24 min to read
Enterprise GitHub Actions Self-Hosted Runners: Production-Grade Kubernetes Deployment
Complete guide to implementing scalable, secure, and production-ready GitHub Actions runners on Kubernetes with advanced patterns
Overview
GitHub Actions Self-Hosted Runners represent a paradigm shift in enterprise CI/CD infrastructure, enabling organizations to transcend the limitations of GitHub-hosted runners while maintaining complete control over their build environments.
In today’s cloud-native landscape, enterprises demand CI/CD infrastructure that can seamlessly scale from development teams to global organizations while ensuring security, compliance, and cost optimization.
This comprehensive guide explores the enterprise implementation of GitHub Actions self-hosted runners on Kubernetes, covering advanced deployment patterns, security hardening, performance optimization, and operational excellence practices.
Whether you’re building CI/CD infrastructure for a startup or orchestrating deployments across a global enterprise, this guide provides the depth and practical insights needed for production-ready implementations.
Enterprise Architecture Deep Dive
Modern enterprise CI/CD environments require sophisticated runner management that can handle diverse workloads, security requirements, and scaling demands. GitHub Actions self-hosted runners on Kubernetes provide the foundation for building resilient, scalable, and secure CI/CD infrastructure.
Why Enterprise Self-Hosted Runners?
GitHub-Hosted Runner Limitations
While GitHub-hosted runners provide excellent out-of-the-box functionality, enterprise environments often encounter significant constraints:
Resource Constraints
- Limited to 2-core CPU and 7GB RAM for standard runners
- Maximum job execution time of 6 hours for public repositories, 35 minutes for private repositories (free plans)
- Restricted access to internal resources and private networks
Security and Compliance Gaps
- Limited control over the execution environment
- No ability to implement organization-specific security policies
- Challenges with compliance requirements (SOC 2, HIPAA, PCI DSS)
- Inability to use organization-specific security tools and scanning
Cost and Scale Considerations
- Per-minute billing can become expensive for high-volume CI/CD
- No cost predictability for large-scale operations
- Limited parallel job execution (20 jobs for free accounts, 180 for Pro)
Self-Hosted Runner Enterprise Advantages
Infrastructure Control
- Complete control over compute resources and specifications
- Ability to scale vertically and horizontally based on demand
- Custom network configurations and security policies
- Integration with existing enterprise infrastructure
Security and Compliance
- Full control over the execution environment
- Implementation of organization-specific security tools
- Compliance with enterprise security policies
- Private network access without exposing internal resources
Cost Optimization
- Predictable infrastructure costs
- Ability to optimize resource utilization
- No per-minute charges for CI/CD execution
- Shared infrastructure across multiple projects and teams
Performance and Customization
- Optimized environments for specific workloads
- Pre-configured tools and dependencies
- Faster build times through persistent caching
- Custom hardware configurations (GPU, high-memory instances)
Enterprise Architecture Components
Understanding GitHub Action Hosted Runners
Enterprise Components Deep Dive
- Kubernetes operator that manages GitHub Actions runners at enterprise scale
- Provides declarative configuration through Custom Resource Definitions (CRDs)
- Handles automatic provisioning, scaling, and lifecycle management
- Supports webhook-driven scaling for real-time responsiveness
- Integrates with Kubernetes RBAC and security policies
- Custom resource that defines runner groups with specific configurations
- Supports multiple scaling strategies (webhook, scheduled, metric-based)
- Enables workload-specific runner configurations
- Provides isolation between different teams and projects
- Supports both ephemeral and persistent runner patterns
- Maintains persistent connection with GitHub Actions service
- Receives webhook events for job queue changes
- Triggers scaling decisions based on workload demand
- Handles authentication and authorization with GitHub
- Provides metrics and observability for scaling operations
- Containerized environments that execute GitHub Actions workflows
- Support for custom container images with enterprise tools
- Integration with enterprise security and compliance tools
- Persistent volume support for caching and artifacts
- Network isolation and security policy enforcement
Enterprise Scaling Strategies
Webhook-Driven Scaling (Recommended for Production)
- Real-time scaling based on GitHub Actions job queue
- Sub-second response times for new job requests
- Optimal resource utilization and cost efficiency
- Requires proper webhook endpoint configuration and security
Scheduled Scaling
- Predictable scaling based on organizational patterns
- Ideal for known workload patterns (business hours, deployment windows)
- Combines with webhook scaling for hybrid approaches
- Supports timezone-aware scaling policies
Metric-Based Scaling
- CPU, memory, and custom metric-driven scaling
- Integration with Prometheus and Kubernetes HPA
- Suitable for long-running workflows and resource-intensive tasks
Metric-Based Scaling
- CPU, memory, and custom metric-driven scaling
- Integration with Prometheus and Kubernetes HPA
- Suitable for long-running workflows and resource-intensive tasks
- Provides granular control over scaling behavior
Enterprise Prerequisites and Planning
Infrastructure Requirements
Kubernetes Cluster Specifications
- Kubernetes 1.25+ with Container Runtime Interface (CRI) support
- Minimum 3 nodes for high availability (production environments)
- Resource allocation: 4 vCPU, 8GB RAM per node (baseline)
- Storage: 100GB+ per node for container images and build artifacts
- Network policies support for security isolation
- Load balancer integration for webhook endpoints
Enterprise Security Foundation
- RBAC-enabled Kubernetes cluster with proper service accounts
- Network policies for runner pod isolation
- Pod Security Standards (restricted profile recommended)
- Container image scanning and vulnerability management
- Secrets management integration (HashiCorp Vault, AWS Secrets Manager, etc.)
