39 min to read
Advanced AWS Assume Role Patterns & Enterprise Security Best Practices
Overview
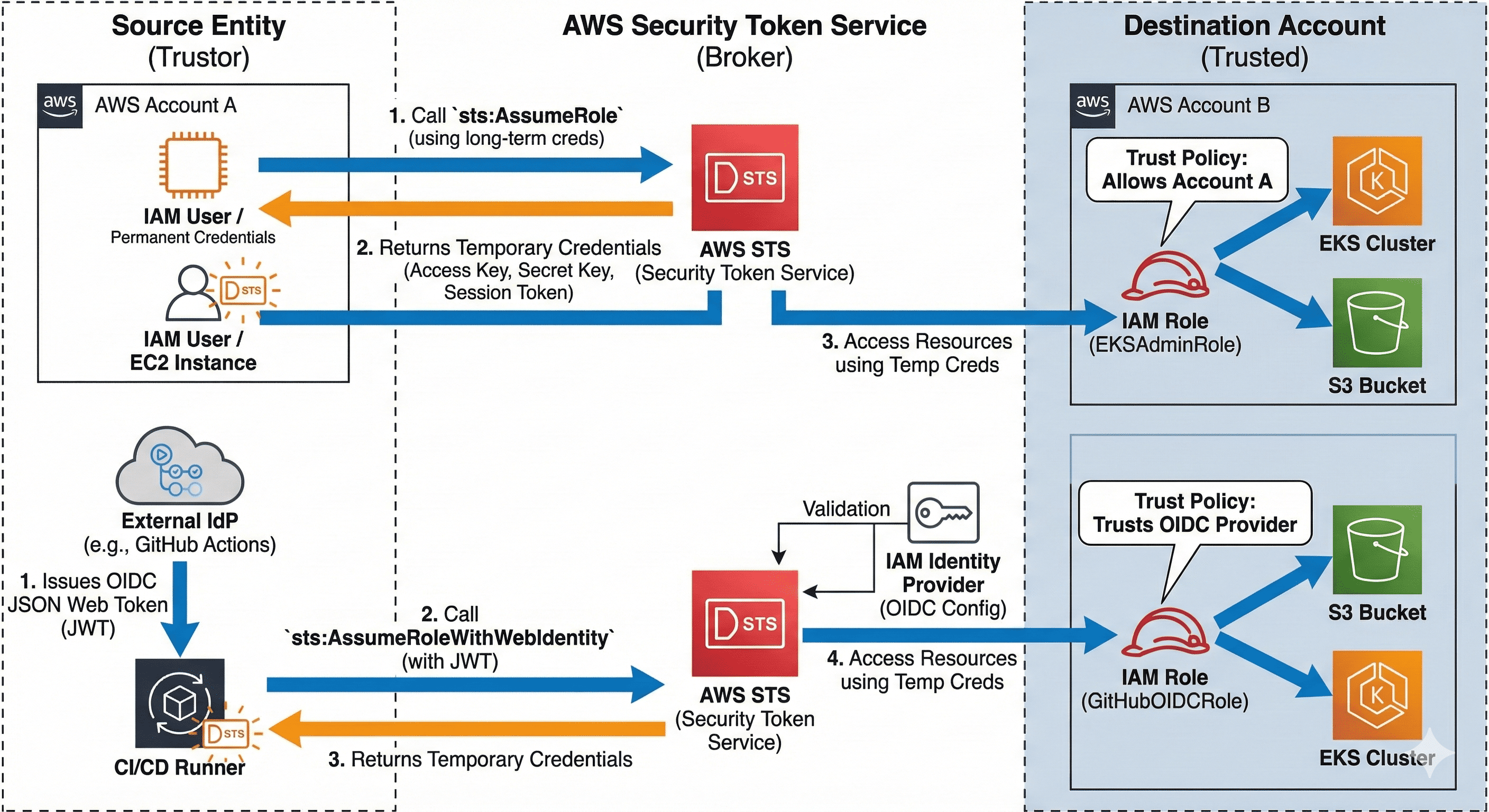
AWS Assume Role is a fundamental security feature that enables temporary, controlled access to AWS resources across accounts or within the same account.
This comprehensive guide covers advanced patterns, automation strategies, and enterprise-grade security implementations for production environments.
What is AWS Assume Role?
AWS Assume Role is a function provided by AWS Security Token Service (STS) that allows one IAM entity (user or service) to temporarily adopt another role in AWS and use the permissions associated with that role.
This mechanism enhances security and simplifies access management by granting only the necessary permissions for the duration required to complete specific tasks.
