6 min to read
Understanding Amazon EKS Pod Identity Addon
A deep dive into EKS Pod Identity and comparison with IRSA
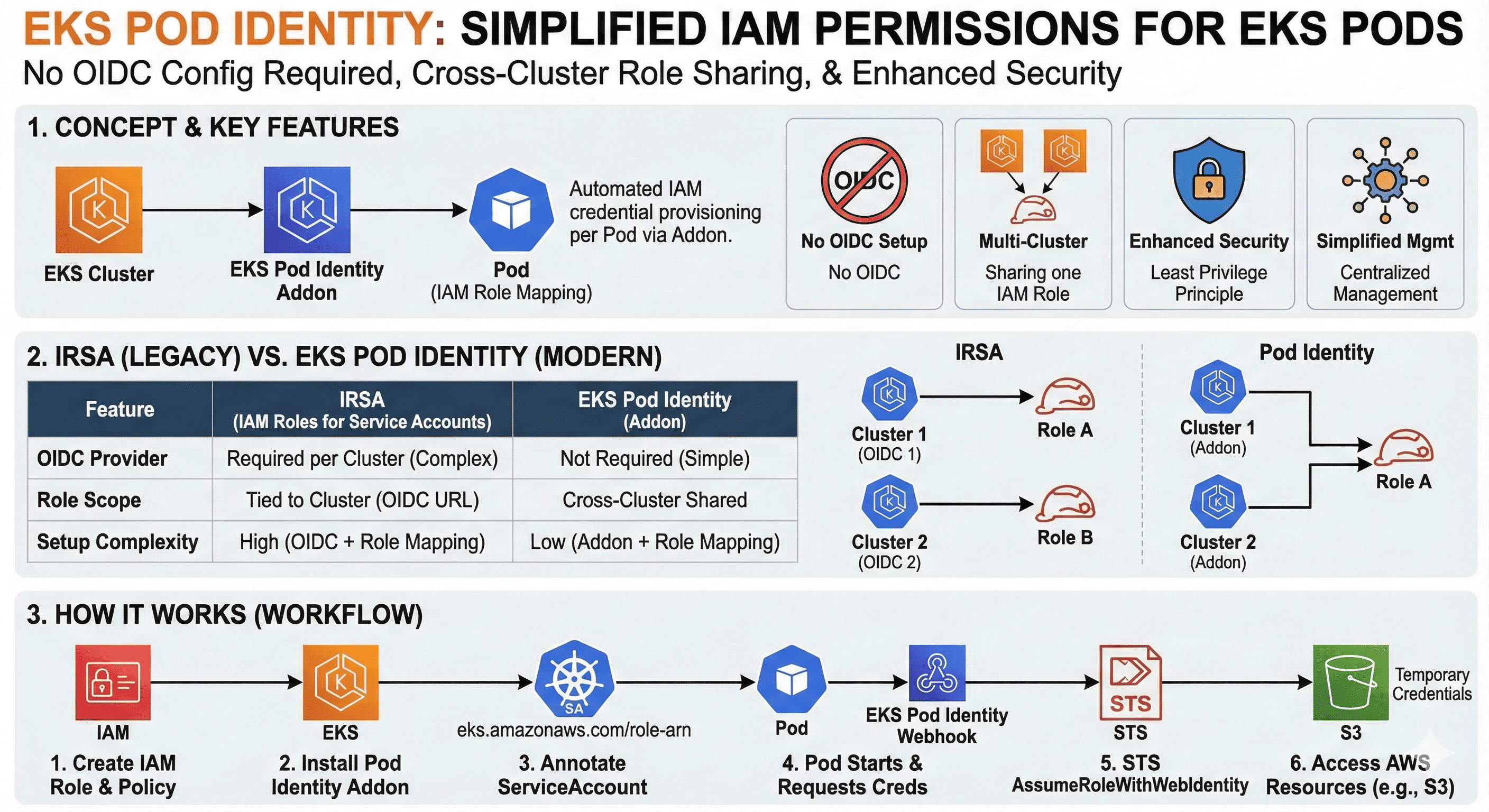
Overview
This post explores EKS Pod Identity Addon, a new feature released by AWS in December 2023 for managing IAM credentials in EKS clusters.
