteed consistent mapping (addresses are assigned from the pool as needed)
- Number of simultaneous connections limited by size of public IP pool
- Mappings timeout after periods of inactivity
Use Cases:
- When multiple internal hosts need internet access but don’t require consistent public addressing
- Organizations with a small pool of public IPs that need to be shared
- Testing environments where consistent public addressing isn’t required
Example Configuration (Cisco IOS):
Router(config)# ip nat pool public-pool 203.0.113.10 203.0.113.20 netmask 255.255.255.0
Router(config)# access-list 1 permit 192.168.1.0 0.0.0.255
Router(config)# ip nat inside source list 1 pool public-pool
Router(config)# interface GigabitEthernet0/0
Router(config-if)# ip nat inside
Router(config)# interface GigabitEthernet0/1
Router(config-if)# ip nat outside
PAT (Port Address Translation)
PAT, also known as NAT Overload, is the most common form of NAT used in home and small business networks. It maps multiple private IP addresses to a single public IP address by using different ports.
Characteristics:
- Many-to-one mapping (many private IPs to one public IP)
- Uses different source port numbers to distinguish between translations
- Most efficient use of public IP addresses
- Also called NAT Overload or NAPT (Network Address Port Translation)
Use Cases:
- Home networks sharing a single ISP-provided IP address
- Small to medium businesses with limited public IP allocations
- Any scenario where conserving public IP addresses is important
Example Configuration (Cisco IOS):
Router(config)# access-list 1 permit 192.168.1.0 0.0.0.255
Router(config)# ip nat inside source list 1 interface GigabitEthernet0/1 overload
Router(config)# interface GigabitEthernet0/0
Router(config-if)# ip nat inside
Router(config)# interface GigabitEthernet0/1
Router(config-if)# ip nat outside
Advanced NAT Types
Beyond the basic NAT types, there are specialized implementations for specific use cases. Source NAT and Destination NAT are particularly important in enterprise and service provider networks.
SNAT (Source NAT)
Source NAT modifies the source address of packets as they pass through the NAT device. This is the most common implementation of NAT used for outbound connections from a private network to the internet.
Purpose:
- Translates source IP for outbound traffic
- Enables internal network access to internet
- Manages port translation
- Masks internal network structure
Key Concepts:
- Primarily used for outbound connections
- Can use a single public IP address (PAT) or a pool of addresses
- Maintains a translation table tracking connections
- Internal hosts initiate connections; external hosts respond to those connections
Implementation:
# Linux iptables SNAT example
iptables -t nat -A POSTROUTING -o eth0 -j SNAT --to-source 198.51.100.1
# Or using masquerade (dynamic source IP)
iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
DNAT (Destination NAT)
DNAT modifies the destination address of packets passing through the NAT device. This is commonly used to forward incoming connections from the internet to specific servers on the internal network.
Purpose:
- Translates destination IP for inbound traffic
- Enables port forwarding
- Manages external access to internal servers
- Provides “reverse proxy” functionality at the network layer
Key Concepts:
- Used for inbound connections from external networks
- Allows specific services to be exposed to the internet
- Can translate both IP addresses and ports
- External clients connect to a public IP; connections are forwarded to internal servers
Implementation:
# Linux iptables DNAT example (port forwarding)
iptables -t nat -A PREROUTING -i eth0 -p tcp --dport 80 -j DNAT --to-destination 192.168.1.100:80
# Port redirection example (forwarding external port 8080 to internal port 80)
iptables -t nat -A PREROUTING -i eth0 -p tcp --dport 8080 -j DNAT --to-destination 192.168.1.100:80
Bidirectional NAT
Bidirectional NAT, also called “hairpin NAT” or “NAT loopback,” allows clients on the internal network to access internal servers using the public (external) IP address.