- Certificate management for webhook TLS termination
GitHub Enterprise Configuration
Organization-Level Setup
- GitHub Enterprise Server 3.5+ or GitHub.com Enterprise plan
- Organization admin privileges for runner registration
- GitHub App registration with appropriate permissions:
- Repository permissions: Actions (read), Administration (read), Metadata (read)
- Organization permissions: Self-hosted runners (write)
- Personal Access Token (PAT) with appropriate scopes (fallback authentication)
Repository and Team Structure
- Clear runner group definitions by team, project, or environment
- Repository-specific vs organization-wide runner strategies
- Workflow labeling conventions for runner targeting
- Access control and approval workflows for sensitive deployments
Network and Connectivity
Outbound Connectivity Requirements
- HTTPS access to GitHub.com (api.github.com, github.com)
- Container registry access (ghcr.io, docker.io, enterprise registries)
- Package manager repositories (npm, pip, maven, etc.)
- Cloud provider APIs for infrastructure provisioning
- Internal enterprise services and APIs
Webhook Endpoint Configuration
- Publicly accessible HTTPS endpoint for GitHub webhooks
- TLS certificate from trusted CA
- Network path from GitHub.com to Kubernetes cluster
- Load balancer configuration for high availability
- DDoS protection and rate limiting
- Controls scaling and lifecycle through GitHub Actions API
- Optimizes communication between workflows and runners
Security Best Practices Assessment
- Vulnerability scanning for runner container images
- Runtime security monitoring and threat detection
- Compliance framework alignment (SOC 2, ISO 27001, etc.)
- Data encryption in transit and at rest
- Audit logging and monitoring requirements
- Incident response procedures for compromised runners
Enterprise Deployment Architecture
Production-Grade Infrastructure Pattern
Multi-Environment Strategy
Development Environment
- Shared runner pools for cost optimization
- Relaxed security policies for developer productivity
- Integration with development tools and debugging capabilities
- Fast feedback loops with minimal resource constraints
Staging Environment
- Production-like configurations for testing
- Security policy enforcement testing
- Performance benchmarking and load testing
- Integration testing with enterprise services
Production Environment
- Dedicated runner pools for critical workloads
- Maximum security and compliance enforcement
- High availability and disaster recovery capabilities
- Comprehensive monitoring and alerting
Self-Hosted vs. GitHub-Hosted Runners Comparison
Enterprise Self-Hosted Runners
Advantages:
- Custom Hardware Specifications: GPU instances, high-memory nodes, specialized processors
- Network Access: Direct access to internal APIs, databases, and enterprise services
- Cost Optimization: No per-minute billing, predictable infrastructure costs
- Performance: Optimized environments, persistent caching, faster build times
- Security Control: Custom security tools, compliance frameworks, network isolation
- Scalability: Unlimited parallel jobs, auto-scaling based on demand
Considerations:
- Infrastructure Management: Kubernetes cluster maintenance and updates
- Security Responsibility: Container image security, vulnerability management
- Operational Overhead: Monitoring, troubleshooting, and incident response
- Compliance: Meeting enterprise security and audit requirements
GitHub-Hosted Runners
Advantages:
- Zero Maintenance: Fully managed by GitHub
- Automatic Updates: Latest software and security patches
- Clean Environment: Fresh instances for each job execution
- Simple Setup: No infrastructure provisioning required
Limitations:
- Resource Constraints: 2-core CPU, 7GB RAM maximum
- Execution Time Limits: 6 hours for public, 35 minutes for private (free)
- Network Isolation: No access to internal enterprise resources
- Cost at Scale: Per-minute billing becomes expensive for high-volume usage
- Limited Customization: Cannot install enterprise-specific tools
Enterprise Authentication and Security
GitHub App Authentication (Recommended for Enterprise)
GitHub Apps provide the most secure and scalable authentication method for enterprise environments, offering fine-grained permissions and enhanced security features.
