4 min to read
Memory Layout in C/C++ - A Developer's Refresher
Understanding memory management for better debugging and optimization
Overview
Understanding how memory is arranged and managed internally when writing and executing programs is crucial not only for performance optimization but also for preventing bugs and improving debugging capabilities.
Particularly for developers working with C/C++, Rust, or low-level system programming, accurately identifying and tracking issues such as pointer errors, segmentation faults, and memory leaks is essential.
In this article, we’ll examine process memory structure from a system perspective, explore the differences between Stack and Heap memory, and summarize common bug scenarios and memory debugging tools encountered in practical development.
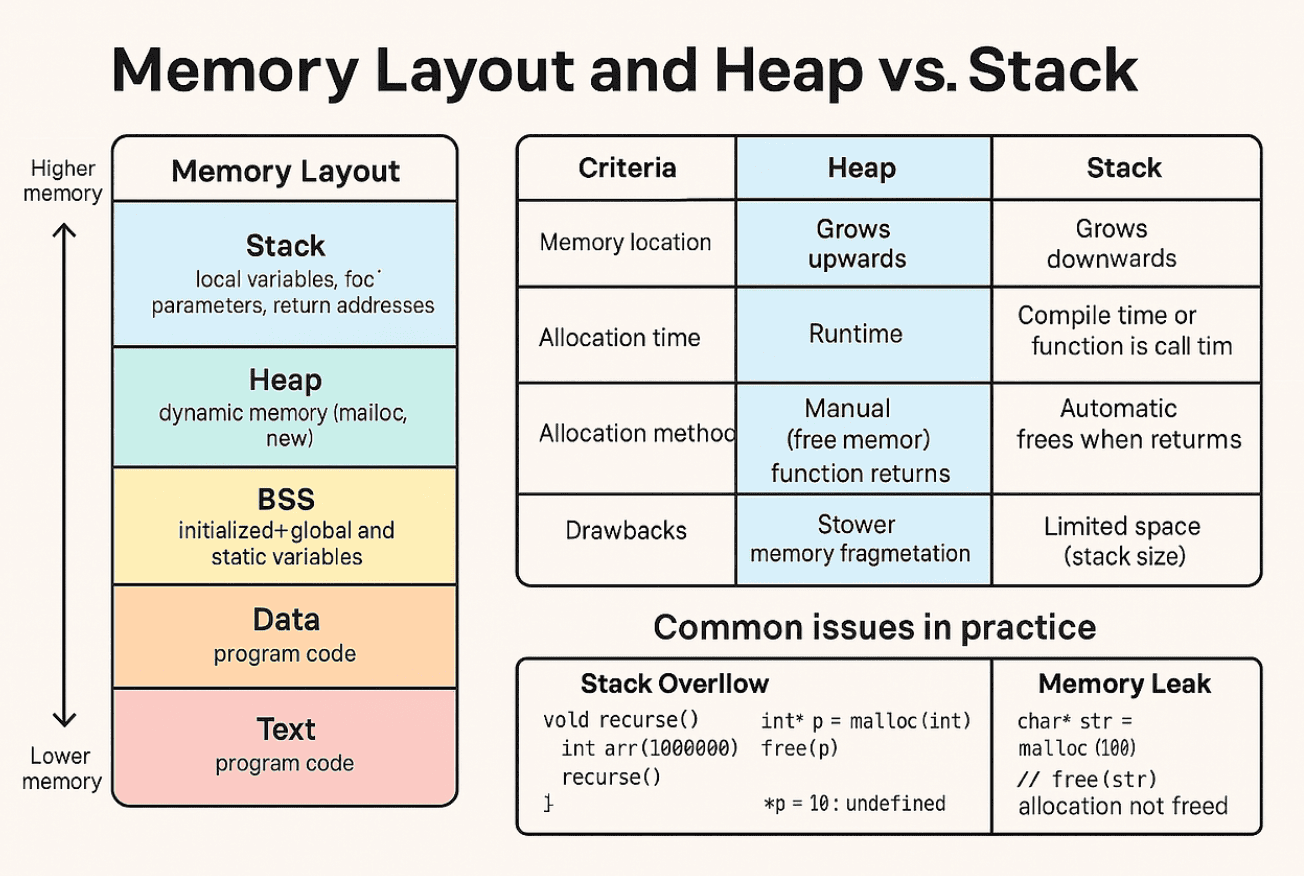
Memory Layout
When a C/C++ program is executed, the operating system allocates memory to each process, dividing it into the following regions:
Text Segment (Code Segment)
- Stores the executable program code
- Usually read-only with execution permissions
Data Segment
- Stores initialized global variables and static variables
BSS Segment
- Stores uninitialized global variables and static variables
Heap Segment
- Used for dynamic memory allocation via malloc, new, etc.
