13 min to read
Understanding IPsec vs SSL/TLS - Network Security Protocols
A comprehensive comparison of IPsec and SSL/TLS protocols
Overview
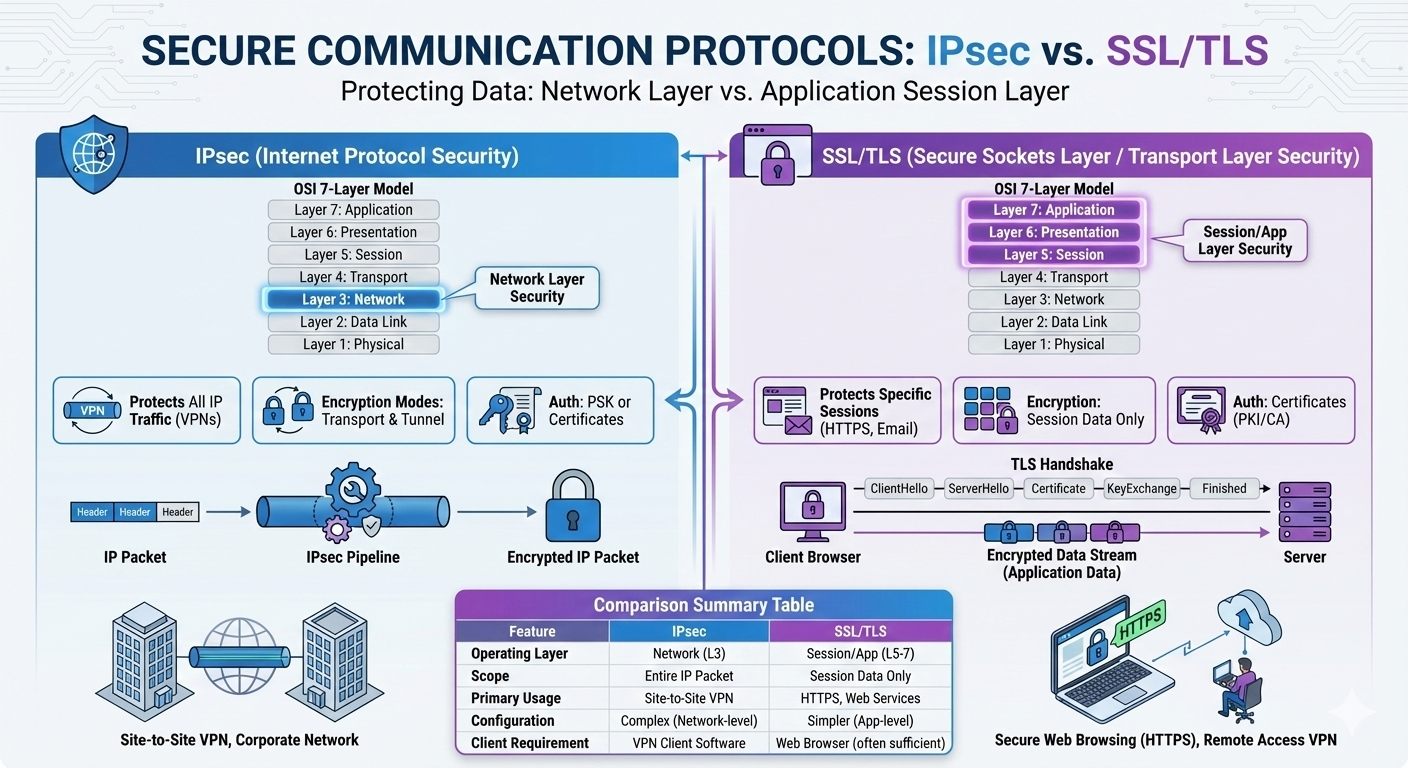
IPsec and SSL/TLS are both protocols used for securing network traffic, operating at different layers of the network stack.
Network security protocols are essential for protecting data as it travels across networks, whether internal corporate networks or the public internet. This article provides a comprehensive comparison of two major security protocol suites: IPsec and SSL/TLS, examining their architectures, strengths, weaknesses, and appropriate use cases.
IPsec (Internet Protocol Security)
Internet Protocol Security (IPsec) is a protocol suite that secures Internet Protocol (IP) communications by authenticating and encrypting each IP packet in a data stream.
IPsec was developed in the mid-1990s by the Internet Engineering Task Force (IETF) as part of the IPv6 standard, though it was later back-ported to IPv4. It was created to address fundamental security weaknesses in the IP protocol, which originally had no built-in security mechanisms.
