15 min to read
AWS Network Connection Methods Complete Comparison - VPC Peering vs Transit Gateway vs VPN
Comprehensive analysis of AWS networking solutions for multi-VPC and hybrid cloud architectures
Overview
Network connectivity between multiple VPCs is a core component of modern cloud infrastructure design.
AWS provides various networking connection options including VPC Peering, Transit Gateway, and VPN, each with unique characteristics and application scenarios.
This comprehensive guide analyzes the technical features of these three methods, compares them across scalability, cost, and security dimensions, and examines key considerations for designing hybrid cloud architectures.
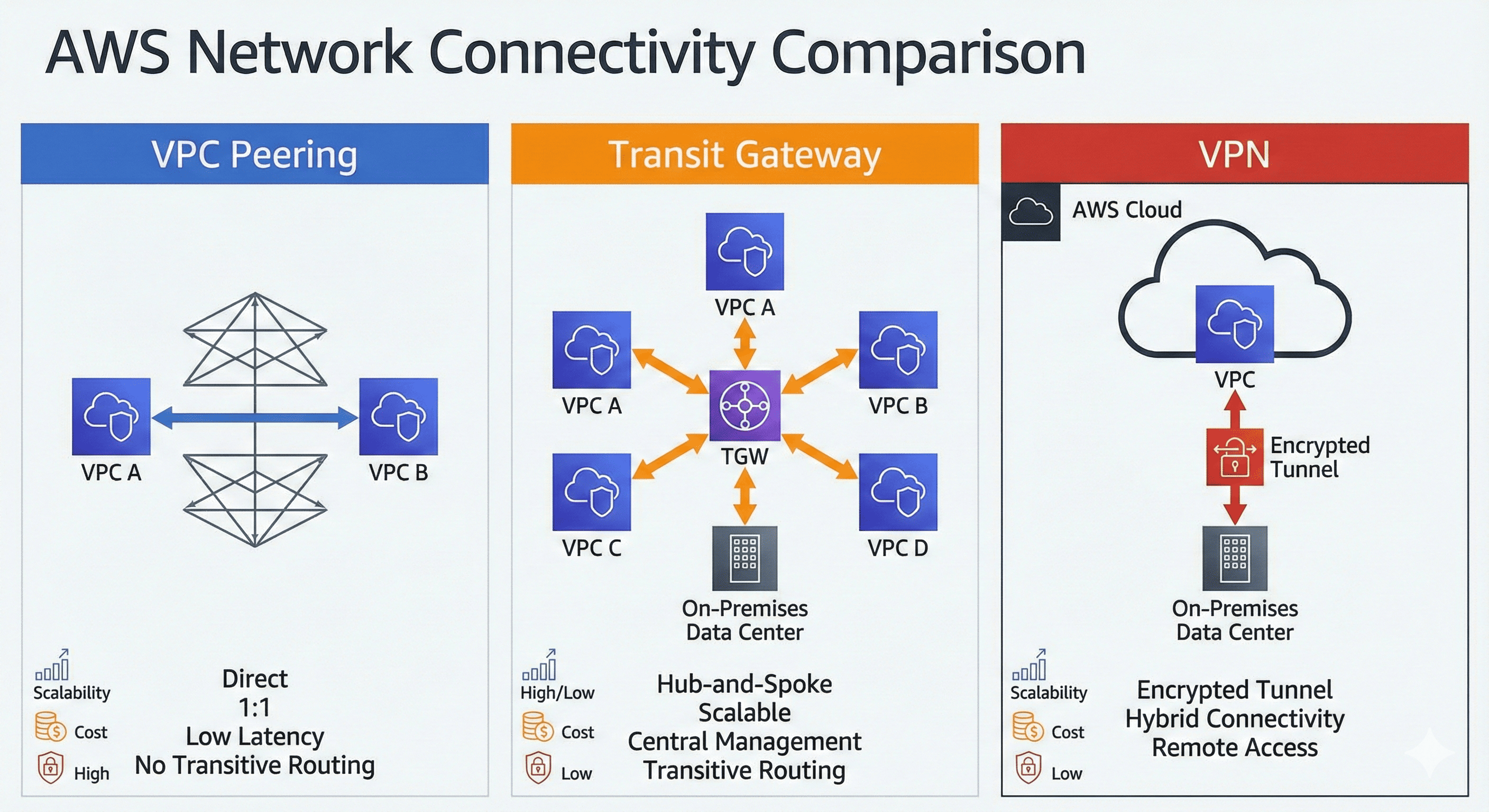
Network Connection Architecture Overview
VPC Peering In-Depth Analysis
VPC Peering provides the simplest form of direct network connection between two VPCs.