Enterprise GitHub App Configuration
1. GitHub App Creation and Permissions
# Navigate to GitHub Organization Settings
# https://github.com/organizations/{YOUR_ORG}/settings/apps
# Required App Permissions:
# Repository permissions:
# - Actions: Read
# - Administration: Read
# - Metadata: Read
# - Pull requests: Read (for PR workflows)
# - Checks: Write (for status updates)
#
# Organization permissions:
# - Self-hosted runners: Write
# - Administration: Read (for organization-level deployment)
2. Enterprise Security Configuration
# github-app-secret.yaml
apiVersion: v1
kind: Secret
metadata:
name: github-app-auth
namespace: arc-systems
type: Opaque
data:
github_app_id: <base64-encoded-app-id>
github_app_installation_id: <base64-encoded-installation-id>
github_app_private_key: <base64-encoded-private-key>
---
# Enterprise RBAC Configuration
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: arc-enterprise-role
rules:
- apiGroups: [""]
resources: ["pods", "secrets", "configmaps", "services"]
verbs: ["get", "list", "watch", "create", "update", "patch", "delete"]
- apiGroups: ["apps"]
resources: ["deployments", "replicasets"]
verbs: ["get", "list", "watch", "create", "update", "patch", "delete"]
- apiGroups: ["actions.summerwind.dev"]
resources: ["*"]
verbs: ["*"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: arc-enterprise-binding
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: arc-enterprise-role
subjects:
- kind: ServiceAccount
name: arc-controller
namespace: arc-systems
3. Network Security and Policies
# network-policy-enterprise.yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: arc-enterprise-network-policy
namespace: arc-systems
spec:
podSelector:
matchLabels:
app: actions-runner
policyTypes:
- Ingress
- Egress
ingress:
- from:
- namespaceSelector:
matchLabels:
name: arc-systems
ports:
- protocol: TCP
port: 8080
egress:
# Allow DNS resolution
- to: []
ports:
- protocol: UDP
port: 53
# Allow HTTPS to GitHub
- to: []
ports:
- protocol: TCP
port: 443