The IPsec standards evolved through multiple iterations:
- First standardized in 1995 (RFC 1825-1829)
- Major update in 1998 (RFC 2401-2412)
- Revised again in 2005 (RFC 4301-4309)
- Latest updates focus on integration with modern encryption standards
Architecture and Components
IPsec consists of several distinct protocols that work together to provide a comprehensive security framework:
Security Protocols
- Authentication Header (AH)
- Provides integrity and authentication
- Does not provide encryption
- Protects against data tampering
- Defined in RFC 4302
- Encapsulating Security Payload (ESP)
- Provides confidentiality, authentication, and integrity
- Encrypts packet payload
- Can operate in tunnel or transport mode
- Defined in RFC 4303
Key Management
Internet Key Exchange (IKE)
- Negotiates security associations (SAs)
- Manages key exchange
- Handles mutual authentication
- IKEv2 (current version) streamlines the process with fewer message exchanges
Security Associations (SA)
Security Associations are fundamental to IPsec operations:
- Unidirectional logical connections between communicating parties
- Defined by source/destination, protocol, and Security Parameter Index (SPI)
- Contain encryption keys, algorithms, modes, and lifetimes
Modes of Operation
IPsec operates in two distinct modes, each serving different security purposes:
Transport Mode
In transport mode, IPsec protects the payload of IP packets but leaves the original IP header intact.
Characteristics:
- Only the payload is encrypted and/or authenticated
- Original IP header remains visible
- More efficient (less overhead)
- Typically used for host-to-host communications
Packet Structure:
Original IP Header | IPsec Header | Original Payload
Tunnel Mode
In tunnel mode, the entire original IP packet is encapsulated within a new IP packet with a new header.
Characteristics:
- Entire original packet (header and payload) is protected
- New IP header is added
- Higher overhead
- Typically used for network-to-network (gateway-to-gateway) or host-to-network communications
- Standard for VPN implementations
Packet Structure:
New IP Header | IPsec Header | Original IP Header | Original Payload
Authentication and Encryption
IPsec supports various authentication and encryption methods:
Authentication Methods
- Pre-Shared Keys (PSK): Simple shared secret
- RSA Signatures: Public key cryptography
- Extensible Authentication Protocol (EAP): Framework for various authentication types
- Digital Certificates: X.509 certificates
Encryption Algorithms
- AES-CBC: Advanced Encryption Standard in Cipher Block Chaining mode
- AES-GCM: AES in Galois/Counter Mode (provides authentication and encryption)
- ChaCha20-Poly1305: Modern AEAD (Authenticated Encryption with Associated Data) algorithm
Hash Algorithms
- SHA-256/384/512: Secure Hash Algorithms
- HMAC: Hash-based Message Authentication Code
Configuration Example
A basic IPsec configuration on a Cisco router might look like this:
! Define ISAKMP policy (IKE Phase 1)
crypto isakmp policy 10
authentication pre-share
encryption aes 256
hash sha256
group 14
lifetime 86400
! Define pre-shared key
crypto isakmp key STRONG-SECRET-KEY address 203.0.113.2
! Define IPsec transform set (IKE Phase 2)
crypto ipsec transform-set TS-ESP-AES-SHA esp-aes 256 esp-sha-hmac
mode tunnel
! Define crypto ACL to identify interesting traffic
access-list 101 permit ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
! Create a crypto map
crypto map SECURE-MAP 10 ipsec-isakmp
set peer 203.0.113.2
set transform-set TS-ESP-AES-SHA
match address 101
! Apply crypto map to outgoing interface
interface GigabitEthernet0/0
crypto map SECURE-MAP
SSL/TLS (Secure Sockets Layer/Transport Layer Security)
SSL/TLS is a protocol suite that provides secure communication over a computer network, typically between web browsers and servers, though it can be used for other applications as well.
The protocol has evolved significantly since its inception:
- SSL 1.0: Developed by Netscape, never publicly released (1994)
- SSL 2.0: Released but had serious security flaws (1995)
- SSL 3.0: Redesigned to address security issues (1996)
- TLS 1.0: First IETF standardized version (RFC 2246, 1999)
- TLS 1.1: Protection against CBC attacks (RFC 4346, 2006)
- TLS 1.2: Improved security, stronger crypto (RFC 5246, 2008)
- TLS 1.3: Major redesign, faster handshakes, better security (RFC 8446, 2018)
SSL is now deprecated due to security vulnerabilities, and TLS is the current standard.