- Size can be adjusted during runtime
Stack Segment
- Stores local variables, parameters, return addresses during function calls
- Last-In-First-Out (LIFO) structure
Stack vs Heap
| Characteristic | Stack | Heap |
|---|---|---|
| Memory Growth | Grows from lower to higher addresses | Grows from higher to lower addresses |
| Allocation Time | Compile time or function call time | Runtime |
| Allocation Method | Automatic (allocated/deallocated on function call/return) | Manual (developer must explicitly free) |
| Speed | Fast | Slow |
| Size Limitation | Relatively small | Relatively large |
| Leak Possibility | Almost none | Possible memory leaks |
Real-world Examples
Stack Overflow
Occurs when recursion has incorrect termination conditions or when declaring excessively large local arrays:
void recurse() {
int arr[1000000]; // Stack space shortage
recurse();
}
Use After Free
A mistake where memory is used after it has been freed:
int* p = malloc(sizeof(int));
free(p);
*p = 10; // Undefined behavior
Memory Leak
Situation where memory continuously consumes resources because it’s allocated but never freed:
char* str = malloc(100);
// str is used but free() is omitted → leak occurs
Dangling Pointer
Incorrectly using a pointer that references deallocated memory.
Memory Debugging Tips
- valgrind: Detects runtime memory errors and leaks
- gdb: Inspects stack frames and pointer addresses
- ASAN (AddressSanitizer): Clang/LLVM-based memory error detection tool
Dynamic Memory Reallocation (realloc)
realloc() is used to dynamically change the size of an already allocated memory block.
However, since the pointer returned by realloc() may differ from the original pointer, it’s essential to always replace the original pointer:
char *data = malloc(10);
data = realloc(data, 100); // Must overwrite with return value
Caution with Stack Memory in Functions
Returning the address of a local array can cause Dangling Pointer issues:
char* dangerous() {
char temp[100];
return temp; // temp disappears when function ends
}
Heap Fragmentation
When many malloc()/free() calls repeat, empty spaces in heap memory can become fragmented, making it impossible to allocate large blocks even when the total available space is sufficient.
Solutions: Memory pools, garbage collection, slab allocator
Modern C++ RAII Pattern
The modern C++ style is to use smart pointers (std::unique_ptr, std::shared_ptr) rather than directly managing memory with new/delete:
std::unique_ptr<int> ptr = std::make_unique<int>(10); // Automatic cleanup
Conclusion
Stack and Heap go beyond simple storage location differences, being deeply connected to a program’s execution structure and resource management strategy.
Especially for developers working with manually managed memory languages like C/C++, the ability to prevent and debug memory issues such as Stack Overflow, memory leaks, and Use After Free is essential.
While operating systems and compilers provide increasingly more protective measures, many bugs and security vulnerabilities still arise from memory issues.
Therefore, it’s important to adopt practices such as:
- Always being careful not to omit free() or delete
- Initializing memory before use and releasing it after
- Actively utilizing debugging tools (valgrind, gdb, ASAN, etc.)
Stable systems are built upon invisible memory foundations.

Comments