It operates through AWS's private backbone network, ensuring secure communication without internet exposure.
Technical Characteristics
VPC Peering creates a 1:1 network connection between VPCs using AWS’s private infrastructure.
This connection operates at the network layer and provides seamless communication as if resources were in the same network.
Key Features
- Direct 1:1 Connection: Point-to-point connectivity between VPCs
- No Transitive Routing: Does not support routing through intermediate VPCs
- Cross-Region Support: Enables inter-region VPC connections
- Unlimited Bandwidth: No artificial bandwidth limitations imposed
Limitations and Considerations
The most significant constraint of VPC Peering is the lack of transitive routing support.
If VPC A peers with VPC B, and VPC B peers with VPC C, VPC A cannot communicate directly with VPC C through VPC B. This limitation dramatically increases management overhead in complex network topologies.
Additionally, overlapping CIDR blocks are not permitted, requiring careful IP address space planning during network design.
Terraform Implementation
# VPC Peering Connection
resource "aws_vpc_peering_connection" "main" {
peer_vpc_id = aws_vpc.peer.id
vpc_id = aws_vpc.main.id
# For cross-region peering
peer_region = var.peer_region
tags = {
Name = "vpc-peering-main-to-peer"
}
}
# Accept Peering Connection
resource "aws_vpc_peering_connection_accepter" "peer" {
vpc_peering_connection_id = aws_vpc_peering_connection.main.id
auto_accept = true
tags = {
Name = "vpc-peering-accepter"
}
}
# Route Table Updates
resource "aws_route" "main_to_peer" {
route_table_id = aws_route_table.main.id
destination_cidr_block = aws_vpc.peer.cidr_block
vpc_peering_connection_id = aws_vpc_peering_connection.main.id
}
resource "aws_route" "peer_to_main" {
route_table_id = aws_route_table.peer.id
destination_cidr_block = aws_vpc.main.cidr_block
vpc_peering_connection_id = aws_vpc_peering_connection.main.id
}
Transit Gateway Comprehensive Analysis
Transit Gateway implements a hub-and-spoke model enabling centralized network management.
This significantly reduces complexity in multi-VPC environments through consolidated routing control.
Architectural Excellence
Transit Gateway serves as a regional network hub that connects VPCs, on-premises networks, and other AWS services through a single managed service.
This hub-and-spoke architecture eliminates the need for complex mesh networking configurations.
Core Capabilities
- Multi-VPC and On-Premises Support: Connects various network types through a single hub
- Granular Traffic Control: Advanced routing tables for fine-grained traffic management
- Cross-Region Peering: Enables global network connectivity
- Direct Connect Integration: Seamless integration with dedicated network connections
Advanced Feature Utilization
Transit Gateway enables network segmentation through routing tables and attachments.
This allows logical separation between development, staging, and production environments while permitting selective communication when required.