Architecture and Components
TLS consists of two main layers:
TLS Record Protocol
The lower-level component that provides:
- Connection security
- Encapsulation of higher-level protocols
- Compression (optional)
- Message integrity
- Encryption
TLS Handshake Protocol
The higher-level component that establishes the secure connection:
- Authenticates server (and optionally client)
- Negotiates cryptographic parameters
- Establishes shared secret keys
- Enables secure communication
Key TLS Components
- Certificates: X.509 digital certificates containing public keys and identity information
- Cipher Suites: Combinations of encryption, authentication, and key exchange algorithms
- Session Keys: Temporary symmetric keys used for bulk data encryption
- Certificate Authorities (CAs): Trusted third parties that issue digital certificates
client certificate Server->>Client: ServerHelloDone Client->>Client: Verify certificate Client->>Server: ClientKeyExchange (premaster secret) Client->>Server: ChangeCipherSpec Client->>Server: Finished (encrypted) Server->>Server: Generate session keys Server->>Client: ChangeCipherSpec Server->>Client: Finished (encrypted) Note over Client,Server: Secure Communication Begins
TLS 1.3 Improvements
TLS 1.3 introduced significant improvements over previous versions:
- Reduced Handshake Latency: 1-RTT (Round Trip Time) handshakes, with 0-RTT resumption option
- Removed Legacy Cryptography: Eliminated vulnerable algorithms (MD5, SHA-1, RC4, DES)
- Simplified Cipher Suite Negotiation: Separated key exchange from cipher suite
- Forward Secrecy by Default: Requires ephemeral key exchange methods
- Encrypted Handshake Messages: Improved privacy by encrypting more of the handshake
Implementation Example
A basic HTTPS server configuration in Node.js using TLS:
const https = require('https');
const fs = require('fs');
// Read TLS certificate and key
const options = {
key: fs.readFileSync('server-key.pem'),
cert: fs.readFileSync('server-cert.pem'),
// Modern secure configuration
ciphers: 'TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:TLS_AES_128_GCM_SHA256',
minVersion: 'TLSv1.2'
};
// Create HTTPS server
https.createServer(options, (req, res) => {
res.writeHead(200, {'Content-Type': 'text/plain'});
res.end('Secure Connection Established\n');
}).listen(443, () => {
console.log('Server running on https://localhost:443/');
});
An Nginx server configuration with strong TLS settings:
server {
listen 443 ssl http2;
server_name example.com;
ssl_certificate /etc/nginx/ssl/example.com.crt;
ssl_certificate_key /etc/nginx/ssl/example.com.key;
# Modern TLS configuration
ssl_protocols TLSv1.2 TLSv1.3;
ssl_prefer_server_ciphers on;
ssl_ciphers ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305;
# Improve security
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 10m;
ssl_session_tickets off;
# HSTS (6 months)
add_header Strict-Transport-Security "max-age=15768000" always;
# OCSP Stapling
ssl_stapling on;
ssl_stapling_verify on;
# Root directory and logs
root /var/www/example.com;
access_log /var/log/nginx/example.com.access.log;
error_log /var/log/nginx/example.com.error.log;
}
IPsec vs SSL/TLS Comparison
| Feature | IPsec | SSL/TLS |
|---|---|---|
| OSI Layer | Network (Layer 3) | Session/Presentation (Layers 5-6) |
| Primary Function | Secure IP packets | Secure application data |
| Security Scope | Full packet encryption | Session data encryption |
| Typical Usage | VPNs, site-to-site connections | Web browsers, application security |
| Authentication | Multiple methods (PSK, certificates) | Primarily CA certificates |
| Configuration | Complex, network-level | Relatively simpler, application-level |
| Transparency | Transparent to applications | Requires application support |
| Implementation | Network-level, OS support required | Application layer, library implementation |
| NAT Compatibility | Problematic (esp. with AH), requires NAT-T | Excellent |
| Firewall Traversal | Often blocked, requires specific rules | Typically allowed (port 443) |
VPN Technologies
Both IPsec and SSL/TLS are commonly used for creating Virtual Private Networks (VPNs), but they differ significantly in implementation and use cases.
IPsec VPN
IPsec VPNs provide secure network-to-network or client-to-network connectivity at the IP layer.
Types of IPsec VPNs
- Site-to-Site VPN
- Connects entire networks together
- Typically implemented between firewalls or routers
- Transparent to end users
- Ideal for connecting branch offices to headquarters
- Remote Access VPN
- Connects individual clients to a private network
- Requires VPN client software
- Provides full network integration
- Suitable for employees requiring complete network access
Implementation Considerations
- Hardware Requirements: Dedicated VPN concentrators or firewalls
- Client Software: Required on end-user devices
- Network Integration: Deep integration with existing network infrastructure
- Performance: Can handle high throughput with hardware acceleration
- Administrative Overhead: Substantial for large deployments
SSL/TLS VPN
SSL/TLS VPNs operate at the application layer and are typically easier to deploy for remote access scenarios.