The sts:AssumeRole operation enables a secure delegation model where:
- Temporary access: Credentials expire after a specified duration (15 minutes to 12 hours)
- No sharing of long-term credentials: Eliminates the need to share permanent IAM credentials
- Granular permissions: Access can be restricted based on session policies, source IP, and more
- Centralized management: Simplifies permission management across multiple accounts
- Audit trail: Complete visibility into who assumed what role and when
- Zero-trust architecture: Supports least-privilege access principles
Advanced Use Cases
- Cross-account access: Access resources in another AWS account without creating and managing users in that account
- Multi-tenant architectures: Isolate customer data while maintaining operational efficiency
- Break-glass procedures: Emergency access with proper approval workflows
- Service-to-service authentication: Secure communication between microservices
- Time-bound privileged access: Temporary elevated permissions for specific tasks
- Compliance and auditing: Meet regulatory requirements with detailed access logs
- Zero-downtime credential rotation: Update access without service interruption
How AWS Assume Role Works
- Trust relationship: The target role specifies which entities (principals) can assume it
- Permission check: The assuming entity must have permission to call the
sts:AssumeRoleaction - STS call: The entity calls the AssumeRole API with the role ARN and optional parameters
- Temporary credentials: STS returns temporary security credentials (access key, secret key, session token)
- Using credentials: Applications use these credentials to make AWS API calls with the role’s permissions
Enterprise-Grade Role Architecture Patterns
1. Hub-and-Spoke Model
Central Security Account (Hub)
├── Identity Management
├── Audit & Compliance
├── Emergency Access Roles
└── Cross-Account Trust Relationships
Spoke Accounts
├── Production Account
├── Development Account
├── Testing Account
└── Shared Services Account
Implementation Strategy:
- Central identity account manages all user identities
- Each spoke account trusts the hub account
- Role assumption flows through the hub for centralized auditing
- Consistent naming conventions across all accounts
2. Layered Security Model
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AssumeRoleWithMFA",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::CENTRAL-ACCOUNT:root"
},
"Action": "sts:AssumeRole",
"Condition": {
"Bool": {
"aws:MultiFactorAuthPresent": "true"
},
"NumericLessThan": {
"aws:MultiFactorAuthAge": "3600"
},
"StringEquals": {
"aws:PrincipalTag/Department": ["DevOps", "Security"],
"aws:RequestedRegion": ["us-west-2", "us-east-1"]
},
"IpAddress": {
"aws:SourceIp": ["203.0.113.0/24", "198.51.100.0/24"]
},
"StringLike": {
"aws:userid": "AIDAI*:${aws:username}"
}
}
}
]
}
3. Just-In-Time (JIT) Access Pattern
Automated Approval Workflow:
import boto3
import json
from datetime import datetime, timedelta
class JITAccessManager:
def __init__(self):
self.sts = boto3.client('sts')
self.iam = boto3.client('iam')
self.sns = boto3.client('sns')
def request_elevated_access(self, requestor, role_arn, duration_hours, justification):
"""Request temporary elevated access with approval workflow"""
# Create temporary policy for specific duration
temp_policy = {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {"AWS": f"arn:aws:iam::{self.get_account_id()}:user/{requestor}"},
"Action": "sts:AssumeRole",
"Resource": role_arn,
"Condition": {
"DateLessThan": {
"aws:CurrentTime": (datetime.utcnow() + timedelta(hours=duration_hours)).isoformat()
}
}
}
]
}
# Send approval request
approval_request = {
"requestor": requestor,
"role_arn": role_arn,
"duration": duration_hours,
"justification": justification,
"timestamp": datetime.utcnow().isoformat(),
"policy": temp_policy
}
self.sns.publish(
TopicArn='arn:aws:sns:region:account:jit-access-requests',
Message=json.dumps(approval_request),
Subject=f'JIT Access Request: {requestor} -> {role_arn}'
)
return approval_request
def approve_access_request(self, request_id, approver):
"""Approve and implement temporary access"""
# Implementation for approval workflow
pass
Advanced Automation with Infrastructure as Code
Terraform Module for Cross-Account Roles
# modules/cross-account-role/main.tf
variable "account_id" {
description = "Account ID that can assume this role"
type = string
}
variable "role_name" {