# Allow access to internal enterprise services
- to:
- namespaceSelector:
matchLabels:
name: enterprise-services
ports:
- protocol: TCP
port: 443
- protocol: TCP
port: 80
Personal Access Token (PAT) Authentication
For development and testing environments, PAT authentication provides a simpler setup process.
Enterprise PAT Security Requirements
- Fine-grained personal access tokens (beta) recommended
- Organization-specific token scopes
- Regular token rotation (90-day maximum)
- Secure storage in enterprise secret management system
# Required PAT Scopes for Enterprise:
# - repo (Full control of private repositories)
# - admin:org (Full control of orgs and teams, read and write org projects)
# - workflow (Update GitHub Action workflows)
# Create PAT secret
kubectl create secret generic github-pat-secret --from-literal=github_token=$GITHUB_PAT --namespace=arc-systems
# Verify secret creation
kubectl get secret github-pat-secret -n arc-systems -o yaml
Enterprise Authentication Best Practices
1. Credential Management
- Use enterprise secret management solutions (HashiCorp Vault, AWS Secrets Manager)
- Implement automatic credential rotation
- Audit credential access and usage
- Never store credentials in code or configuration files
2. Access Control
- Implement least-privilege access principles
- Use separate authentication for different environments
- Regular access reviews and permission audits
- Multi-factor authentication enforcement
3. Monitoring and Compliance
- Comprehensive audit logging for all authentication events
- Integration with SIEM systems for security monitoring
- Compliance reporting for regulatory requirements
- Incident response procedures for compromised credentials
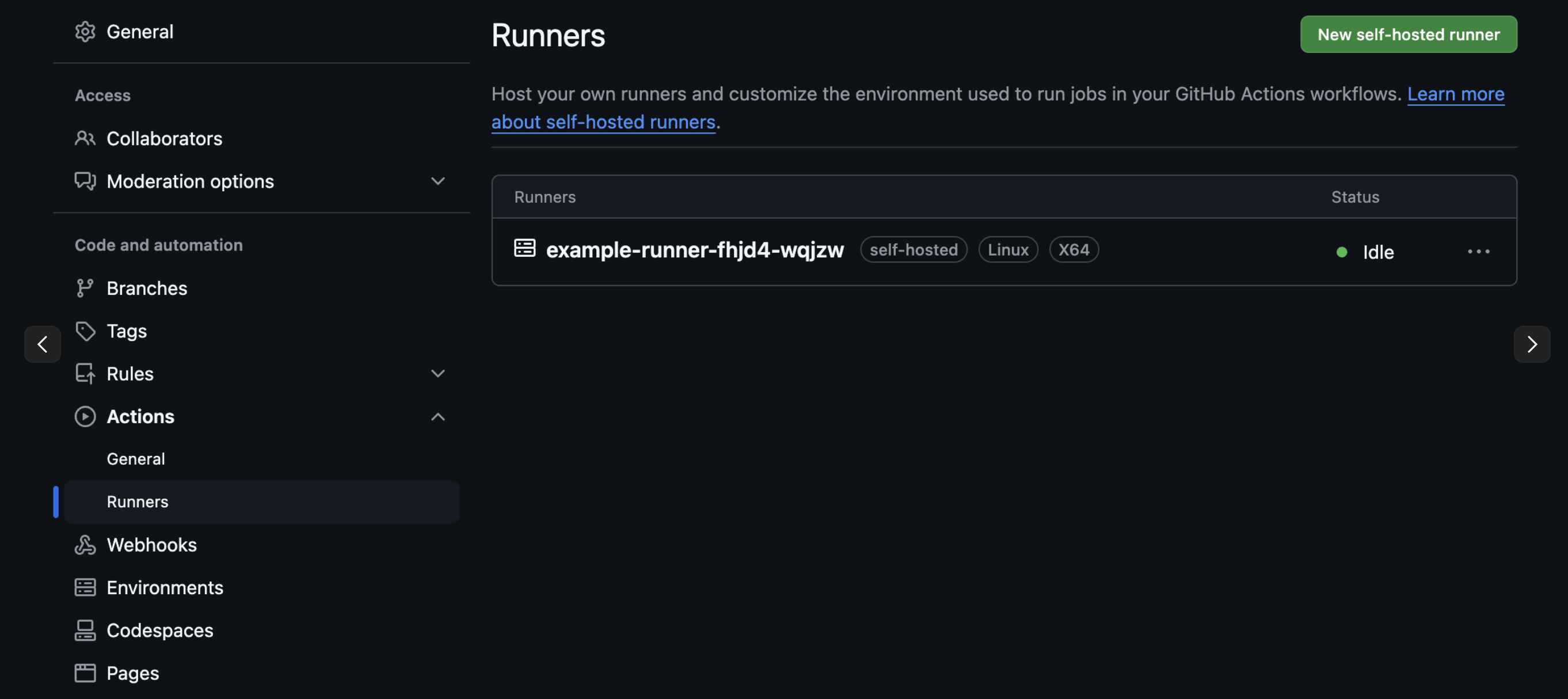
Option 1: GitHub PAT Token
Github Organization/Account settings → Settings → Developer settings → GitHub Personal access tokens
- PAT Token is required for the runner to authenticate with GitHub.
- Below is an example of PAT Token permissions.