Types of SSL/TLS VPNs
- Portal VPN
- Web-based interface for accessing specific applications
- No full network integration
- Application proxying
- Often includes file sharing, webmail, and web-based applications
- Tunnel VPN
- Similar to IPsec remote access but using SSL/TLS
- Can provide network-level access
- Usually more selective about traffic routing
- Often implements split tunneling
Implementation Advantages
- Browser-Based Access: Often requires only a web browser
- Ease of Deployment: Minimal client configuration
- Firewall Friendliness: Uses standard web ports (443)
- Granular Access Control: Can limit access to specific applications
- Clientless Options: Portal VPNs may not require any client installation
Split tunneling is a VPN configuration that allows a remote user to access a secure network and the public internet simultaneously through the same physical connection, but with different logical routes.
Advantages:- Reduces bandwidth consumption on the corporate network
- Improves performance for internet access
- Reduces latency for cloud services
- Creates potential attack vectors if user's device is compromised
- May violate compliance requirements in regulated industries
- Complicates network monitoring and traffic inspection
Security Considerations
IPsec Security Strengths and Concerns
Strengths:
- Comprehensive packet protection
- OS-level implementation (difficult to subvert)
- Protected against traffic analysis
- Strong authentication options
- Well-suited for securing infrastructure
Concerns:
- Complexity increases chance of misconfiguration
- Implementation variations can cause interoperability issues
- Key management can be challenging
- Some legacy implementations have vulnerabilities
- Resource-intensive (especially on lower-end devices)
SSL/TLS Security Strengths and Concerns
Strengths:
- Wide adoption and implementation
- Regular updates and improvements
- Flexible deployment options
- Strong modern cipher support
- Built-in trust model with CAs
Concerns:
- Certificate management challenges
- PKI trust issues (compromised CAs)
- Dependency on application implementation
- Historical vulnerabilities (BEAST, POODLE, Heartbleed)
- Not designed to protect entire network traffic
Detailed Technical Comparison
| Technical Aspect | IPsec | SSL/TLS |
|---|---|---|
| Protocol Support | All IP-based protocols (TCP, UDP, ICMP, etc.) | Primarily TCP (with DTLS for UDP) |
| Implementation Level | Operating system kernel | Application or library |
| Client Configuration | Complex, requires dedicated setup | Often minimal or browser-based |
| Addressing Model | Network layer (IP addresses) | Application layer (URLs, hostnames) |
| Key Exchange | IKE (Internet Key Exchange) | TLS Handshake Protocol |
| User Experience | Transparent but requires client installation | Often integrated into familiar applications |
| Deployment Complexity | High (network infrastructure changes) | Medium (application configuration) |
| Ideal Use Case | Connecting entire networks securely | Securing specific application traffic |
Use Case Selection Guide
When to Choose IPsec
IPsec is typically the better choice when:
- Securing Entire Networks: Connecting branch offices or data centers
- Protocol Diversity: Need to secure non-TCP protocols
- Transparency Required: Applications shouldn’t need modification
- Hardware Support Available: Network devices with IPsec acceleration
- Strict Security Requirements: Defense-in-depth approach needed
- Site-to-Site Connectivity: Permanent secure tunnels between locations
When to Choose SSL/TLS
SSL/TLS is typically the better choice when:
- Application-Specific Security: Protecting specific services
- Remote User Access: Users need access from varied locations/devices
- Simplified Deployment: Minimal infrastructure changes desired
- Firewall/NAT Traversal: Working in restricted network environments
- Granular Access Control: Need to secure specific applications, not entire networks
- Public Services: Securing public-facing web applications
Many organizations implement both technologies for different purposes:
- IPsec for site-to-site network connections between offices
- SSL/TLS VPN for employee remote access
- HTTPS (TLS) for securing public web applications
- Application-level TLS for internal service communications
This layered approach provides defense in depth and optimizes each protocol for its strengths.
Future Trends
IPsec Evolution
- Integration with Software-Defined Networking (SDN)
- Improved performance through hardware acceleration
- Better IPv6 support and implementation
- Simplified configuration through automation
- Enhanced with quantum-resistant algorithms
SSL/TLS Evolution
- Continued improvements in TLS 1.3 adoption
- Post-quantum cryptography integration
- Encrypted Client Hello (ECH) for enhanced privacy
- Certificate Transparency expansion
- Increased use of DTLS for real-time applications


Comments