description = "Name of the role to create"
type = string
}
variable "policies" {
description = "List of policy ARNs to attach"
type = list(string)
default = []
}
variable "max_session_duration" {
description = "Maximum session duration in seconds"
type = number
default = 3600
}
variable "require_mfa" {
description = "Require MFA for role assumption"
type = bool
default = true
}
variable "allowed_principals" {
description = "List of principals allowed to assume this role"
type = list(string)
}
data "aws_iam_policy_document" "trust_policy" {
statement {
effect = "Allow"
principals {
type = "AWS"
identifiers = var.allowed_principals
}
actions = ["sts:AssumeRole"]
dynamic "condition" {
for_each = var.require_mfa ? [1] : []
content {
test = "Bool"
variable = "aws:MultiFactorAuthPresent"
values = ["true"]
}
}
condition {
test = "StringEquals"
variable = "aws:RequestedRegion"
values = ["us-west-2", "us-east-1"]
}
}
}
resource "aws_iam_role" "cross_account_role" {
name = var.role_name
assume_role_policy = data.aws_iam_policy_document.trust_policy.json
max_session_duration = var.max_session_duration
tags = {
ManagedBy = "terraform"
Purpose = "cross-account-access"
Environment = terraform.workspace
}
}
resource "aws_iam_role_policy_attachment" "policies" {
count = length(var.policies)
role = aws_iam_role.cross_account_role.name
policy_arn = var.policies[count.index]
}
# CloudTrail for auditing
resource "aws_cloudtrail" "role_audit" {
name = "${var.role_name}-audit-trail"
s3_bucket_name = aws_s3_bucket.audit_logs.bucket
event_selector {
read_write_type = "All"
include_management_events = true
data_resource {
type = "AWS::S3::Object"
values = ["arn:aws:s3:::${aws_s3_bucket.audit_logs.bucket}/*"]
}
}
insight_selector {
insight_type = "ApiCallRateInsight"
}
}
output "role_arn" {
description = "ARN of the created role"
value = aws_iam_role.cross_account_role.arn
}
AWS CLI Wrapper Script for Enhanced Security
Advanced Monitoring and Alerting
CloudWatch Dashboards for Role Usage
Advanced EventBridge Rules for Security Alerts
import boto3
import json
def create_security_monitoring():
events = boto3.client('events')
sns = boto3.client('sns')
# Rule for suspicious role assumptions
suspicious_pattern = {
"source": ["aws.sts"],
"detail-type": ["AWS API Call via CloudTrail"],
"detail": {
"eventSource": ["sts.amazonaws.com"],
"eventName": ["AssumeRole"],
"errorCode": {"exists": False},
"sourceIPAddress": {
"anything-but": {
"prefix": ["10.", "172.16.", "192.168."]
}
}
}
}
events.put_rule(
Name='SuspiciousRoleAssumption',
EventPattern=json.dumps(suspicious_pattern),
State='ENABLED',
Description='Alert on role assumptions from external IPs'
)
# Rule for failed role assumptions
failure_pattern = {
"source": ["aws.sts"],
"detail-type": ["AWS API Call via CloudTrail"],
"detail": {
"eventSource": ["sts.amazonaws.com"],
"eventName": ["AssumeRole"],
"errorCode": {"exists": True}
}
}
events.put_rule(
Name='FailedRoleAssumption',
EventPattern=json.dumps(failure_pattern),
State='ENABLED',
Description='Alert on failed role assumption attempts'
)
def lambda_security_handler(event, context):
"""Lambda function to process security events and send alerts"""
detail = event['detail']
event_name = detail.get('eventName')
source_ip = detail.get('sourceIPAddress')
user_identity = detail.get('userIdentity', {})
# Analyze the event
risk_score = calculate_risk_score(detail)
if risk_score > 70: # High risk threshold
send_security_alert(detail, risk_score)
# Optionally, automatically revoke the session
if risk_score > 90:
revoke_active_sessions(user_identity)
return {'statusCode': 200}
def calculate_risk_score(detail):
"""Calculate risk score based on various factors"""
score = 0
# Check source IP reputation
if is_suspicious_ip(detail.get('sourceIPAddress')):
score += 30
# Check time of access
if is_unusual_time(detail.get('eventTime')):
score += 20
# Check role sensitivity
role_arn = detail.get('requestParameters', {}).get('roleArn', '')
if 'Admin' in role_arn or 'Root' in role_arn:
score += 25
# Check user behavior anomaly
if is_anomalous_behavior(detail):
score += 25
return score
Detailed Example: Cross-Account EKS Access with Enhanced Security
The following example demonstrates how to use AssumeRole to grant Account A access to EKS resources in Account B with production-grade security controls.
Step 1: Create Advanced IAM Role in Account B (Target Account)
Create an IAM role with comprehensive security controls and conditions.