Terraform Implementation
# Transit Gateway Creation
resource "aws_ec2_transit_gateway" "main" {
description = "Main Transit Gateway"
default_route_table_association = "enable"
default_route_table_propagation = "enable"
dns_support = "enable"
vpn_ecmp_support = "enable"
tags = {
Name = "main-tgw"
}
}
# VPC Attachments
resource "aws_ec2_transit_gateway_vpc_attachment" "production" {
subnet_ids = [aws_subnet.prod_private.id]
transit_gateway_id = aws_ec2_transit_gateway.main.id
vpc_id = aws_vpc.production.id
tags = {
Name = "tgw-attachment-production"
}
}
resource "aws_ec2_transit_gateway_vpc_attachment" "development" {
subnet_ids = [aws_subnet.dev_private.id]
transit_gateway_id = aws_ec2_transit_gateway.main.id
vpc_id = aws_vpc.development.id
tags = {
Name = "tgw-attachment-development"
}
}
# Custom Routing Table
resource "aws_ec2_transit_gateway_route_table" "isolated" {
transit_gateway_id = aws_ec2_transit_gateway.main.id
tags = {
Name = "isolated-environment-routes"
}
}
# Route Configuration
resource "aws_ec2_transit_gateway_route" "production_route" {
destination_cidr_block = "10.1.0.0/16"
transit_gateway_attachment_id = aws_ec2_transit_gateway_vpc_attachment.production.id
transit_gateway_route_table_id = aws_ec2_transit_gateway_route_table.isolated.id
}
VPN Connection Methods Detailed Analysis
Site-to-Site VPN Technical Architecture
AWS Site-to-Site VPN establishes encrypted connections between on-premises networks and AWS VPCs using IPSec tunnels.
Each VPN connection consists of two tunnels to ensure high availability and redundancy.
Key Components
- Virtual Private Gateway (VGW) or Transit Gateway: AWS-side gateway for VPN termination
- Customer Gateway: On-premises gateway device or software
- VPN Connection: IPSec tunnel configuration between gateways
Client VPN for Remote Access
AWS Client VPN provides OpenVPN-based managed service for secure remote user access to AWS resources.
It supports various authentication methods including Active Directory, SAML 2.0, and certificate-based authentication.
Terraform Implementation
# Customer Gateway
resource "aws_customer_gateway" "main" {
bgp_asn = 65000
ip_address = var.customer_gateway_ip
type = "ipsec.1"
tags = {
Name = "main-customer-gateway"
}
}
# Virtual Private Gateway
resource "aws_vpn_gateway" "main" {
vpc_id = aws_vpc.main.id
tags = {
Name = "main-vpn-gateway"
}
}
# VPN Connection
resource "aws_vpn_connection" "main" {
customer_gateway_id = aws_customer_gateway.main.id
type = "ipsec.1"
vpn_gateway_id = aws_vpn_gateway.main.id
static_routes_only = true
tags = {
Name = "main-vpn-connection"
}
}
# Static Route Configuration
resource "aws_vpn_connection_route" "office" {
vpn_connection_id = aws_vpn_connection.main.id
destination_cidr_block = "192.168.0.0/16"
}
# Transit Gateway VPN Attachment (Advanced)
resource "aws_ec2_transit_gateway_vpn_attachment" "tgw_vpn" {
customer_gateway_id = aws_customer_gateway.main.id
transit_gateway_id = aws_ec2_transit_gateway.main.id
tags = {
Name = "tgw-vpn-attachment"
}
}
Scalability Comparison Analysis
VPC Peering Scalability Constraints
VPC Peering requires n(n-1)/2 peering connections to connect n VPCs in a full mesh topology.
This results in exponential complexity growth as the number of VPCs increases. For example, connecting 10 VPCs requires 45 peering connections, each requiring individual routing configuration.
| Number of VPCs | Required Peering Connections | Route Entries per VPC | Management Complexity |
|---|---|---|---|
| 3 | 3 | 2 | Low |
| 5 | 10 | 4 | Medium |
| 10 | 45 | 9 | High |
| 20 | 190 | 19 | Very High |
Transit Gateway Scaling Excellence
Transit Gateway provides linear scalability through its hub-and-spoke model.
Connecting n VPCs requires only n attachments, with centralized routing management significantly reducing complexity.
Transit Gateway Limitations
| Resource | Limit per Region | Notes |
|---|---|---|
| Attachments per Transit Gateway | 5,000 | Includes VPCs, VPNs, Direct Connect |
| Routes per Route Table | 10,000 | Static and propagated routes |
| Bandwidth per Attachment | 50 Gbps | Burst capacity up to 100 Gbps |
| Transit Gateways per Region | 5 | Can be increased via support request |
VPN Scalability Considerations
VPN connections scale based on on-premises infrastructure expansion requirements.
AWS supports VPN tunnels up to 1.25 Gbps each, with higher bandwidth achievable through multiple tunnels or Direct Connect integration.