- Manages credentials for applications similar to EC2 instance profiles
- Provides secure credentials through EKS Auth API and agent pods
- Integrates with Kubernetes API server via Pod Identity Webhook
- Simplifies AWS permissions management for Kubernetes identities
How It Works
Service Account and IAM Role Connection
- Links Kubernetes service accounts with IAM roles
- Defines AWS resource permissions in IAM roles
- Pod Identity Webhook issues web ID tokens
- Uses STS AssumeRoleWithWebIdentity for temporary credentials
Advantages
- Implements least privilege principle with per-pod IAM roles
- Reduces credential exposure risk
- Simplifies credential management with AWS SDK
- Enables fine-grained access control
Implementation Guide
1. EKS Cluster Setup
- Enable PodIdentity Webhook when creating an EKS cluster
- To use IRSA, connect the OIDC provider to a cluster
2. Create OIDC provider
3. Service Account Configuration
apiVersion: v1
kind: ServiceAccount
metadata:
name: my-service-account
annotations:
eks.amazonaws.com/role-arn: arn:aws:iam::<account-id>:role/<role-name>
4. Pod Configuration
apiVersion: apps/v1
kind: Deployment
metadata:
name: my-deployment
spec:
template:
spec:
serviceAccountName: my-service-account
5. Add IAM Role
- Associate IAM policies for AWS resource access to roles
IRSA vs Pod Identity Comparison
- OIDC Provider:
- IRSA: Required for each cluster
- Pod Identity: Not required
- Role Management:
- IRSA: Cluster-specific roles
- Pod Identity: Shared roles across clusters
- Setup Complexity:
- IRSA: Moderate (OIDC setup per cluster)
- Pod Identity: Simpler (Centralized management)
IRSA
- In IRSA, each EKS cluster must create an OpenID Connect (OIDC) ID provider and associate with the cluster.
- The IAM role is associated with a specific service account in the cluster-specific Kubernetes Namespace.
- Roles are associated with OIDC issuer URLs that are unique to each cluster, so you must create a separate IAM role for each cluster or service account.
- For example, an ARN in an IAM role contains an OIDC provider URL associated with the cluster.
eks.amazonaws.com/role-arn: arn:aws:iam::(account-id):role/(role-name)- Each IAM role is scoped as the OIDC provider in the cluster, making it difficult to share roles across clusters
- If you have multiple clusters, you must create a separate IAM role for each cluster and associate it with the service account for that cluster.
Pod Identity
- Sharing Roles Across Clusters
- Pod ID abstracts the need for cluster-specific OIDC providers
- A single IAM role that can be shared across multiple EKS clusters is available.
- With Pod ID, roles are not linked to a particular OIDC provider or cluster.
- ID mapping is handled centrally, and Kubernetes service accounts across the cluster can use the same IAM role.
- The Pod ID agent add-on serves as a bridge between the Kubernetes Pod and AWS Identification and Access Management (IAM).
- Pod dynamically takes on the role of IAM without an OIDC provider. This allows for smooth expansion and easier management of access policies.
IMDSv2 Integration
Instance Metadata Service Version 2 (IMDSv2) is a secure version of the AWS EC2 instance’s access to metadata.
- Token-based session authentication
- Enhanced security against SSRF attacks
- Network hop limits
- Required header validation
Example IMDSv2 Usage
Migration from IRSA to Pod Identity
- Install the EKS Pod Identity Agent on your existing clusters
- Create Pod Identity Associations between service accounts and IAM roles
- Gradually transition workloads to use Pod Identity instead of IRSA
- Update service account annotations to match the new format
Example Pod Identity Association
apiVersion: eks.amazonaws.com/v1beta1
kind: PodIdentityAssociation
metadata:
name: my-app-association
namespace: default
spec:
serviceAccount: my-service-account
roleArn: arn:aws:iam::<account-id>:role/EKSPodIdentityRole
Compatibility with Existing Workloads
You can run both IRSA and Pod Identity in the same cluster during migration:
Troubleshooting Pod Identity
- Credentials not available: Check Pod Identity Agent logs
- Permission denied: Verify IAM role has appropriate policies
- Association not working: Confirm Pod Identity Association exists
- Agent pods failing: Check for networking or RBAC issues
Debugging Commands
# Check Pod Identity Agent status
kubectl get pods -n kube-system | grep pod-identity-agent
# View Agent logs
kubectl logs -n kube-system pod-identity-agent-xxxxx
# Verify service account configuration
kubectl describe serviceaccount my-service-account -n default
# Test AWS credentials from within a pod
kubectl exec -it my-pod -- aws sts get-caller-identity


Comments