Enhanced Trust Policy with Multiple Security Layers:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "CrossAccountAssumeRole",
"Effect": "Allow",
"Principal": {
"AWS": [
"arn:aws:iam::123456789012:role/DevOpsTeamRole",
"arn:aws:iam::123456789012:role/SecurityTeamRole"
]
},
"Action": "sts:AssumeRole",
"Condition": {
"Bool": {
"aws:MultiFactorAuthPresent": "true"
},
"NumericLessThan": {
"aws:MultiFactorAuthAge": "1800"
},
"StringEquals": {
"aws:PrincipalTag/Department": ["DevOps", "Security"],
"aws:RequestedRegion": ["us-west-2", "us-east-1"],
"sts:ExternalId": "unique-external-id-2024"
},
"IpAddress": {
"aws:SourceIp": [
"203.0.113.0/24",
"198.51.100.0/24"
]
},
"DateGreaterThan": {
"aws:CurrentTime": "2024-01-01T00:00:00Z"
},
"DateLessThan": {
"aws:CurrentTime": "2025-12-31T23:59:59Z"
}
}
},
{
"Sid": "EmergencyAccess",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::123456789012:role/BreakGlassRole"
},
"Action": "sts:AssumeRole",
"Condition": {
"Bool": {
"aws:MultiFactorAuthPresent": "true"
},
"StringEquals": {
"aws:PrincipalTag/EmergencyAccess": "true"
}
}
}
]
}
Granular Permission Policy with Resource-Level Controls:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "EKSClusterManagement",
"Effect": "Allow",
"Action": [
"eks:DescribeCluster",
"eks:ListClusters",
"eks:DescribeNodegroup",
"eks:ListNodegroups",
"eks:DescribeUpdate",
"eks:ListUpdates"
],
"Resource": [
"arn:aws:eks:*:111122223333:cluster/prod-*",
"arn:aws:eks:*:111122223333:cluster/staging-*"
],
"Condition": {
"StringEquals": {
"aws:RequestedRegion": ["us-west-2", "us-east-1"]
}
}
},
{
"Sid": "EKSConfigurationUpdates",
"Effect": "Allow",
"Action": [
"eks:UpdateClusterConfig",
"eks:UpdateClusterVersion",
"eks:UpdateNodegroupConfig",
"eks:UpdateNodegroupVersion"
],
"Resource": [
"arn:aws:eks:*:111122223333:cluster/staging-*",
"arn:aws:eks:*:111122223333:nodegroup/staging-*/*/*"
],
"Condition": {
"StringEquals": {
"aws:RequestedRegion": ["us-west-2"],
"aws:PrincipalTag/Role": "DevOps"
},
"Bool": {
"aws:MultiFactorAuthPresent": "true"
}
}
},
{
"Sid": "ProductionReadOnly",
"Effect": "Allow",
"Action": [
"eks:DescribeCluster",
"eks:ListClusters",
"eks:DescribeNodegroup",
"eks:ListNodegroups"
],
"Resource": [
"arn:aws:eks:*:111122223333:cluster/prod-*"
],
"Condition": {
"StringEquals": {
"aws:PrincipalTag/ProductionAccess": "read-only"
}
}
},
{
"Sid": "CloudWatchLogs",
"Effect": "Allow",
"Action": [
"logs:DescribeLogGroups",
"logs:DescribeLogStreams",
"logs:GetLogEvents",
"logs:FilterLogEvents"
],
"Resource": [
"arn:aws:logs:*:111122223333:log-group:/aws/eks/*"
]
}
]
}
Permission Boundary for Additional Security:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "PermissionBoundary",
"Effect": "Allow",
"Action": [
"eks:*",
"ec2:DescribeInstances",
"ec2:DescribeSecurityGroups",
"ec2:DescribeSubnets",
"ec2:DescribeVpcs",
"iam:ListRoles",
"iam:PassRole",
"logs:*"
],
"Resource": "*",
"Condition": {
"StringEquals": {
"aws:RequestedRegion": ["us-west-2", "us-east-1"]
}
}
},
{
"Sid": "DenyDangerousActions",
"Effect": "Deny",
"Action": [
"eks:DeleteCluster",
"eks:DeleteNodegroup",
"iam:DeleteRole",
"iam:DeletePolicy",
"iam:DetachRolePolicy"
],
"Resource": "*",
"Condition": {
"StringNotEquals": {
"aws:PrincipalTag/CanDelete": "true"
}
}
}
]
}
Step 2: Create IAM Policy in Account A (Source Account)
Create and attach an IAM policy to the users or roles in Account A that need to assume the role in Account B.
Example Policy (in Account A):
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "sts:AssumeRole",
"Resource": "arn:aws:iam::111122223333:role/EKSAdminRole",
"Condition": {
"StringLike": {
"aws:RequestedRegion": [
"us-west-2",
"us-east-1"
]
}
}
}
]
}
Step 3: Assume Role from Account A
A user or service in Account A can now assume the role in Account B using the AWS CLI, SDK, or AWS console.