Cost Structure Deep Dive
VPC Peering Cost Model
VPC Peering incurs no hourly charges for the peering connection itself, with costs only for data transfer. Same-AZ data transfer is free, while cross-AZ and cross-region transfers incur standard data transfer charges.
| Transfer Type | Cost (USD) | Notes |
|---|---|---|
| Peering Connection | $0.00/hour | No connection charges |
| Same AZ Data Transfer | $0.00/GB | Within same availability zone |
| Cross-AZ Data Transfer | $0.01/GB | Between availability zones |
| Cross-Region Data Transfer | $0.02-0.09/GB | Varies by region pair |
Transit Gateway Cost Model
Transit Gateway charges based on the number of attachments and data processing volume.
| Service Component | Cost (USD) | Billing Unit |
|---|---|---|
| Attachment Hour | $0.05 | Per attachment per hour |
| Data Processing | $0.02 | Per GB processed |
| Cross-Region Peering | $0.05 | Per peering per hour |
VPN Cost Model
VPN connections charge for connection time and data transfer volumes.
| Service Component | Cost (USD) | Billing Unit |
|---|---|---|
| VPN Connection Hour | $0.05 | Per connection per hour |
| Data Transfer Out | $0.09 | Per GB (first 1 GB free) |
| Data Transfer In | $0.00 | Per GB (free) |
Security Assessment Comprehensive Review
VPC Peering Security Characteristics
VPC Peering provides private connectivity through AWS backbone infrastructure, ensuring no internet exposure.
Independent security groups and NACLs in each VPC enable granular access control with defense-in-depth architecture.
Transit Gateway Security Enhancement
Transit Gateway enables network segmentation through routing tables, supporting micro-segmentation for zero-trust architecture implementation.
Advanced routing policies allow precise traffic flow control between network segments.
VPN Encryption and Authentication
Site-to-Site VPN provides end-to-end encryption through IPSec, supporting pre-shared key (PSK) or certificate-based authentication. Client VPN integrates with Active Directory, SAML 2.0, or certificate-based authentication systems.
Hybrid Cloud Architecture Design Strategy
Multi-Tier Network Architecture
Modern hybrid cloud environments combine multiple connection methods to optimize network architecture based on specific requirements.
Recommended Design Patterns
- Core Network: Transit Gateway-centered hub-and-spoke structure
- Edge Connectivity: Direct Connect or VPN for on-premises connectivity
- Workload Isolation: VPC Peering for special-purpose connections
Performance Optimization Considerations
Network performance optimization requires comprehensive consideration of latency, bandwidth, and availability. Transit Gateway provides up to 50 Gbps bandwidth within regions, but cross-region connections may introduce additional latency.
Disaster Recovery and Business Continuity