- Repository Level: repo, workflow
- Organization Level: read:org, admin:org, workflow
- Enterprise Level: admin:enterprise, workflow
Option 2: GitHub App
If you have an existing app
- Click the app
- Check “App ID” in “About” section
If you don’t have an existing app
- Create new GitHub App
- Input the required Information
- GitHub App name
- Homepage URL
- Webhook URL (Optional)
- Repository permissions Settings:
- Actions: Read and Write
- Administration: Read and Write
- Metadata: Read-only
- Click”Create GitHub App”
Get Installation ID
- Click “Install App”
- Select the repository or organization
- Click “Install”
- Check “Installation ID” in “About” section
https://github.com/organizations/YOUR-ORG/settings/installations/INSTALLATION_ID
Generate private key
- Move App Settings Page
- Click “Generate a private key”
- Download the private key file
- Actions: Read and Write
- Administration: Read and Write
- Metadata: Read-only
Installation
1. Add Helm Repository
helm repo add actions-runner-controller https://actions-runner-controller.github.io/actions-runner-controller
2. Create Namespace
kubectl create namespace actions-runner-system
3. Install Controller
4. Deploy Runner
kubectl apply -f runner-cr.yaml
Configuration Files
runner.yaml
authSecret:
enabled: true
create: true
name: "controller-manager"
github_token: "ghp_xxxxxxxxxxxxxxxxxxxxxxxx"
image:
repository: "summerwind/actions-runner-controller"
actionsRunnerRepositoryAndTag: "summerwind/actions-runner:latest"
dindSidecarRepositoryAndTag: "docker:dind"
pullPolicy: IfNotPresent
rbac:
allowGrantingKubernetesContainerModePermissions: true
serviceAccount:
create: true
runner-cr.yaml
apiVersion: actions.summerwind.dev/v1alpha1
kind: RunnerDeployment
metadata:
name: example-runner
spec:
replicas: 1
template:
spec:
repository: "your-github-username/your-repository"
labels:
- self-hosted
- linux
- x64
Advanced Runner Configurations
1. Auto-Scaling Runners
Create a Horizontal Pod Autoscaler (HPA) for runners:
apiVersion: actions.summerwind.dev/v1alpha1
kind: HorizontalRunnerAutoscaler
metadata:
name: runner-autoscaler
spec:
scaleTargetRef:
name: example-runner
minReplicas: 1
maxReplicas: 10
metrics:
- type: TotalNumberOfQueuedAndInProgressWorkflowRuns
repositoryNames:
- your-github-username/your-repository
2. Organization-Level Runners
apiVersion: actions.summerwind.dev/v1alpha1
kind: RunnerDeployment
metadata:
name: org-runner
spec:
replicas: 2
template:
spec:
organization: "your-organization"
labels:
- org-runner
- linux
- x64
3. Runner with Docker-in-Docker (DinD) Support
apiVersion: actions.summerwind.dev/v1alpha1
kind: RunnerDeployment
metadata:
name: docker-runner
spec:
replicas: 1
template:
spec:
repository: "your-github-username/your-repository"
image: summerwind/actions-runner:latest
dockerEnabled: true
labels:
- docker
- linux
4. Ephemeral Runners (Run once and terminate)
apiVersion: actions.summerwind.dev/v1alpha1
kind: RunnerDeployment
metadata:
name: ephemeral-runner
spec:
replicas: 1
template:
spec:
repository: "your-github-username/your-repository"
ephemeral: true
labels:
- ephemeral
- linux
5. GitHub App Authentication Configuration
# GitHub App Secret
apiVersion: v1
kind: Secret
metadata:
name: github-app-secret
namespace: actions-runner-system
type: Opaque
data:
app-id: "APP_ID_BASE64"
installation-id: "INSTALLATION_ID_BASE64"
private-key: "PRIVATE_KEY_BASE64"
# Controller configuration
authSecret:
enabled: true
create: false
name: "github-app-secret"
Resource Management and Optimization
1. Runner Resource Configuration
apiVersion: actions.summerwind.dev/v1alpha1
kind: RunnerDeployment
metadata:
name: resource-optimized-runner
spec:
replicas: 1
template:
spec:
repository: "your-github-username/your-repository"
resources:
limits:
cpu: "2.0"
memory: "4Gi"
requests:
cpu: "1.0"
memory: "2Gi"
labels:
- resource-optimized
2. Runner with Node Selectors and Tolerations
apiVersion: actions.summerwind.dev/v1alpha1
kind: RunnerDeployment
metadata:
name: dedicated-node-runner
spec:
replicas: 1
template:
spec:
repository: "your-github-username/your-repository"
nodeSelector:
node-type: actions-runner
tolerations:
- key: "dedicated"
operator: "Equal"
value: "actions-runner"
effect: "NoSchedule"
labels:
- dedicated-node
Verification
Check Installation
kubectl get po -n actions-runner-system
kubectl get runnerdeployments.actions.summerwind.dev
Verify Runner Connection
Check runners in your repository:
Settings → Actions → Runners

Example Workflow
name: Example Workflow
on:
workflow_dispatch:
jobs:
test-job:
runs-on: self-hosted
# or runs-on: [self-hosted, linux, x64]
steps:
- name: Test Step
run: echo "Running on self-hosted runner"
Advanced Workflow Examples
Using Docker in Self-Hosted Runner
Workflow with Multiple Runner Types
name: Multi-Runner Workflow
on:
pull_request:
branches: [main]
jobs:
build:
runs-on: [self-hosted, linux, build]
steps:
- uses: actions/checkout@v3
- name: Build App
run: npm ci && npm run build
- name: Upload Artifact
uses: actions/upload-artifact@v3
with:
name: build
path: build/
test:
needs: build
runs-on: [self-hosted, linux, test]
steps:
- uses: actions/checkout@v3
- name: Download Artifact
uses: actions/download-artifact@v3
with:
name: build
path: build/
- name: Run Tests
run: npm ci && npm test
Troubleshooting
Common Issues and Solutions:
1. Runner Registration Failures:
- Check PAT token or GitHub App authentication
- Verify network connectivity to GitHub
- Ensure proper permissions for tokens
- Check logs: kubectl logs -n actions-runner-system deployment/actions-runner-controller-controller-manager
2. Runner Pod Crashes:
- Check resource limits
- Verify container image compatibility
- Inspect pod logs: kubectl logs -n actions-runner-system pod/runner-pod-name
- Check pod events: kubectl describe pod -n actions-runner-system runner-pod-name
3. Runners Not Picking Up Jobs:
- Verify runner labels match workflow configuration
- Check if runners are idle or busy
- Ensure proper repository/organization configuration
- Check runner status in GitHub UI
4. Docker-in-Docker Issues:
- Verify dockerEnabled: true is set
- Check if runner has proper privileges
- Inspect DinD sidecar logs
- Consider volume configuration for Docker socket
Useful Debugging Commands
# Check controller status
kubectl logs -n actions-runner-system deployment/actions-runner-controller-controller-manager
# View runner deployment status
kubectl describe runnerdeployments.actions.summerwind.dev example-runner
# Check runner pod logs
kubectl logs -n actions-runner-system pod/example-runner-pod-name
# Verify runner set status
kubectl get runnersets.actions.summerwind.dev -n actions-runner-system
# Check runner autoscaler status
kubectl describe horizontalrunnerautoscaler.actions.summerwind.dev runner-autoscaler
Security Best Practices
Security Recommendations:
1. Runner Isolation:
- Use ephemeral runners for untrusted code
- Isolate runners in dedicated namespaces
- Consider using runner groups for sensitive projects
- Implement network policies to restrict communication
2. Authentication:
- Use GitHub Apps instead of PAT tokens
- Rotate private keys regularly
- Store secrets securely using Kubernetes Secrets
- Implement least privilege principle for tokens
3. Runner Protection:
- Don’t grant sudo/admin privileges unless necessary
- Limit runner capabilities
- Consider using gVisor or similar sandbox technologies
- Scan runner images for vulnerabilities
4. Docker Security:
- Use rootless Docker when possible
- Implement proper resource limits
- Consider alternatives like Kaniko for building without Docker daemon
- Scan container images during build
Sample Secure Runner Configuration
apiVersion: actions.summerwind.dev/v1alpha1
kind: RunnerDeployment
metadata:
name: secure-runner
spec:
replicas: 1
template:
spec:
repository: "your-github-username/your-repository"
ephemeral: true
securityContext:
runAsNonRoot: true
runAsUser: 1000
fsGroup: 1000
volumeMounts:
- name: tmp
mountPath: /tmp
volumes:
- name: tmp
emptyDir: {}
labels:
- secure-runner
Upgrade and Maintenance
Upgrading Actions Runner Controller
Scaling for Production Workloads
For production environments, consider the following scaling configurations:
apiVersion: actions.summerwind.dev/v1alpha1
kind: HorizontalRunnerAutoscaler
metadata:
name: production-runner-autoscaler
spec:
scaleTargetRef:
name: production-runner
minReplicas: 2
maxReplicas: 20
scaleDownDelaySecondsAfterScaleOut: 300
metrics:
- type: PercentageRunnersBusy
scaleUpThreshold: '0.75'
scaleDownThreshold: '0.25'
scaleUpFactor: '2'
scaleDownFactor: '0.5'
Key Considerations
- You must choose between GitHub App or PAT authentication
- GitHub App is recommended (better security and permissions management)
2. Permissions:
- Set the proper permissions and resources required for Runner
3. Network Policy:
- Check network policy and security settings

Comments