Using AWS CLI:
This command returns a JSON object containing:
AccessKeyIdSecretAccessKeySessionTokenExpirationtimestamp
Using AWS SDK (Python example):
import boto3
# Create an STS client
sts_client = boto3.client('sts')
# Assume the role
assumed_role = sts_client.assume_role(
RoleArn='arn:aws:iam::111122223333:role/EKSAdminRole',
RoleSessionName='EKSAdminSession',
DurationSeconds=3600 # 1 hour
)
# Extract the temporary credentials
credentials = assumed_role['Credentials']
# Create an EKS client using the temporary credentials
eks_client = boto3.client(
'eks',
region_name='us-west-2',
aws_access_key_id=credentials['AccessKeyId'],
aws_secret_access_key=credentials['SecretAccessKey'],
aws_session_token=credentials['SessionToken']
)
# Now you can make EKS API calls
clusters = eks_client.list_clusters()
print(clusters)
Step 4: Use Temporary Credentials for Access
These temporary credentials can be used to access EKS resources in Account B. Here’s an example of updating your kubeconfig:
You can also create a shell profile that automatically assumes the role:
# Add to your ~/.bash_profile or ~/.zshrc
function assume-eks-role() {
output=$(aws sts assume-role --role-arn arn:aws:iam::111122223333:role/EKSAdminRole --role-session-name EKSSession)
export AWS_ACCESS_KEY_ID=$(echo $output | jq -r '.Credentials.AccessKeyId')
export AWS_SECRET_ACCESS_KEY=$(echo $output | jq -r '.Credentials.SecretAccessKey')
export AWS_SESSION_TOKEN=$(echo $output | jq -r '.Credentials.SessionToken')
echo "Temporary credentials set for EKS admin role"
}
What is sts:AssumeRoleWithWebIdentity?
The
sts:AssumeRoleWithWebIdentityoperation allows you to obtain temporary AWS credentials by using an OpenID Connect (OIDC) token or SAML 2.0 assertion from an external identity provider.
This mechanism enables federating AWS access with external identity systems without requiring AWS IAM users for each identity.
Key Benefits
- No IAM users needed: Eliminates the need to create IAM users for each external identity
- Centralized identity management: Use your existing identity provider
- Zero IAM credentials: No long-term AWS credentials to manage or rotate
- Auditable access: All access is logged in AWS CloudTrail with the original identity information
Common Use Cases
- GitHub Actions: Authenticate GitHub workflows to access AWS resources
- Kubernetes Service Accounts: Allow pods to access AWS services securely
- Web/Mobile Applications: Allow authenticated application users to access AWS resources directly
- Enterprise SSO: Enable employees to access AWS using their corporate credentials
- Self-developed applications: Authenticate custom applications with your own OIDC provider
Process Flow
- OIDC Provider Configuration: Register an OIDC provider in IAM and create a role with a trust policy
- Identity Authentication: User/service authenticates with the external IdP and receives an OIDC token
- AWS API Call: Application calls
AssumeRoleWithWebIdentityAPI with the OIDC token - Token Verification: AWS verifies the token with the configured OIDC provider
- Temporary Credentials: Upon successful verification, AWS issues temporary credentials
Example: GitHub Actions Integration
IAM OIDC Provider Configuration:
aws iam create-open-id-connect-provider --url https://token.actions.githubusercontent.com --client-id-list sts.amazonaws.com --thumbprint-list 6938fd4d98bab03faadb97b34396831e3780aea1
Role Trust Policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Federated": "arn:aws:iam::ACCOUNT_ID:oidc-provider/token.actions.githubusercontent.com"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringEquals": {
"token.actions.githubusercontent.com:aud": "sts.amazonaws.com",
"token.actions.githubusercontent.com:sub": "repo:your-org/your-repo:ref:refs/heads/main"
}
}
}
]
}
GitHub Actions Workflow:
jobs:
deploy:
runs-on: ubuntu-latest
permissions:
id-token: write
contents: read
steps:
- name: Configure AWS credentials
uses: aws-actions/configure-aws-credentials@v1
with:
role-to-assume: arn:aws:iam::ACCOUNT_ID:role/GitHubActionsRole
aws-region: us-east-1
- name: Deploy infrastructure
run: aws cloudformation deploy --template-file template.yaml --stack-name my-stack
Comparison: AssumeRole vs AssumeRoleWithWebIdentity vs AssumeRoleWithSAML
Authentication:
- sts:AssumeRole: AWS IAM credentials
- sts:AssumeRoleWithWebIdentity: OIDC token
- sts:AssumeRoleWithSAML: SAML 2.0 assertion
Identity Source:
- sts:AssumeRole: AWS IAM
- sts:AssumeRoleWithWebIdentity: External OIDC providers (Google, GitHub, etc.)
