8 min to read
Setting up ArgoCD - GitOps Continuous Deployment Tool

Overview
Learn about ArgoCD, a declarative GitOps continuous deployment tool for Kubernetes.
What is ArgoCD?
ArgoCD is a declarative GitOps CD tool for Kubernetes that:
- Ensures application configurations are version controlled
- Automates deployment lifecycle
- Makes application management auditable and understandable
Why ArgoCD?
- Application definitions, configurations, and environments must be declarative and version controlled.
- Application deployment and lifecycle management should be automated, auditable, and easy to understand.
What is GitOps?
GitOps is a term first used by Weaveworks Inc. in 2017 and is one of DevOps’ practices in projects.
It focuses on continuous deployment targeting cloud-native applications.
As the word indicates, it means that all elements related to the distribution and operation of the application are coded and managed in Git.
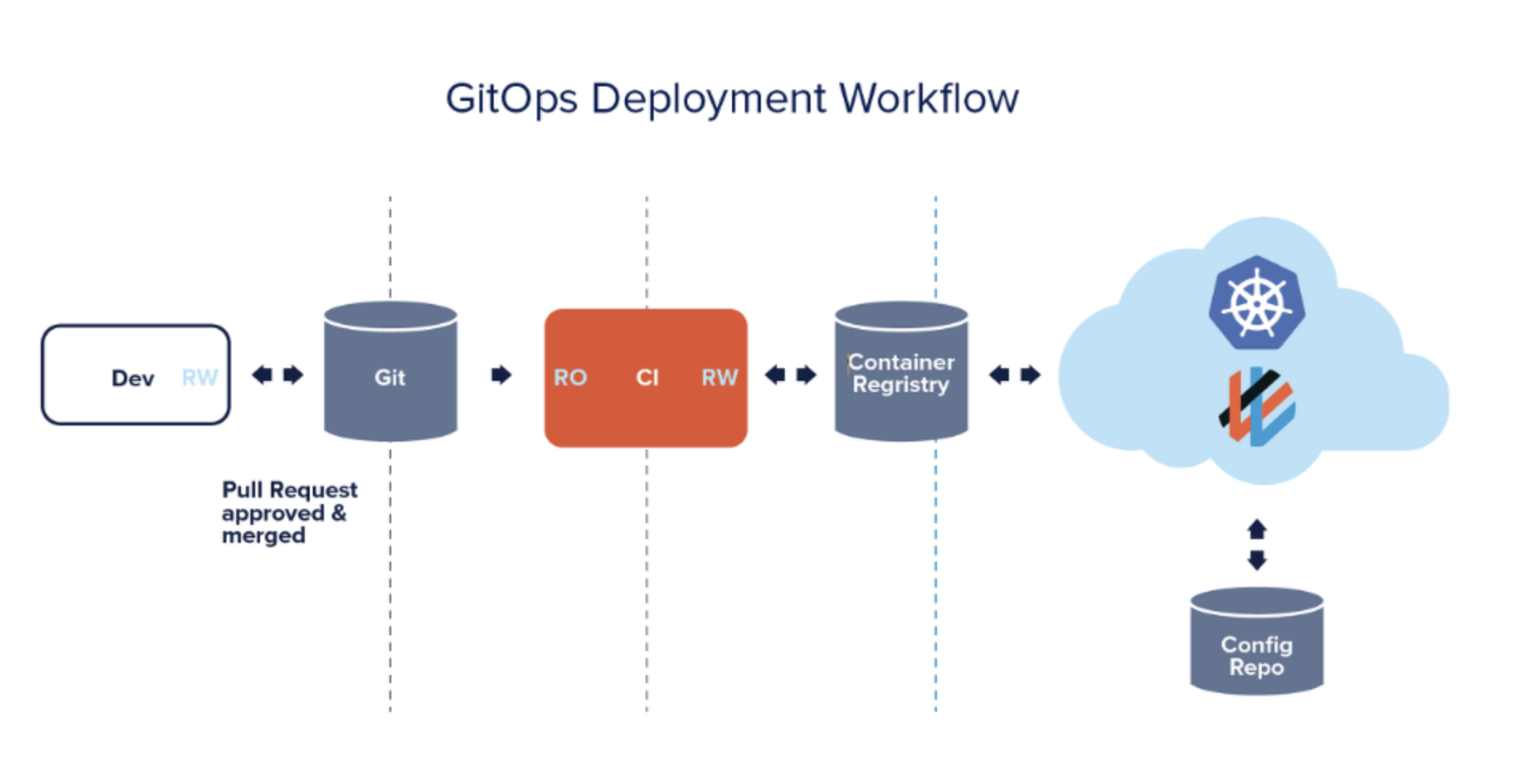
ArgoCD Components Architecture
Installation
# Install ArgoCD
kubectl create namespace argocd
kubectl apply -n argocd -f https://raw.githubusercontent.com/argoproj/argo-cd/stable/manifests/install.yaml
kubectl apply -n argocd -f https://raw.githubusercontent.com/argoproj/argo-cd/stable/manifests/ha/install.yaml
# Install Argocd Helm Chart https://argo-cd.readthedocs.io/en/latest/user-guide/helm/
# Reference: https://github.com/somaz94/helm-chart-template/tree/main/k8s-service/argocd/argo-cd
helm install argocd argo-cd --namespace argocd --create-namespace --version <version>
# Install ArgoCD CLI
curl -sL -o argocd https://github.com/argoproj/argo-cd/releases/download/v2.7.1/argocd-linux-amd64
chmod +x argocd
sudo mv argocd /usr/local/bin/
Helm Values Example
# values.yaml for Helm installation
server:
extraArgs:
- --insecure
ingress:
enabled: true
hosts:
- argocd.example.com
annotations:
kubernetes.io/ingress.class: nginx
nginx.ingress.kubernetes.io/force-ssl-redirect: "true"
nginx.ingress.kubernetes.io/ssl-passthrough: "true"
nginx.ingress.kubernetes.io/backend-protocol: "HTTPS"
resources:
limits:
cpu: 500m
memory: 512Mi
requests:
cpu: 200m
memory: 256Mi
repoServer:
resources:
limits:
cpu: 300m
memory: 512Mi
requests:
cpu: 100m
memory: 256Mi
applicationSet:
enabled: true
notifications:
enabled: true
dex:
enabled: false
To install with custom values:
helm install argocd argo-cd -f values.yaml --namespace argocd --create-namespace
Ingress Configuration
Initial Setup
# Get initial admin password
kubectl -n argocd get secret argocd-initial-admin-secret -o jsonpath="{.data.password}" | base64 -d; echo
# Verify installation
kubectl get po,svc,ingress,sts -n argocd
Login
Managing Applications
Application Definition
Create an application in ArgoCD:
# application.yaml
apiVersion: argoproj.io/v1alpha1
kind: Application
metadata:
name: guestbook
namespace: argocd
spec:
project: default
source:
repoURL: https://github.com/argoproj/argocd-example-apps.git
targetRevision: HEAD
path: guestbook
destination:
server: https://kubernetes.default.svc
namespace: guestbook
syncPolicy:
automated:
prune: true
selfHeal: true
syncOptions:
- CreateNamespace=true
Apply the application:
kubectl apply -f application.yaml
CLI Management
# Log in to ArgoCD
argocd login argocd.somaz.link
# List applications
argocd app list
# Get application details
argocd app get guestbook
# Manually sync an application
argocd app sync guestbook
# Create an application via CLI
argocd app create guestbook --repo https://github.com/argoproj/argocd-example-apps.git --path guestbook --dest-server https://kubernetes.default.svc --dest-namespace guestbook
Advanced Configuration
SSO Integration
You can integrate ArgoCD with Identity Providers using OIDC:
apiVersion: v1
kind: ConfigMap
metadata:
name: argocd-cm
namespace: argocd
data:
url: https://argocd.somaz.link
# OIDC Configuration
oidc.config: |
name: Okta
issuer: https://dev-123456.okta.com
clientID: 0oabcdefghijklmn
clientSecret: '$oidc.okta.clientSecret'
requestedScopes: ["openid", "profile", "email", "groups"]
requestedIDTokenClaims:
groups:
essential: true
Create a secret for the client secret:
kubectl create secret generic argocd-secret --from-literal=oidc.okta.clientSecret=your-client-secret -n argocd
RBAC Configuration
Configure RBAC in ArgoCD:
apiVersion: v1
kind: ConfigMap
metadata:
name: argocd-rbac-cm
namespace: argocd
data:
policy.csv: |
# Project roles
p, role:dev-readonly, applications, get, dev/*, allow
p, role:dev-admin, applications, *, dev/*, allow
# Group mappings
g, dev-team, role:dev-readonly
g, devops-team, role:dev-admin
# Allow admins to do everything
p, role:org-admin, applications, *, */*, allow
g, admin-team, role:org-admin
ApplicationSet Example
ApplicationSets help manage multiple similar applications:
apiVersion: argoproj.io/v1alpha1
kind: ApplicationSet
metadata:
name: microservices
namespace: argocd
spec:
generators:
- list:
elements:
- name: api
namespace: microservices
path: services/api
- name: auth
namespace: microservices
path: services/auth
- name: frontend
namespace: microservices
path: services/frontend
template:
metadata:
name: ''
spec:
project: default
source:
repoURL: https://github.com/myorg/microservices.git
targetRevision: HEAD
path: ''
destination:
server: https://kubernetes.default.svc
namespace: ''
syncPolicy:
automated:
prune: true
selfHeal: true
Monitoring and Troubleshooting
Health Status Dashboard
ArgoCD provides a dashboard to monitor the health of your applications. If you encounter issues, check these common problems:
Common Issues and Solutions:
1. Application Out of Sync: - Check Git repository connectivity
- Verify branch/tag/commit reference
- Inspect detailed sync status:
argocd app get [app-name]2. Authentication Failures: - Ensure Git credentials are correct
- Check SSH keys or access tokens
- Verify network connectivity to Git provider
3. Resource Creation Failures: - Check RBAC permissions
- Verify namespace exists (or enable auto-creation)
- Look for validation errors:
kubectl logs deployment/argocd-repo-server -n argocd4. Webhook Integration Issues: - Ensure webhook is properly configured
- Check network connectivity from Git provider to ArgoCD
- Verify payload structure and secrets
Useful Diagnostic Commands
# Check ArgoCD server logs
kubectl logs -n argocd -l app.kubernetes.io/name=argocd-server
# Check repo server logs (for Git issues)
kubectl logs -n argocd -l app.kubernetes.io/name=argocd-repo-server
# Check controller logs (for sync issues)
kubectl logs -n argocd -l app.kubernetes.io/name=argocd-application-controller
# Get detailed application status
argocd app get myapp --hard-refresh
# Check recent application events
kubectl get events -n argocd --sort-by='.lastTimestamp'
Backup and Restore
Backup ArgoCD
# Backup ArgoCD application definitions
kubectl get applications -n argocd -o yaml > argocd-applications-backup.yaml
# Backup ArgoCD projects
kubectl get appprojects -n argocd -o yaml > argocd-projects-backup.yaml
# Backup ArgoCD settings and configurations
kubectl get configmap argocd-cm -n argocd -o yaml > argocd-cm-backup.yaml
kubectl get configmap argocd-rbac-cm -n argocd -o yaml > argocd-rbac-cm-backup.yaml
kubectl get secret argocd-secret -n argocd -o yaml > argocd-secret-backup.yaml
Restore ArgoCD
# Restore from backups
kubectl apply -f argocd-applications-backup.yaml
kubectl apply -f argocd-projects-backup.yaml
kubectl apply -f argocd-cm-backup.yaml
kubectl apply -f argocd-rbac-cm-backup.yaml
kubectl apply -f argocd-secret-backup.yaml
Best Practices
1. Security: - Change default admin password
- Use SSL/TLS
- Implement RBAC
- Regularly rotate secrets and credentials
- Use private Git repositories
2. High Availability: - Use HA installation for production
- Configure proper backup
- Monitor resources
- Set appropriate resource limits
- Use node affinity for critical components
3. GitOps Workflow: - Use declarative configurations
- Version control everything
- Automate deployments
- Implement PR approval workflows
- Organize repositories by environment
4. Performance: - Use ApplicationSets for managing multiple applications
- Configure reasonable sync periods
- Utilize webhooks for immediate updates
- Implement proper caching strategies
- Monitor and adjust resource limits as needed

Comments