Characteristics:
- Allows internal clients to reach internal servers via public IP
- Requires specialized NAT configuration
- Especially useful in single-firewall environments
Example Implementation:
# Linux NAT loopback (using iptables)
iptables -t nat -A PREROUTING -d 198.51.100.1 -p tcp --dport 80 -j DNAT --to-destination 192.168.1.100:80
iptables -t nat -A POSTROUTING -s 192.168.1.0/24 -d 192.168.1.100 -p tcp --dport 80 -j SNAT --to-source 192.168.1.1
NAT Workflow Example
| Component | Private IP | Public IP |
|---|---|---|
| Internal Client | 192.168.1.100 | - |
| NAT Device | 192.168.1.1 | 198.51.100.1 |
| External Client | - | 203.0.113.50 |
| Internal Server | 192.168.1.200 | - |
Explanation
- Internal Client: Uses a private IP (192.168.1.100) within the local network and doesn’t have a public IP.
- NAT Device: Acts as a bridge between internal and external networks, translating private IPs to its public IP (198.51.100.1).
- External Client: Has a public IP (203.0.113.50) and can access external networks directly.
- Internal Server: Like the client, it has a private IP (192.168.1.200) and is isolated from public access.
SNAT Process
When an internal client communicates with an external server, the NAT device performs Source NAT:
- The internal client (192.168.1.100) sends a packet to a web server (203.0.113.50)
- The packet reaches the NAT device
- The NAT device records the connection in its translation table
- The NAT device changes the source IP and port
- The modified packet travels to the destination
- The destination responds to the NAT device’s public IP
- The NAT device uses its translation table to forward the response to the internal client
Original Packet:
Source: 192.168.1.100:12345
Destination: 203.0.113.50:80
Translated Packet:
Source: 198.51.100.1:54321
Destination: 203.0.113.50:80
| Source IP:Port | NAT IP:Port | Destination IP:Port |
|---|---|---|
| 192.168.1.100:12345 | 198.51.100.1:54321 | 203.0.113.50:80 |
DNAT Process
When an external client wants to access an internal server (port forwarding):
- The external client (203.0.113.50) sends a packet to the NAT device’s public IP
- The packet reaches the NAT device
- The NAT device identifies this as a forwarded service
- The NAT device changes the destination IP (and possibly port)
- The modified packet is forwarded to the internal server
- The internal server responds to the NAT device
- The NAT device translates the source IP back to its public IP
- The response returns to the external client
Original Packet:
Source: 203.0.113.50:44321
Destination: 198.51.100.1:80
Translated Packet:
Source: 203.0.113.50:44321
Destination: 192.168.1.200:80
NAT in Different Environments
NAT implementations vary across different environments and network devices. Understanding these implementations helps in effective network design and troubleshooting.
NAT in Home Networks
In home networks, NAT is typically implemented in consumer routers/gateways and provides basic internet connectivity for multiple devices.
Characteristics:
- Usually implements PAT/NAT Overload
- Simple configuration through router web interface
- Often combined with DHCP and basic firewall
- Limited port forwarding capabilities
Common Configurations:
- Port forwarding for gaming consoles
- DMZ host for a single device to receive all inbound connections
- UPnP for automatic port forwarding
NAT in Enterprise Networks
Enterprise networks often implement more complex NAT scenarios to accommodate business requirements while maintaining security.
Common Implementations:
- Multiple public IP addresses and NAT pools
- Policy-based NAT for different departments or applications
- Integration with firewall security policies
- High-availability NAT configurations
- NAT with load balancing for inbound connections
Technologies:
- Dedicated firewall/NAT appliances (Cisco ASA, Palo Alto, Fortinet)
- Software-defined networking with NAT functionality
- Load balancers providing NAT services
NAT in Cloud Environments
Cloud providers offer various NAT implementations to support different architectural patterns:
AWS NAT Solutions:
- NAT Gateways: Managed NAT service for outbound internet connectivity
- Internet Gateways: Provide direct internet access with public IPs
- Load Balancers: Perform DNAT to route traffic to backend instances
Azure NAT Solutions:
- Virtual Network NAT: Outbound connectivity for private resources
- Load Balancers: Inbound NAT rules for forwarding traffic
- Public IP addresses: Direct assignment to resources
Google Cloud NAT Solutions:
- Cloud NAT: Managed NAT service for outbound access
- External IP addresses: Direct assignment to resources
- Load balancers: Layer 4 and Layer 7 NAT functionality
NAT Security Considerations
While NAT provides some inherent security benefits, it’s important to understand its limitations and proper implementation from a security perspective.