- sts:AssumeRoleWithSAML: SAML IdPs (Active Directory, Okta, etc.)
Primary Use Cases:
- sts:AssumeRole: Cross-account access, delegation within AWS
- sts:AssumeRoleWithWebIdentity: Mobile/web apps, CI/CD pipelines, Kubernetes
- sts:AssumeRoleWithSAML: Enterprise SSO, workforce identity federation
Required Setup:
- sts:AssumeRole: IAM roles and policies
- sts:AssumeRoleWithWebIdentity: OIDC provider + IAM role
- sts:AssumeRoleWithSAML: SAML provider + IAM role
Credential Duration:
- sts:AssumeRole: 15 min - 12 hours
- sts:AssumeRoleWithWebIdentity: 15 min - 12 hours
- sts:AssumeRoleWithSAML: 15 min - 12 hours
Common Examples:
- sts:AssumeRole: AWS CLI, AWS console
- sts:AssumeRoleWithWebIdentity: GitHub Actions, Kubernetes ServiceAccounts
- sts:AssumeRoleWithSAML: AWS Console login via corporate SSO
Advanced Best Practices for Enterprise AWS Assume Role
1. Security Architecture:
- Implement defense-in-depth with multiple conditional layers
- Use permission boundaries to limit maximum permissions
- Enforce MFA with time-based conditions (MFA age < 30 minutes)
- Implement IP allowlisting and geographic restrictions
- Use external IDs for third-party access to prevent confused deputy attacks
- Implement role chaining limits and session duration policies
- Use Infrastructure as Code (Terraform/CloudFormation) for consistent role deployment
- Implement automated role lifecycle management
- Create self-service portals for role requests with approval workflows
- Establish break-glass procedures with proper audit trails
- Implement just-in-time (JIT) access with time-bound permissions
- Use AWS Config rules to monitor role configuration drift
- Enable comprehensive CloudTrail logging with log file validation
- Implement real-time alerting for suspicious role assumption patterns
- Use AWS GuardDuty for behavioral analysis and threat detection
- Create custom CloudWatch metrics for role usage analytics
- Implement automated compliance checks with AWS Security Hub
- Use IAM Access Analyzer for unused and over-privileged role detection
- Establish role naming conventions and tagging strategies
- Implement regular access reviews and role audits
- Use AWS Organizations SCPs as guardrails
- Create role templates for common use cases
- Implement risk-based access controls with conditional policies
- Establish incident response procedures for compromised roles
- Implement credential caching to reduce STS API calls
- Use regional STS endpoints for reduced latency
- Implement retry logic with exponential backoff
- Monitor STS API throttling and adjust application behavior
- Use session tags for enhanced authorization decisions
- Implement efficient credential refresh mechanisms
Enterprise Role Patterns and Anti-Patterns
Recommended Patterns
1. Principle of Least Privilege with Session Policies:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::my-bucket/user-${aws:userid}/*"
}
]
}
2. Time-Based Access Controls:
{
"Condition": {
"DateGreaterThan": {
"aws:CurrentTime": "2024-01-01T09:00:00Z"
},
"DateLessThan": {
"aws:CurrentTime": "2024-01-01T17:00:00Z"
},
"ForAllValues:StringEquals": {
"aws:RequestedRegion": ["us-west-2"]
}
}
}
3. Emergency Access Pattern:
def create_emergency_access_role():
"""Create break-glass role with temporary elevated permissions"""
trust_policy = {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {"AWS": f"arn:aws:iam::{ACCOUNT_ID}:role/EmergencyAccessRole"},
"Action": "sts:AssumeRole",
"Condition": {
"Bool": {"aws:MultiFactorAuthPresent": "true"},
"StringEquals": {"aws:PrincipalTag/EmergencyAccess": "approved"},
"NumericLessThan": {"aws:MultiFactorAuthAge": "900"} # 15 minutes
}
}
]
}
# Create role with temporary permissions
# Automatically expire after 2 hours
Anti-Patterns to Avoid
1. Overly Permissive Trust Policies:
// DON'T DO THIS
{
"Effect": "Allow",
"Principal": {"AWS": "*"},
"Action": "sts:AssumeRole"
}
2. Long-Lived Sessions Without Conditions:
// DON'T DO THIS
{
"Effect": "Allow",
"Principal": {"AWS": "arn:aws:iam::123456789012:root"},
"Action": "sts:AssumeRole"
// No conditions = unlimited access
}
3. Credential Hardcoding:
# DON'T DO THIS
AWS_ACCESS_KEY_ID = "AKIA..."
AWS_SECRET_ACCESS_KEY = "secret..."