Network connection redundancy is essential in hybrid cloud architectures. If Transit Gateway serves as the primary connection, consider VPN as backup path, or implement hybrid approaches using both Direct Connect and VPN simultaneously.
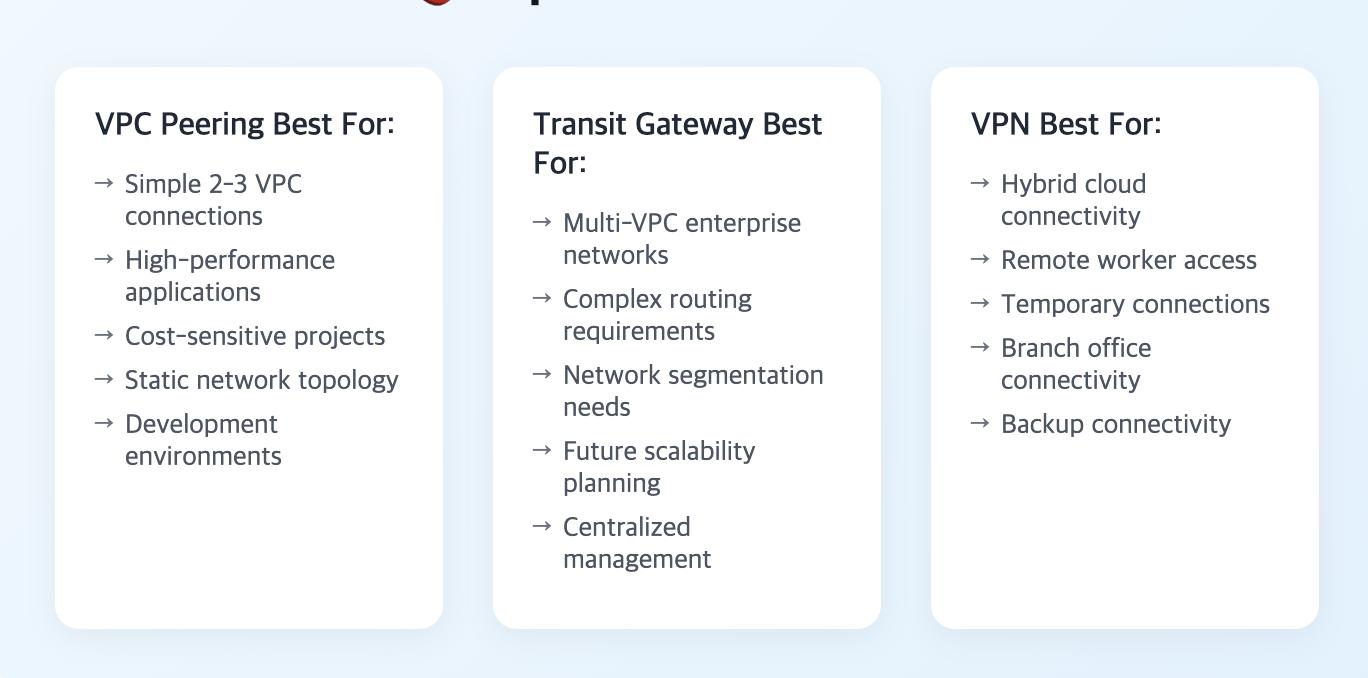
Optimal Use Cases by Connection Method
VPC Peering Optimal Scenarios
- Simple Connectivity: Small number of VPCs requiring straightforward connections
- High Performance Requirements: Applications demanding high bandwidth and low latency
- Cost Optimization Focus: Projects where cost minimization is the primary objective
- Stable Topology: Networks with simple, infrequently changing topologies
Transit Gateway Optimal Scenarios
- Complex Multi-VPC Environments: Large-scale networks requiring numerous VPC connections
- Advanced Routing Requirements: Networks needing sophisticated routing policies
- Security and Segmentation: Environments where network segmentation and security are critical
- Future Scalability: Architectures designed for significant future expansion
VPN Optimal Scenarios
- Hybrid Connectivity: Connecting on-premises infrastructure to cloud environments
- Remote User Access: Providing secure access for distributed workforce
- Temporary Connections: Short-term or testing-purpose network connections
- Pre-Direct Connect: Interim connectivity before Direct Connect deployment
Performance and Monitoring Best Practices
Network Monitoring Strategy
Implement comprehensive monitoring across all connection types using CloudWatch metrics, VPC Flow Logs, and AWS X-Ray for distributed tracing.
Performance Optimization Guidelines
- Right-sizing: Choose appropriate instance types and network configurations
- Regional Placement: Optimize resource placement to minimize latency
- Connection Redundancy: Implement multiple paths for critical connections
- Traffic Engineering: Use routing policies to optimize traffic flow
Conclusion
AWS networking options—VPC Peering, Transit Gateway, and VPN—each offer unique characteristics and advantages.
VPC Peering excels in simple 1:1 connections with superior performance and cost efficiency. Transit Gateway demonstrates excellence in centralized management and scalability for complex multi-VPC environments. VPN serves as a cornerstone for hybrid cloud connectivity, providing essential on-premises integration.
Successful cloud network design requires comprehensive consideration of current requirements alongside future expansion plans, security requirements, and cost optimization goals. Most enterprise environments benefit from hybrid approaches combining multiple connection methods rather than relying on single solutions.
Through appropriate network architecture selection, organizations can simultaneously achieve performance, security, and cost efficiency objectives, ultimately contributing significantly to business goal achievement. The key lies in understanding the strengths and limitations of each approach and selecting the optimal combination for specific use cases.

Comments