Security Benefits of NAT
Network Hiding:
- Internal IP addresses and topology are hidden
- Reduces attack surface by concealing internal structure
- Adds a layer of obscurity
Connection State Tracking:
- Only allows incoming connections that correspond to outgoing requests
- Acts as a basic stateful firewall
- Blocks unsolicited inbound connections
Security Limitations
Not a Firewall Replacement:
- NAT alone is not sufficient for network security
- Should be combined with proper firewall rules and security practices
- Port forwarding can introduce vulnerabilities if not properly secured
Protocol Compatibility Issues:
- Some protocols work poorly with NAT (IPsec, FTP, SIP, etc.)
- Application Layer Gateways (ALGs) required for certain protocols
- Can create unexpected security gaps
NAT Best Practices for Security
- Use NAT in conjunction with a properly configured firewall
- Only forward necessary ports to internal servers
- Implement least privilege principle for port forwarding
- Regularly audit NAT and port forwarding rules
- Consider using a DMZ for public-facing servers
- Monitor NAT translation logs for unusual activity
- Keep NAT device software and firmware updated
NAT Troubleshooting
NAT issues can be complex to troubleshoot due to the connection state tracking and address translation involved. Here are some common issues and their resolutions.
Common NAT Problems
Asymmetric Routing:
- Packets take different paths through different NAT devices
- Solution: Ensure routing design provides symmetric paths
Connection Tracking Table Full:
- NAT device cannot handle additional connections
- Solution: Increase connection table size or implement connection limits
Protocol Compatibility:
- Certain protocols may not work correctly through NAT
- Solution: Implement protocol-specific ALGs or use alternative protocols
Troubleshooting Commands
Linux NAT Troubleshooting:
# View NAT translation table
cat /proc/net/nf_conntrack
# Check iptables NAT rules
iptables -t nat -L -v -n
# Monitor NAT operations
tcpdump -i eth0 -n
# Check routing
ip route show
Cisco NAT Troubleshooting:
# View NAT translations
show ip nat translations
show ip nat translations verbose
# View NAT statistics
show ip nat statistics
# Debug NAT operations
debug ip nat detailed
Diagnosing NAT Issues
- Verify Basic Connectivity: Ensure internal and external connectivity works
- Check NAT Configuration: Verify NAT rules are correctly configured
- Examine Translation Table: Look for expected translations in the NAT table
- Packet Capture: Capture traffic before and after NAT to see transformations
- Analyze Logs: Check for error messages related to NAT
- Test with Simple Protocol: Use basic protocols like ICMP or HTTP first
- Verify State: Ensure connection tracking is working properly
NAT and IPv6
As IPv6 adoption increases, the role of NAT is changing. IPv6 provides a vast address space that technically eliminates the need for NAT, but transitional mechanisms and security considerations have led to various IPv6 NAT implementations.
IPv6 and the Future of NAT
IPv6 Address Space:
- 128-bit addresses (340 undecillion addresses)
- Sufficient to give every device a unique public address
- Theoretically eliminates the primary need for NAT
NAT in IPv6 Environments:
- NAT66: IPv6-to-IPv6 address translation (less common)
- NPTv6 (Network Prefix Translation): Translates IPv6 prefixes
- NAT64: Facilitates communication between IPv6 and IPv4 networks
Transitional Technologies
Dual Stack:
- Devices run both IPv4 and IPv6 simultaneously
- Traditional NAT used for IPv4; direct addressing for IPv6
- Most common current implementation
IPv6 Tunneling:
- Encapsulates IPv6 packets within IPv4 packets
- Examples: 6to4, Teredo, ISATAP
- Often used where native IPv6 is unavailable

Comments