# DO THIS INSTEAD
credentials = sts_client.assume_role(...)
Advanced Troubleshooting and Diagnostics
1. Access Denied Issues (Enhanced Diagnostics):
- Use AWS CLI with --debug flag to see detailed API responses
- Check CloudTrail for specific error codes and failure reasons
- Validate all condition keys in trust policies
- Test with AWS IAM Policy Simulator for permission validation
- Verify external ID requirements and case sensitivity
- Check for typos in role ARNs and account IDs
- Monitor credential expiration with automated renewal
- Implement exponential backoff for STS API rate limiting
- Handle token refresh gracefully in long-running applications
- Use AWS SDKs' built-in credential providers when possible
- Implement circuit breakers for STS endpoint failures
- Validate OIDC provider thumbprint matches current certificate
- Check token claims structure and required audience values
- Verify clock synchronization between systems
- Test token validation with online JWT decoders
- Monitor for certificate rotation and update schedules
- Implement caching strategies for frequently used credentials
- Use regional STS endpoints to reduce latency
- Monitor STS API quotas and request patterns
- Implement health checks for role assumption workflows
- Use CloudWatch metrics to track assumption success rates
- Create runbooks for compromised role scenarios
- Implement automated session revocation capabilities
- Set up real-time alerting for anomalous access patterns
- Use AWS Config to detect unauthorized role modifications
- Maintain audit trails for forensic analysis
Production-Ready Code Examples
Advanced Session Management Class
import boto3
import json
import time
from datetime import datetime, timedelta
from botocore.exceptions import ClientError, BotoCoreError
import logging
from typing import Dict, Optional, Any
import threading
from dataclasses import dataclass
@dataclass
class AssumeRoleConfig:
role_arn: str
session_name: str
duration_seconds: int = 3600
external_id: Optional[str] = None
session_policy: Optional[str] = None
mfa_serial: Optional[str] = None
region: str = 'us-east-1'
class EnhancedSTSManager:
"""Enterprise-grade STS session manager with caching and error handling"""
def __init__(self):
self.logger = logging.getLogger(__name__)
self._sessions: Dict[str, Dict[str, Any]] = {}
self._lock = threading.RLock()
self.sts_client = boto3.client('sts')
def assume_role(self, config: AssumeRoleConfig, mfa_token: Optional[str] = None) -> Dict[str, Any]:
"""Assume role with comprehensive error handling and caching"""
cache_key = self._generate_cache_key(config)
with self._lock:
# Check cache first
if self._is_cached_session_valid(cache_key):
self.logger.info(f"Using cached credentials for {config.role_arn}")
return self._sessions[cache_key]['credentials']
try:
credentials = self._perform_assume_role(config, mfa_token)
self._cache_session(cache_key, credentials)
return credentials
except ClientError as e:
self._handle_client_error(e, config)
raise
except Exception as e:
self.logger.error(f"Unexpected error assuming role: {str(e)}")
raise
def _perform_assume_role(self, config: AssumeRoleConfig, mfa_token: Optional[str] = None) -> Dict[str, Any]:
"""Perform the actual assume role operation with retry logic"""
assume_role_params = {
'RoleArn': config.role_arn,
'RoleSessionName': config.session_name,
'DurationSeconds': config.duration_seconds
}
# Add optional parameters
if config.external_id:
assume_role_params['ExternalId'] = config.external_id
if config.session_policy:
assume_role_params['Policy'] = config.session_policy
if config.mfa_serial and mfa_token:
assume_role_params['SerialNumber'] = config.mfa_serial
assume_role_params['TokenCode'] = mfa_token
# Retry logic with exponential backoff
max_retries = 3
base_delay = 1
for attempt in range(max_retries):
try:
response = self.sts_client.assume_role(**assume_role_params)
# Enhance credentials with metadata
credentials = response['Credentials']
credentials['AssumedRoleUser'] = response['AssumedRoleUser']
credentials['PackedPolicySize'] = response.get('PackedPolicySize', 0)
self.logger.info(f"Successfully assumed role: {config.role_arn}")
return credentials
except ClientError as e:
error_code = e.response['Error']['Code']
if error_code in ['Throttling', 'RequestLimitExceeded'] and attempt < max_retries - 1:
delay = base_delay * (2 ** attempt)
self.logger.warning(f"Rate limited, retrying in {delay} seconds...")
time.sleep(delay)
continue
else:
raise
def _handle_client_error(self, error: ClientError, config: AssumeRoleConfig):
"""Provide detailed error analysis and suggestions"""
error_code = error.response['Error']['Code']
error_message = error.response['Error']['Message']
troubleshooting_guide = {
'AccessDenied': "Check trust policy, ensure calling identity has sts:AssumeRole permission",
'InvalidParameterValue': "Verify role ARN format and account ID",
'MalformedPolicyDocument': "Review session policy JSON syntax",
'TokenRefreshRequired': "MFA token expired, obtain new token",
'RegionDisabledException': "STS not available in requested region"
}
suggestion = troubleshooting_guide.get(error_code, "Check AWS documentation for error code")
self.logger.error(f"AssumeRole failed: {error_code} - {error_message}")
self.logger.error(f"Suggestion: {suggestion}")
self.logger.error(f"Role ARN: {config.role_arn}")
def _generate_cache_key(self, config: AssumeRoleConfig) -> str:
"""Generate unique cache key for session"""
return f"{config.role_arn}:{config.session_name}:{config.duration_seconds}"
def _is_cached_session_valid(self, cache_key: str) -> bool:
"""Check if cached session is still valid"""
if cache_key not in self._sessions:
return False
session = self._sessions[cache_key]
expiration = datetime.fromisoformat(session['credentials']['Expiration'].replace('Z', '+00:00'))
# Consider session valid if more than 5 minutes remaining
return datetime.now(expiration.tzinfo) < (expiration - timedelta(minutes=5))
def _cache_session(self, cache_key: str, credentials: Dict[str, Any]):
"""Cache session credentials"""
self._sessions[cache_key] = {
'credentials': credentials,
'cached_at': datetime.utcnow()
}
def get_session_info(self, cache_key: str) -> Optional[Dict[str, Any]]:
"""Get information about cached session"""
with self._lock:
if cache_key in self._sessions:
session = self._sessions[cache_key]
return {
'cached_at': session['cached_at'],
'expires_at': session['credentials']['Expiration'],
'assumed_role_arn': session['credentials']['AssumedRoleUser']['Arn']
}
return None
def revoke_session(self, cache_key: str):
"""Manually revoke cached session"""
with self._lock:
if cache_key in self._sessions:
del self._sessions[cache_key]
self.logger.info(f"Revoked cached session: {cache_key}")
# Usage example
def main():
manager = EnhancedSTSManager()
config = AssumeRoleConfig(
role_arn='arn:aws:iam::111122223333:role/EKSAdminRole',
session_name=f'enhanced-session-{int(time.time())}',
duration_seconds=3600,
external_id='unique-external-id-2024'
)
try:
credentials = manager.assume_role(config, mfa_token='123456')
# Use credentials to create service clients
eks_client = boto3.client(
'eks',
aws_access_key_id=credentials['AccessKeyId'],
aws_secret_access_key=credentials['SecretAccessKey'],
aws_session_token=credentials['SessionToken'],
region_name='us-west-2'
)
# Your EKS operations here
clusters = eks_client.list_clusters()
print(f"Found {len(clusters['clusters'])} EKS clusters")
except Exception as e:
logging.error(f"Failed to assume role: {str(e)}")
if __name__ == "__main__":
logging.basicConfig(level=logging.INFO)
main()
Reference and Additional Resources
- AWS STS Documentation
- AWS Cross-Account Access Guide
- AWS IAM Role Delegation
- AWS AssumeRole Deep Dive
- OIDC Federation with AWS
- GitHub OIDC Integration with AWS
- AWS Security Token Service Best Practices
- AWS IAM Policy Simulator
- AWS CloudTrail User Guide
- AWS Config Rules for IAM
Enterprise Adoption Checklist
Phase 1: Foundation (Weeks 1-2)
☐ Establish AWS Organizations structure
☐ Define role naming conventions and tagging strategy
☐ Create central identity account (hub-and-spoke model)
☐ Enable CloudTrail in all accounts
☐ Set up basic cross-account roles
Phase 2: Security Hardening (Weeks 3-4)
☐ Implement MFA requirements for all role assumptions
☐ Add IP restrictions and geographic controls
☐ Deploy permission boundaries
☐ Configure AWS Config rules for compliance
☐ Set up CloudWatch alarms for suspicious activities
Phase 3: Automation (Weeks 5-6)
☐ Deploy Infrastructure as Code for role management
☐ Implement automated compliance checking
☐ Create self-service role request portal
☐ Set up just-in-time access workflows
☐ Deploy credential caching solutions
Phase 4: Advanced Features (Weeks 7-8)
☐ Implement break-glass procedures
☐ Deploy advanced monitoring and alerting
☐ Create emergency response runbooks
☐ Establish regular access review processes
☐ Integrate with existing identity providers
Ongoing Maintenance
☐ Regular role and permission audits
☐ Security awareness training for teams
☐ Performance monitoring and optimization
☐ Threat model updates and security reviews
☐ Documentation and procedure updates

Comments